Operational Technology (OT) Security Education teaches a different rhythm of security—one where “just patch it now” is often the wrong reflex. The diagram shows why. Learners bring in inputs such as foundational knowledge and training resources, but OT learning is shaped by strong controls: industrial regulations and safety policies that treat stability, uptime, and human safety as first principles. Mechanisms like expert-led labs and OT security tooling let students practice realistic decisions: segmenting networks without disrupting control loops, monitoring quietly without adding fragility, designing access so maintenance is possible without turning every engineer into an administrator, and planning incident response when “shut it down” may be the most dangerous option. The output is practical judgment—learners who can protect systems that run factories, utilities, transport, and critical infrastructure, balancing cybersecurity needs with the uncompromising demands of safety and continuous operation.
This IDEF0 (Input–Control–Output–Mechanism) diagram summarizes Operational Technology (OT) Security Education as a structured transformation. Inputs include training materials and learner knowledge of industrial systems and basic security concepts. Controls include industrial regulations, safety policies, standards, and governance requirements that constrain what can be changed and how risk is managed in OT environments. Mechanisms include instructors, experts, OT security tools, lab environments, and realistic scenarios involving PLCs, SCADA concepts, segmentation, monitoring, and incident handling. Outputs include learners who develop OT protection skills—able to prioritize safety, understand operational constraints, and apply security measures that fit the realities of industrial reliability and uptime.
Operational Technology (OT) Security is a specialized field of cybersecurity focused on protecting systems that manage industrial operations—such as power plants, water treatment facilities, and manufacturing lines. Unlike IT environments that prioritize data, OT systems control physical processes, making their failure or compromise potentially catastrophic. As digital connectivity expands, the convergence of IT and OT increases exposure to cyber threats, necessitating robust and tailored defense mechanisms.
One critical aspect of OT security is managing the interface between industrial systems and cloud infrastructure. As cloud security becomes central to infrastructure management, secure integration with OT systems is essential. At the same time, advanced monitoring tools using AI and ML in cybersecurity can detect subtle anomalies in operational data streams, helping to identify threats before they escalate.
The challenges of securing OT environments are intensified by legacy systems that were not designed with modern security principles in mind. Here, fundamental disciplines like cryptography and identity and access management must be adapted to work reliably within the real-time constraints of industrial networks. Preventing unauthorized access to control systems is as important as educating personnel through cybersecurity awareness programs that address both digital hygiene and operational safety.
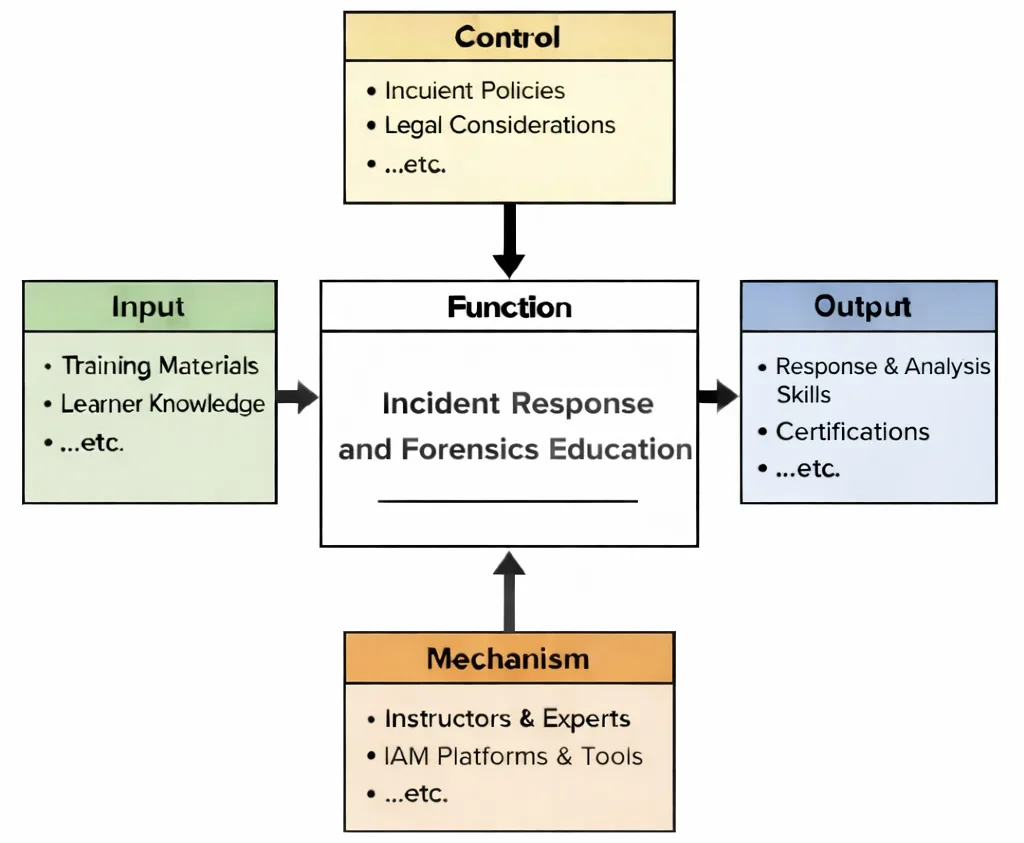
When threats breach defenses, timely incident response and forensics ensure that disruptions are minimized and vulnerabilities are identified. Industrial forensics requires deep understanding of process control logic and sensor networks, overlapping with domains such as CPS security. In highly regulated sectors, compliance and governance are shaped by robust cybersecurity policies tailored to operational risk.
Network segmentation and real-time monitoring play a central role in network security for OT systems. They are supported by application security techniques adapted to industrial software and hardware. To proactively identify system weaknesses, organizations often employ ethical hacking strategies, simulating attacks in controlled environments.
The rise of emerging areas in cybersecurity further expands the threat landscape for OT, with sophisticated attacks now targeting critical infrastructure. Integrating threat intelligence feeds allows teams to detect attack trends and adjust defenses accordingly. These insights are increasingly refined using data analysis and visualization tools to make complex patterns more interpretable.
OT Security also benefits from broader data science and analytics applications, which aggregate sensor data and system logs for deeper insights. Supporting techniques such as data cleaning and preprocessing help improve the quality of these insights, while data collection and storage mechanisms provide long-term visibility over equipment behavior. Using advanced tools and technologies, professionals are equipped to automate responses and maintain operational continuity.
As industrial systems evolve, they increasingly rely on domain-specific analytics to detect unusual process behavior, adding another layer of protection. However, implementing these technologies must also consider ethical and social aspects, particularly when automation decisions impact safety or employment. OT Security is therefore not just a technical challenge, but also a multidimensional discipline with operational, societal, and economic implications.
With its convergence of industrial control and cyber defense, Operational Technology Security is central to safeguarding the systems that sustain modern civilization. As technologies advance and threats evolve, this domain demands continuous learning, cross-disciplinary collaboration, and strategic foresight to ensure resilient and secure operations.

This image depicts OT security as the protective layer around real-world industrial operations. On the left, factory towers, tanks, and process equipment represent physical infrastructure controlled by sensors and automated systems. In the center, a large shield with a padlock signals secure control of critical assets, while the surrounding network lines suggest interconnected controllers, HMIs, and field devices. On the right, screens and control-room consoles symbolize monitoring, alarms, and operational oversight, and the presence of power lines highlights links to critical utilities. Small warning triangles and alert symbols convey the risk of disruptions—from cyber intrusions to unsafe system changes. Overall, the picture communicates that OT security is about keeping industrial systems safe, reliable, and resilient while they continue running in real time.
What is OT security and how is it different from traditional IT security?
OT security refers to the protection of operational technology systems such as industrial control systems (ICS), SCADA systems, PLCs, and other devices that monitor and control physical processes in factories, utilities, transportation, and critical infrastructure. It differs from traditional IT security because OT systems are tightly linked to real-world equipment, safety, and uptime, so changes that might be routine in IT can be risky in OT. In OT environments, priorities often follow the order of safety and availability first, followed by integrity and confidentiality, whereas IT security usually emphasises confidentiality, integrity, and availability. Understanding OT security requires both cybersecurity knowledge and a basic grasp of engineering systems, industrial processes, and safety requirements.
Why is OT security important for critical infrastructure and industrial systems?
OT security is important because industrial and critical infrastructure systems control essential services such as power, water, manufacturing, transport, and building automation. A successful cyberattack on these systems can cause physical damage to equipment, production downtime, safety incidents, environmental harm, or disruption of public services. As OT networks become more connected to IT systems and the internet, attackers gain more pathways to reach control systems that were once isolated. Securing OT helps organisations protect human safety, maintain regulatory compliance, avoid costly outages, and preserve public trust in essential services.
What are some common cyber threats to OT environments and industrial control systems?
Common cyber threats to OT environments include malware and ransomware that target industrial systems, phishing campaigns that compromise operator accounts, and remote access abuse through poorly secured VPNs or remote desktop tools. Attackers may exploit unpatched vulnerabilities in PLCs, HMIs, engineering workstations, or Windows servers that sit at the boundary between IT and OT networks. Misconfigurations, weak passwords, and shared accounts are frequent weaknesses in control system environments. In more advanced cases, adversaries may attempt to modify setpoints, disable safety systems, or subtly manipulate sensor data to cause unsafe or inefficient operation without immediate detection.
How does network segmentation help improve OT security?
Network segmentation improves OT security by dividing the overall environment into zones and conduits with controlled communication paths between them. In a typical design, business IT networks, demilitarised zones (DMZs), and OT control networks are separated with firewalls and strictly defined rules for what traffic is allowed. This structure limits the spread of malware or an intruder from office systems into sensitive control networks, and helps ensure that only essential protocols and services are exposed across boundaries. Segmentation also supports monitoring, because security teams can place sensors and logging points at key chokepoints to detect anomalous traffic moving between zones.
What security controls are commonly used to protect OT systems and devices?
Common security controls for OT systems include network segmentation, firewalls, and intrusion detection systems tuned for industrial protocols such as Modbus, DNP3, or PROFINET. Organisations also use strict access control for engineering workstations and control rooms, including multifactor authentication, role-based access, and locked cabinets or enclosures for critical hardware. Hardening measures such as disabling unused services, enforcing secure remote access methods, and applying carefully tested patches are important, even when patching must be scheduled to avoid production disruption. Continuous monitoring, security logging, and incident response procedures adapted to OT environments help detect and respond to abnormal activity while respecting operational and safety constraints.
How do standards and frameworks such as IEC 62443 support OT security?
Standards and frameworks such as IEC 62443, NIST guidance, and sector-specific regulations provide structured approaches for improving OT security. IEC 62443, for example, describes security requirements for control system components, system-level architectures, and organisational processes, including concepts like security zones, conduits, and security levels. These documents help asset owners, integrators, and vendors align on common terminology and baseline expectations, making it easier to design, procure, and operate secure industrial systems. For students, learning these frameworks offers a roadmap for how technical controls, governance, and lifecycle management come together in real industrial cybersecurity projects.
What challenges do organisations face when securing legacy OT systems?
Organisations often face significant challenges when securing legacy OT systems because many were designed decades ago without modern cybersecurity in mind. These systems may run outdated operating systems, support only weak authentication, and cannot easily be patched or restarted without disrupting production. Vendors may no longer support the equipment or may require long maintenance windows for updates, leading to delayed remediation of vulnerabilities. To manage these constraints, security teams rely on compensating controls such as strict network isolation, carefully managed remote access, enhanced monitoring, and detailed procedures that balance safety, uptime, and security requirements.
What skills and knowledge are useful for students interested in OT security careers?
Students interested in OT security careers benefit from a mix of cybersecurity fundamentals, networking knowledge, and basic understanding of industrial control concepts. Useful topics include network architecture, firewalls, industrial protocols, security monitoring, and incident response, together with awareness of safety systems, control loops, and physical process behaviour. Hands-on practice with simulation tools, lab environments, or entry-level roles in industrial operations and maintenance can help bridge the gap between theory and real plant conditions. Strong communication skills are also important, because OT security professionals must collaborate with engineers, operators, and management to design controls that respect safety, reliability, and production goals.
Table of Contents
Key Topics in OT Security
Protecting Critical Infrastructure:
- What It Includes:
- Infrastructure critical to national and public safety, such as energy grids, water systems, transportation networks, and healthcare facilities.
- Threats:
- Nation-state cyberattacks targeting power grids (e.g., the 2015 Ukraine power grid attack).
- Ransomware shutting down critical systems, as seen in the Colonial Pipeline attack.
- Security Measures:
- Implementing segmentation to isolate critical systems from less secure networks.
- Using advanced threat detection tools for real-time monitoring.
- Enforcing strict access controls to prevent unauthorized entry.
- Applications:
- Monitoring and protecting Supervisory Control and Data Acquisition (SCADA) systems that manage energy distribution.
- What It Includes:
Securing Industrial Control Systems (ICS):
- What They Are:
- Systems used in industrial processes to monitor and control equipment and operations.
- Examples: SCADA systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs).
- Threats:
- Malware like Stuxnet specifically designed to sabotage ICS operations.
- Insider threats, including intentional or accidental misconfigurations.
- Security Strategies:
- Network Segmentation:
- Divide IT and OT networks to minimize attack surfaces.
- Patch Management:
- Regularly update ICS software and firmware to mitigate known vulnerabilities.
- Incident Response:
- Develop OT-specific response plans for rapid containment and recovery.
- Network Segmentation:
- Examples:
- Protecting PLCs in a manufacturing plant from unauthorized reprogramming.
- What They Are:
IoT Device Security:
- What It Involves:
- Securing IoT devices used in industrial environments, such as sensors, cameras, and actuators.
- Threats:
- IoT devices often have limited built-in security, making them prime targets for attackers.
- Compromised IoT devices can act as entry points for broader attacks on OT systems.
- Security Measures:
- Authentication:
- Use device certificates and mutual authentication to validate device identity.
- Encryption:
- Protect data in transit between IoT devices and OT networks using TLS or IPsec.
- Monitoring:
- Continuously monitor IoT devices for unusual behavior or unauthorized access.
- Authentication:
- Applications:
- Securing smart sensors in water treatment plants to prevent tampering with water quality data.
- What It Involves:
Applications of OT Security
Preventing Attacks on Manufacturing Systems:
- Challenges:
- Manufacturing systems often rely on legacy equipment with limited security capabilities.
- Examples of Threats:
- Ransomware locking production lines.
- Spoofing attacks altering sensor readings, leading to production errors.
- Solutions:
- Implementing endpoint protection for industrial machines.
- Using intrusion detection systems tailored for OT environments.
- Real-World Example:
- A steel plant deploying OT-specific firewalls to safeguard automated systems from malware.
- Challenges:
Enhancing Resilience Against OT-Specific Threats:
- Threats:
- Advanced Persistent Threats (APTs) targeting critical systems for espionage or sabotage.
- Strategies:
- Redundancy:
- Deploy failover systems to maintain operations during attacks.
- Regular Testing:
- Conduct penetration tests simulating OT-specific threats.
- Backup and Recovery:
- Ensure critical data and configurations can be restored quickly.
- Redundancy:
- Applications:
- Securing smart grids from attacks that could disrupt power supply to entire regions.
- Threats:
Emerging Trends in Operational Technology (OT) Security
Convergence of IT and OT Security:
- What It Is:
- Integration of IT and OT networks increases operational efficiency but introduces shared risks.
- Focus Areas:
- Unified monitoring and threat detection across IT and OT environments.
- Coordinated incident response plans to address blended attacks.
- What It Is:
AI-Powered Threat Detection:
- Capabilities:
- Machine learning models analyze operational data to identify anomalies indicative of cyber threats.
- Applications:
- Predicting potential failures in industrial equipment due to malicious tampering.
- Capabilities:
Zero Trust for OT Systems:
- Principles:
- Assume no user, device, or application is inherently trusted.
- Applications:
- Continuous verification of device and user identities in SCADA systems.
- Implementing micro-segmentation to minimize lateral movement of threats.
- Principles:
5G-Enabled OT Security:
- Opportunities:
- The adoption of 5G networks in industrial environments provides higher speeds and low latency.
- Challenges:
- Securing new attack surfaces created by 5G-connected devices.
- Solutions:
- Using network slicing to segregate industrial traffic from other data streams.
- Opportunities:
Challenges in Operational Technology (OT) Security
Legacy Systems:
- Many OT systems were designed before cybersecurity was a major concern, leading to inherent vulnerabilities.
- Solution:
- Deploy security gateways to protect legacy equipment without requiring major upgrades.
Limited Patch Availability:
- OT systems often operate in environments where downtime for updates is unacceptable.
- Solution:
- Implement compensating controls like network monitoring and intrusion prevention.
Human Error:
- Operators may inadvertently expose systems to risks through misconfigurations or unintentional actions.
- Solution:
- Conduct regular training and awareness programs for OT personnel.
Resource Constraints:
- Limited budgets and expertise for OT security in small or midsize organizations.
- Solution:
- Leverage managed security service providers (MSSPs) specializing in OT environments.
Tools for Operational Technology (OT) Security
SCADA-Specific Firewalls:
- Protect SCADA systems from unauthorized access and attacks.
- Examples: Fortinet FortiGate, Palo Alto Networks OT Firewalls.
Intrusion Detection and Prevention Systems (IDPS):
- Tools like Nozomi Networks and Claroty monitor OT networks for threats.
Endpoint Security for OT:
- Solutions like McAfee Application Control for ICS to protect endpoints in industrial environments.
Secure Remote Access Tools:
- Ensure secure connections for maintenance and monitoring of OT systems.
- Examples: TeamViewer IoT, Pulse Secure.
Benefits of OT Security
Operational Continuity:
Prevents disruptions in critical industrial processes, minimizing downtime.
Protects Public Safety:
Safeguards systems like energy grids and water supplies, ensuring they remain secure and reliable.
Compliance:
Meets regulatory requirements for industries handling critical infrastructure.
Improved Resilience:
Enhances the ability to detect, respond to, and recover from OT-specific cyber threats.
Why Study Operational Technology (OT) Security
Securing the Systems That Run the Physical World
Understanding the Unique Challenges of OT Environments
Exploring Industrial Threats and Vulnerabilities
Bridging the Gap Between IT and OT Security Practices
Preparing for High-Demand Careers in Industrial Cybersecurity
OT Security – Frequently Asked Questions
These FAQs explain the core ideas, threats, and career pathways in Operational Technology (OT) security so that students can see how cybersecurity applies to real industrial and critical infrastructure systems.
What is OT security and how is it different from traditional IT security?
OT security refers to the protection of operational technology systems such as industrial control systems (ICS), SCADA systems, PLCs, and other devices that monitor and control physical processes in factories, utilities, transportation, and critical infrastructure. It differs from traditional IT security because OT systems are tightly linked to real-world equipment, safety, and uptime, so changes that might be routine in IT can be risky in OT. In OT environments, priorities often follow the order of safety and availability first, followed by integrity and confidentiality, whereas IT security usually emphasises confidentiality, integrity, and availability. Understanding OT security requires both cybersecurity knowledge and a basic grasp of engineering systems, industrial processes, and safety requirements.
Why is OT security important for critical infrastructure and industrial systems?
OT security is important because industrial and critical infrastructure systems control essential services such as power, water, manufacturing, transport, and building automation. A successful cyberattack on these systems can cause physical damage to equipment, production downtime, safety incidents, environmental harm, or disruption of public services. As OT networks become more connected to IT systems and the internet, attackers gain more pathways to reach control systems that were once isolated. Securing OT helps organisations protect human safety, maintain regulatory compliance, avoid costly outages, and preserve public trust in essential services.
What are some common cyber threats to OT environments and industrial control systems?
Common cyber threats to OT environments include malware and ransomware that target industrial systems, phishing campaigns that compromise operator accounts, and remote access abuse through poorly secured VPNs or remote desktop tools. Attackers may exploit unpatched vulnerabilities in PLCs, HMIs, engineering workstations, or Windows servers that sit at the boundary between IT and OT networks. Misconfigurations, weak passwords, and shared accounts are frequent weaknesses in control system environments. In more advanced cases, adversaries may attempt to modify setpoints, disable safety systems, or subtly manipulate sensor data to cause unsafe or inefficient operation without immediate detection.
How does network segmentation help improve OT security?
Network segmentation improves OT security by dividing the overall environment into zones and conduits with controlled communication paths between them. In a typical design, business IT networks, demilitarised zones (DMZs), and OT control networks are separated with firewalls and strictly defined rules for what traffic is allowed. This structure limits the spread of malware or an intruder from office systems into sensitive control networks, and helps ensure that only essential protocols and services are exposed across boundaries. Segmentation also supports monitoring, because security teams can place sensors and logging points at key chokepoints to detect anomalous traffic moving between zones.
What security controls are commonly used to protect OT systems and devices?
Common security controls for OT systems include network segmentation, firewalls, and intrusion detection systems tuned for industrial protocols such as Modbus, DNP3, or PROFINET. Organisations also use strict access control for engineering workstations and control rooms, including multifactor authentication, role-based access, and locked cabinets or enclosures for critical hardware. Hardening measures such as disabling unused services, enforcing secure remote access methods, and applying carefully tested patches are important, even when patching must be scheduled to avoid production disruption. Continuous monitoring, security logging, and incident response procedures adapted to OT environments help detect and respond to abnormal activity while respecting operational and safety constraints.
How do standards and frameworks such as IEC 62443 support OT security?
Standards and frameworks such as IEC 62443, NIST guidance, and sector-specific regulations provide structured approaches for improving OT security. IEC 62443, for example, describes security requirements for control system components, system-level architectures, and organisational processes, including concepts like security zones, conduits, and security levels. These documents help asset owners, integrators, and vendors align on common terminology and baseline expectations, making it easier to design, procure, and operate secure industrial systems. For students, learning these frameworks offers a roadmap for how technical controls, governance, and lifecycle management come together in real industrial cybersecurity projects.
What challenges do organisations face when securing legacy OT systems?
Organisations often face significant challenges when securing legacy OT systems because many were designed decades ago without modern cybersecurity in mind. These systems may run outdated operating systems, support only weak authentication, and cannot easily be patched or restarted without disrupting production. Vendors may no longer support the equipment or may require long maintenance windows for updates, leading to delayed remediation of vulnerabilities. To manage these constraints, security teams rely on compensating controls such as strict network isolation, carefully managed remote access, enhanced monitoring, and detailed procedures that balance safety, uptime, and security requirements.
What skills and knowledge are useful for students interested in OT security careers?
Students interested in OT security careers benefit from a mix of cybersecurity fundamentals, networking knowledge, and basic understanding of industrial control concepts. Useful topics include network architecture, firewalls, industrial protocols, security monitoring, and incident response, together with awareness of safety systems, control loops, and physical process behaviour. Hands-on practice with simulation tools, lab environments, or entry-level roles in industrial operations and maintenance can help bridge the gap between theory and real plant conditions. Strong communication skills are also important, because OT security professionals must collaborate with engineers, operators, and management to design controls that respect safety, reliability, and production goals.
Operational Technology Security: Conclusion
Operational Technology security is vital for protecting the backbone of modern industries and critical infrastructure. As the OT environment becomes more interconnected, implementing robust and adaptive security measures will be essential to address evolving risks and ensure the safety and reliability of industrial operations.
Operational Technology Security: Review Questions and Answers:
1. What is OT security and why is it important for industrial environments?
Answer: OT security refers to the practices and technologies used to protect operational technology systems, including industrial control systems (ICS) and SCADA, from cyber threats. It is important because these systems control critical infrastructure and manufacturing processes, and any breach can lead to significant safety hazards and operational disruptions. Effective OT security ensures the continuity of industrial operations and prevents potential physical damage. By implementing robust OT security measures, organizations can protect both digital and physical assets from malicious activities.
2. How do OT environments differ from traditional IT systems in terms of security requirements?
Answer: OT environments differ from traditional IT systems in that they focus on the control and monitoring of physical processes rather than data processing alone. These systems often require real-time responses and high availability, making them more sensitive to disruptions. OT security must address legacy technologies, proprietary protocols, and stringent safety requirements that are not typically a concern in IT environments. This unique set of challenges demands specialized security approaches tailored to the operational technology landscape.
3. What are the common threats faced by operational technology systems?
Answer: Common threats to OT systems include malware, ransomware, and targeted attacks on industrial control systems designed to disrupt operations. Cyber criminals may exploit vulnerabilities in legacy systems, unpatched software, or insecure communication protocols to gain unauthorized access. Additionally, insider threats and supply chain attacks can compromise OT environments. These threats can result in physical damage, safety risks, and severe financial losses if not properly mitigated.
4. How does risk management contribute to effective OT security?
Answer: Risk management in OT security involves identifying, assessing, and mitigating potential vulnerabilities and threats that could disrupt industrial operations. It helps prioritize security investments by quantifying risks and determining the impact of potential incidents. By continuously monitoring and updating risk assessments, organizations can adapt to evolving threats and maintain resilience. This proactive approach not only safeguards critical infrastructure but also supports compliance with industry regulations and standards.
5. What role does network segmentation play in enhancing OT security?
Answer: Network segmentation divides an OT network into smaller, isolated sections, limiting the spread of cyber threats within the environment. It restricts access between segments, ensuring that a breach in one area does not compromise the entire system. Segmentation allows for tailored security controls and minimizes the attack surface by isolating critical systems. This approach is essential in reducing the potential impact of cyber incidents and maintaining operational continuity in complex OT environments.
6. How do patch management and system updates impact the security of OT systems?
Answer: Patch management and regular system updates are crucial for addressing vulnerabilities in OT systems, especially those running legacy software. Timely updates help close security gaps and protect against known exploits that could be leveraged by attackers. In OT environments, where downtime can have severe consequences, careful planning and testing of patches are essential. Effective patch management ensures that systems remain secure while maintaining the stability and safety of industrial processes.
7. What are the challenges of integrating OT security with traditional IT security measures?
Answer: Integrating OT security with traditional IT security measures poses challenges due to the distinct operational requirements and technologies used in each domain. OT systems often run on outdated or proprietary hardware that may not support modern IT security tools. This integration requires reconciling different protocols, response times, and risk management approaches while ensuring that safety-critical processes are not disrupted. Overcoming these challenges demands a coordinated strategy that addresses the unique needs of both OT and IT environments.
8. How do compliance and regulatory requirements influence OT security practices?
Answer: Compliance and regulatory requirements play a significant role in shaping OT security practices by establishing standards that organizations must meet to protect critical infrastructure. Regulations often mandate specific security controls, risk assessments, and reporting procedures to ensure the safety and reliability of industrial systems. Adhering to these requirements not only minimizes legal and financial risks but also enhances overall operational security. As a result, organizations must continuously update their OT security strategies to remain compliant with evolving industry standards and government regulations.
9. What strategies can organizations implement to improve threat detection in OT environments?
Answer: Organizations can improve threat detection in OT environments by implementing continuous monitoring systems, advanced intrusion detection, and anomaly-based analytics. Utilizing technologies such as machine learning and behavioral analysis helps identify unusual activities that could indicate a breach. Additionally, integrating real-time data from sensors and control systems enhances situational awareness. These strategies enable rapid detection and response to potential threats, minimizing the risk of disruption to critical industrial operations.
10. What future trends are expected to shape the evolution of OT security?
Answer: Future trends in OT security include the increasing convergence of IT and OT systems, the adoption of artificial intelligence for predictive threat analysis, and the integration of blockchain for secure data integrity. These advancements will lead to more sophisticated threat detection and response capabilities, tailored to the unique demands of industrial environments. Additionally, the growth of IoT devices in OT systems will drive the development of scalable and flexible security solutions. As technology evolves, organizations will need to continuously innovate their OT security strategies to address emerging risks and maintain resilience.
Operational Technology Security: Thought-Provoking Questions and Answers
1. How might the convergence of IT and OT networks redefine security strategies in industrial environments?
Answer: The convergence of IT and OT networks blurs the traditional boundaries between enterprise and operational technologies, requiring a unified security approach that addresses both digital and physical risks. This integration allows for enhanced data sharing and operational efficiency but also increases the potential attack surface, making it essential to develop cross-domain security strategies. Organizations will need to implement integrated monitoring and incident response systems that cover both IT and OT components seamlessly.
The convergence could drive innovations such as centralized security management platforms and automated threat intelligence sharing between IT and OT systems. However, it also presents challenges in standardizing security policies and ensuring that legacy OT devices can effectively communicate with modern IT systems without compromising security. Balancing these factors will be critical to achieving a secure, interconnected infrastructure.
2. What role can artificial intelligence play in enhancing threat detection and response in OT security?
Answer: Artificial intelligence (AI) can significantly enhance threat detection and response in OT security by processing large volumes of data from sensors, control systems, and network traffic in real time. AI algorithms can learn normal operational patterns and quickly identify anomalies that may indicate potential cyber attacks or system malfunctions. This proactive approach enables faster incident response and more effective mitigation strategies, reducing the impact of security breaches on critical infrastructure.
Furthermore, AI can facilitate predictive analytics by identifying emerging threats and vulnerabilities before they are exploited. The integration of machine learning into OT security systems can also automate routine monitoring tasks, freeing up human resources to focus on strategic decision-making. However, the implementation of AI must be carefully managed to ensure accuracy and avoid false positives, especially in safety-critical environments.
3. How might the increasing adoption of IoT devices in industrial settings impact OT security measures?
Answer: The increasing adoption of IoT devices in industrial settings expands the operational technology landscape, introducing numerous endpoints that require robust security measures. Each IoT device represents a potential entry point for cyber attacks, making it essential to implement scalable security solutions that can monitor and protect a vast array of connected devices. This growth necessitates specialized protocols for device authentication, data encryption, and continuous monitoring tailored to the resource constraints of IoT technology.
On the other hand, the proliferation of IoT devices offers opportunities for enhanced operational efficiency and real-time data analytics. To capitalize on these benefits while mitigating risks, organizations must integrate IoT security into their overall OT security framework, leveraging advanced analytics and automated response mechanisms. This holistic approach ensures that the expansion of IoT does not compromise the integrity and reliability of critical industrial systems.
4. What challenges do legacy OT systems present in implementing modern security measures, and how can organizations overcome these obstacles?
Answer: Legacy OT systems often lack the necessary infrastructure to support modern security measures, such as advanced encryption, continuous monitoring, and automated threat detection. These older systems may run on outdated hardware and software that are incompatible with contemporary security protocols, making them vulnerable to cyber attacks. The challenge lies in updating or integrating these systems without disrupting critical operational processes.
Organizations can overcome these obstacles by adopting a phased modernization strategy that includes deploying security gateways, using network segmentation to isolate legacy systems, and implementing specialized patches or virtualized environments. Collaboration with vendors and investing in custom security solutions tailored to legacy infrastructures are also effective strategies. This approach not only enhances security but also extends the useful life of legacy systems while gradually transitioning to modern technologies.
5. How can regulatory and compliance requirements drive innovation in OT security practices?
Answer: Regulatory and compliance requirements set stringent standards for the protection of critical infrastructure, pushing organizations to innovate their OT security practices to meet these benchmarks. These requirements mandate regular risk assessments, continuous monitoring, and robust incident response protocols, which drive the development and adoption of advanced security technologies. Compliance pressures encourage organizations to invest in cutting-edge solutions such as AI-based threat detection, blockchain for data integrity, and comprehensive access control systems.
Moreover, the need to adhere to regulatory standards fosters collaboration between industry, government, and academia, leading to the creation of standardized frameworks and best practices that benefit the entire sector. This collaborative environment not only enhances overall security but also ensures that innovations are aligned with legal and ethical standards, ultimately contributing to a safer and more resilient industrial landscape.
6. What ethical considerations arise when deploying advanced monitoring technologies in OT environments, and how can organizations address them?
Answer: Deploying advanced monitoring technologies in OT environments raises ethical considerations related to privacy, data collection, and the potential for intrusive surveillance of operational processes. There is a risk that extensive monitoring could infringe on employee privacy or expose sensitive operational data beyond what is necessary for security purposes. Organizations must balance the need for comprehensive security with respect for individual privacy and operational confidentiality by establishing clear data governance policies and ethical guidelines.
To address these concerns, organizations should implement robust access controls, anonymize collected data where possible, and ensure transparency in monitoring practices. Engaging stakeholders in the development of these policies and regularly reviewing them to align with ethical standards can help build trust and ensure that advanced monitoring technologies are used responsibly.
7. How might the integration of blockchain technology enhance the security and integrity of OT networks?
Answer: Blockchain technology can enhance the security and integrity of OT networks by providing a decentralized, tamper-proof ledger for recording transactions and system events. This immutable record-keeping ensures that once data is entered, it cannot be altered without consensus from the network, thereby safeguarding against tampering and unauthorized modifications. Integrating blockchain into OT networks can improve traceability, facilitate secure data sharing, and support robust audit trails that are critical for forensic investigations.
Additionally, blockchain’s decentralized nature reduces the risk of a single point of failure, enhancing the overall resilience of the network. By enabling secure, real-time verification of transactions and system changes, blockchain technology can serve as a powerful tool in maintaining the integrity and reliability of operational technology environments, especially in distributed and complex infrastructures.
8. What future trends could redefine the landscape of OT security in the next decade?
Answer: Future trends that could redefine the OT security landscape include the increased convergence of IT and OT systems, the widespread adoption of AI and machine learning for predictive threat analysis, and the emergence of quantum-resistant encryption techniques. These trends will lead to more adaptive and proactive security measures capable of addressing the evolving nature of cyber threats in industrial environments. Additionally, the growing use of IoT devices and cloud-based OT solutions will drive the need for scalable and flexible security architectures.
As these trends mature, organizations will likely see a shift towards integrated security platforms that provide end-to-end protection across both IT and OT domains. This evolution will necessitate continuous innovation, cross-industry collaboration, and the development of new regulatory frameworks to ensure that emerging technologies are deployed securely and effectively.
9. How can organizations measure the effectiveness of their OT security programs beyond traditional metrics?
Answer: Organizations can measure the effectiveness of their OT security programs by incorporating advanced analytics and real-time monitoring data into their assessment frameworks. Beyond traditional metrics such as incident counts and response times, they can evaluate parameters like system resilience, operational uptime, and the speed of recovery following a breach. Advanced performance indicators, such as mean time to detect (MTTD) and mean time to resolve (MTTR), provide deeper insights into the program’s operational effectiveness.
Furthermore, organizations can use simulation exercises and penetration testing results to assess the robustness of their defenses and identify potential gaps in their security posture. Regularly benchmarking against industry standards and integrating feedback from both technical and operational teams ensures a comprehensive evaluation that drives continuous improvement in OT security strategies.
10. What are the potential cost implications of failing to secure OT environments, and how can investments in OT security yield long-term benefits?
Answer: Failing to secure OT environments can lead to significant cost implications, including operational downtime, equipment damage, regulatory fines, and reputational losses. The disruption of critical infrastructure due to a cyber attack can have cascading effects on production, safety, and overall business continuity. Investments in robust OT security, on the other hand, not only mitigate these risks but also contribute to increased operational efficiency and resilience. By preventing costly breaches and ensuring continuous operations, organizations can achieve substantial long-term savings.
Moreover, proactive OT security investments can enhance customer trust and compliance with regulatory requirements, which are critical for maintaining market competitiveness. Although the initial costs may be high, the return on investment becomes evident through reduced incident-related expenses and improved productivity over time.
11. How can cross-industry collaboration drive innovation in OT security solutions?
Answer: Cross-industry collaboration can drive innovation in OT security by fostering the exchange of best practices, threat intelligence, and technological advancements between sectors with similar security challenges. Collaborative efforts enable organizations to pool resources and expertise to develop more robust and adaptable security solutions tailored to complex OT environments. Such partnerships can lead to standardized protocols, shared research initiatives, and joint development of cutting-edge technologies that enhance the overall security posture.
This collaborative approach also facilitates the rapid dissemination of new ideas and innovations across industries, accelerating the adoption of advanced security measures. By working together, companies can overcome common challenges and create a more resilient global framework for protecting critical operational technology infrastructures.
12. How might emerging regulatory changes impact the future development of OT security standards and practices?
Answer: Emerging regulatory changes are likely to significantly impact the future development of OT security standards by mandating stricter compliance requirements and fostering a culture of continuous improvement. As governments and international bodies recognize the increasing risks associated with cyber threats to critical infrastructure, they will push for the adoption of more rigorous security protocols and standardized practices. This regulatory pressure will drive innovation in OT security technologies and practices, ensuring that organizations adopt comprehensive measures to protect their systems.
Additionally, enhanced regulatory frameworks can lead to greater transparency and accountability in OT security, ultimately improving risk management and incident response. Organizations that proactively align their security strategies with these evolving regulations will not only mitigate legal risks but also build a more resilient and future-proof operational technology environment.
Operational Technology Security: Numerical Problems and Solutions:
1. An OT network has 1,500 industrial control devices, and 3% are compromised due to security vulnerabilities. Calculate the number of compromised devices, then determine how many would remain if a security upgrade reduces vulnerabilities by 80%, and finally compute the absolute reduction.
Solution:
• Step 1: Compromised devices = 1,500 × 0.03 = 45 devices.
• Step 2: With an 80% reduction, remaining compromised devices = 45 × (1 – 0.80) = 45 × 0.20 = 9 devices.
• Step 3: Absolute reduction = 45 – 9 = 36 devices.
2. A SCADA system processes 200,000 control signals per day. If a DDoS attack increases signal traffic by 25%, calculate the additional signals per day, then determine the total signals processed during the attack, and finally compute the percentage increase.
Solution:
• Step 1: Additional signals = 200,000 × 0.25 = 50,000 signals.
• Step 2: Total signals during attack = 200,000 + 50,000 = 250,000 signals.
• Step 3: Percentage increase = (50,000 ÷ 200,000) × 100 = 25%.
3. A vulnerability scan in an OT environment takes 40 minutes to complete for 500 devices. Calculate the scanning rate per device in minutes, then estimate the time required to scan 2,000 devices, and finally determine the time saved if an upgraded system increases scanning speed by 50%.
Solution:
• Step 1: Scanning rate per device = 40 minutes ÷ 500 = 0.08 minutes per device.
• Step 2: Time for 2,000 devices = 2,000 × 0.08 = 160 minutes.
• Step 3: With a 50% speed increase, new time = 160 ÷ 1.5 ≈ 106.67 minutes; time saved = 160 – 106.67 ≈ 53.33 minutes.
4. An OT security system logs 300 events per minute. If 0.5% of these events indicate potential threats, calculate the number of threat events per minute, per hour, and per day.
Solution:
• Step 1: Threat events per minute = 300 × 0.005 = 1.5 events.
• Step 2: Threat events per hour = 1.5 × 60 = 90 events.
• Step 3: Threat events per day = 90 × 24 = 2,160 events.
5. A company spends $500,000 on OT security measures that reduce downtime by 70%. If an unmitigated breach would cost $1,200,000 in downtime annually, calculate the annual cost after improvements and the savings percentage.
Solution:
• Step 1: Downtime cost after reduction = $1,200,000 × (1 – 0.70) = $1,200,000 × 0.30 = $360,000.
• Step 2: Annual savings = $1,200,000 – $360,000 = $840,000.
• Step 3: Savings percentage = ($840,000 ÷ $1,200,000) × 100 = 70%.
6. A patch management initiative reduces system vulnerabilities by 85% from an initial count of 400 vulnerabilities. Calculate the number of vulnerabilities fixed, the remaining vulnerabilities, and the overall reduction percentage.
Solution:
• Step 1: Vulnerabilities fixed = 400 × 0.85 = 340 vulnerabilities.
• Step 2: Remaining vulnerabilities = 400 – 340 = 60 vulnerabilities.
• Step 3: Overall reduction percentage = (340 ÷ 400) × 100 = 85%.
7. A network security audit in an OT environment reviews 10,000 logs per day. If 2% of logs require further investigation, calculate the number of logs flagged per day, then per week (7 days), and finally per month (30 days).
Solution:
• Step 1: Logs flagged per day = 10,000 × 0.02 = 200 logs.
• Step 2: Per week = 200 × 7 = 1,400 logs.
• Step 3: Per month = 200 × 30 = 6,000 logs.
8. An intrusion detection system (IDS) has an accuracy of 95% and processes 800,000 events per day. Calculate the number of accurately processed events, the number of errors, and the error rate per day.
Solution:
• Step 1: Accurately processed events = 800,000 × 0.95 = 760,000 events.
• Step 2: Errors = 800,000 – 760,000 = 40,000 events.
• Step 3: Error rate = (40,000 ÷ 800,000) × 100 = 5%.
9. A secure OT network uses 128-bit encryption. Estimate the total number of possible keys, then determine the time required to brute-force all keys at a rate of 10^9 keys per second, and finally convert that time into years using 3.15×10^7 seconds per year.
Solution:
• Step 1: Total possible keys = 2^128.
• Step 2: Brute-force time in seconds = 2^128 ÷ 10^9.
• Step 3: Time in years = (2^128 ÷ 10^9) ÷ 3.15×10^7; this value is astronomically high, demonstrating the impracticality of brute-force attacks.
10. An OT incident response team reduces recovery time from 120 minutes to 45 minutes per incident. For 15 incidents per year, calculate the total time saved annually in minutes and convert that into hours.
Solution:
• Step 1: Time saved per incident = 120 – 45 = 75 minutes.
• Step 2: Total time saved annually = 15 × 75 = 1,125 minutes.
• Step 3: Convert to hours = 1,125 ÷ 60 ≈ 18.75 hours.
11. A network segmentation project divides an OT network into 5 segments, reducing lateral movement risk by 80%. If an initial breach could affect 500 devices, calculate the potential devices affected after segmentation and the absolute reduction in devices.
Solution:
• Step 1: Expected devices affected after segmentation = 500 × (1 – 0.80) = 500 × 0.20 = 100 devices.
• Step 2: Absolute reduction = 500 – 100 = 400 devices.
• Step 3: Percentage reduction is 80%, as given.
12. An incident response drill takes 45 minutes per exercise. If a company conducts 10 drills per quarter, calculate the total drill time per year and the percentage time reduction if improvements cut drill time by 33%.
Solution:
• Step 1: Drills per year = 10 drills × 4 = 40 drills.
• Step 2: Total drill time before = 40 × 45 = 1,800 minutes.
• Step 3: With a 33% reduction, new time per drill = 45 × (1 – 0.33) = 45 × 0.67 ≈ 30.15 minutes; total new drill time = 40 × 30.15 ≈ 1,206 minutes, saving approximately 594 minutes, which is a 33% reduction.
