Network Security in Cybersecurity Education teaches an often-overlooked truth: most attacks are not “mystical”—they are simply traffic finding the easiest path. The diagram captures how learners are trained to close those paths thoughtfully. Inputs (resources, examples, foundational knowledge) enter the learning process, but they are shaped by controls that impose discipline: policies, standards, and rules that define what must be protected and what “good security” looks like in practice. Mechanisms—expert guidance and networking tools—turn abstract ideas into concrete skill: mapping network boundaries, segmenting systems, controlling flows, and reading network behavior through logs and signals. The output is a learner who can design connectivity without surrendering control—someone who understands that a secure network is not a single device or a single setting, but a coherent set of choices that make communication reliable for users and costly for attackers.
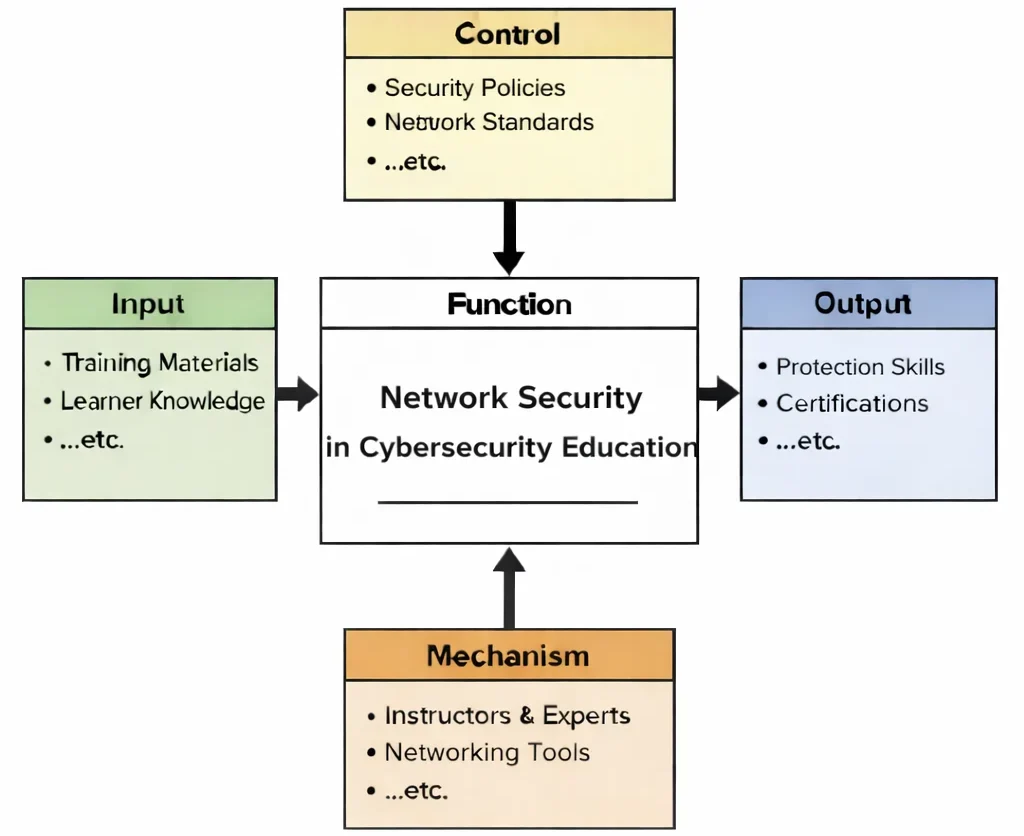
This IDEF0 (Input–Control–Output–Mechanism) diagram summarizes Network Security in Cybersecurity Education as a structured learning transformation. Inputs include training materials and learner knowledge that feed the central function. Controls—such as security policies and networking standards—set the rules for safe design and evaluation. Mechanisms such as instructors/experts and networking tools enable hands-on practice in a controlled environment. Outputs include practical network protection skills and demonstrable competency (often aligned with assessments or certifications), reflecting the ability to design, secure, monitor, and troubleshoot networks with security as a first-class requirement.
Network security is the front line of modern cybersecurity, protecting the confidentiality, integrity, and availability of data as it moves across interconnected systems. As organizations deliver services, handle sensitive information, and operate distributed teams, securing networks against insider misuse and sophisticated external threats has never been more critical.
Effective defenses are layered. Signals from AI & ML in cybersecurity power predictive detection and adaptive filtering at scale, while strong application security prevents web and API exploits from becoming network footholds. Combined with robust cryptography for data in transit and at rest, these controls create a resilient fabric that limits exposure and slows attackers down.
Identity is the new perimeter: identity and access management (MFA, least privilege, just-in-time access) constrains who can reach what, while continuous security awareness reduces social-engineering risk. When incidents occur, disciplined incident response & forensics contain impact, preserve evidence, and feed lessons learned into stronger policies and playbooks.
Today’s estates span cloud, on-prem, and roaming endpoints—and increasingly include safety-critical OT and CPS. That expanded attack surface demands Zero-Trust-style segmentation, egress controls, and high-quality telemetry (DNS/HTTP, flow, IDS) to see and stop lateral movement. Defenders track evolving tradecraft via threat intelligence and analyze patterns with data analysis and visualization—backed by scalable collection & storage, modern tools, and big-data analytics.
Finally, sound monitoring respects people. Ethical guardrails and social considerations help teams balance visibility with privacy. Red-teaming and ethical hacking validate assumptions, while domain-specific analytics tailor detections to each industry. Done well, network security blends engineering, strategy, and data-driven insight to keep infrastructures reliable and worthy of trust.

What you’ll learn on this page
- A Zero-Trust-aware network reference architecture — control vs. data plane, trust boundaries, and where to enforce policy.
- North–south vs. east–west controls — segmentation, firewalls, proxies, and micro-segmentation that limits blast radius.
- DNS, TLS & certificate hygiene — DoH/DoT, HSTS, rotation, and common misconfigurations attackers exploit.
- Telemetry that matters & right-sizing retention — which logs to keep, baselining, alerting that reduces noise.
- Practical playbooks & runbooks — BEC, C2 beaconing, DDoS spikes, and lateral movement containment.
If a link doesn’t jump yet, add the matching id to the target section’s heading
(e.g., <h2 id="dns-tls">DNS, TLS & Certificates</h2>).
What is network security in cybersecurity?
Network security is the practice of protecting the integrity, confidentiality, and availability of data as it travels across or is stored on computer networks. It combines hardware devices, software controls, policies, and monitoring to prevent unauthorised access, misuse, modification, or disruption of network services. Typical measures include firewalls, intrusion detection and prevention systems, secure network protocols, access control, encryption, and continuous monitoring using logs and security analytics. For students, understanding network security provides the foundation for topics such as ethical hacking, secure system design, and incident response in larger cybersecurity architectures.
What are the main types of network security threats?
The main types of network security threats include malware infections, phishing and social engineering, denial-of-service and distributed denial-of-service attacks, man-in-the-middle attacks, and unauthorised access through weak or stolen credentials. Other important threats are eavesdropping on unencrypted traffic, exploitation of software vulnerabilities, misconfigured network devices, and insider misuse of network resources. Many of these threats target both technical weaknesses and human behaviour, so effective network security requires a combination of technical controls, secure configuration, and user awareness. Learning to classify threat types helps students choose appropriate countermeasures and design layered defences that do not rely on any single control.
How do firewalls help protect a network?
Firewalls protect a network by controlling incoming and outgoing traffic based on a defined security policy. They filter packets or connections using rules that consider source and destination addresses, ports, protocols, and sometimes application-level information. Traditional firewalls focus on network and transport layers, while next-generation firewalls add deep packet inspection, intrusion prevention, and application awareness to detect more sophisticated attacks. In practice, firewalls are used to create security zones, limit exposure of internal systems, and enforce the principle of least privilege for network access between segments and to the internet.
What is the difference between IDS and IPS in network security?
An Intrusion Detection System (IDS) monitors network traffic for suspicious patterns and policy violations and alerts security teams when potential attacks are detected. An Intrusion Prevention System (IPS) goes a step further by actively blocking or modifying traffic in real time to prevent malicious activity from reaching its target. Both systems can use signature-based detection, which matches known attack patterns, and anomaly-based detection, which looks for deviations from normal behaviour. Understanding the difference between IDS and IPS helps students reason about where to place controls in a network and how to balance detection accuracy against the risk of blocking legitimate traffic.
Why is network segmentation important for security?
Network segmentation is important because it divides a large network into smaller, isolated segments, limiting how far an attacker or malware can move if a breach occurs. By placing high-value systems, sensitive data, and critical services in protected zones, organisations can apply stricter access controls and monitoring where the risk is highest. Segmentation supports the principle of least privilege by ensuring that users and systems only have network access to the resources they truly need. For students, network segmentation illustrates how good architecture and design can reduce the impact of security incidents even when individual devices or users are compromised.
How do VPNs contribute to network security?
Virtual Private Networks (VPNs) contribute to network security by creating encrypted tunnels between remote users or sites and the organisation’s internal network. This encryption protects data in transit from eavesdropping, tampering, and man-in-the-middle attacks, especially over untrusted networks such as public Wi-Fi. VPNs also enforce authentication, ensuring that only authorised users and devices can establish a secure connection to internal resources. In a broader security architecture, VPNs are often combined with network segmentation, multi-factor authentication, and endpoint protection to secure hybrid and remote access scenarios.
What skills are useful for students who want to specialise in network security?
Students who want to specialise in network security benefit from strong foundations in computer networks, TCP/IP, and common routing and switching technologies. Practical skills include configuring routers, switches, and firewalls; analysing network traffic with tools like Wireshark; and working with VPNs, IDS/IPS, and secure protocols. An understanding of operating systems, scripting for automation, and basic programming helps in writing security rules, processing logs, and building custom detection logic. Soft skills such as documentation, communication, and the ability to translate technical risks into business language are also important for real-world security roles and collaboration with non-technical stakeholders.
Table of Contents
Key Topics in Network Security in Cybersecurity
Firewalls:
- Act as a barrier between trusted and untrusted networks.
- Control incoming and outgoing traffic based on predefined security rules.
- Types of Firewalls:
- Packet-Filtering Firewalls: Analyze individual packets based on source/destination IP, port, and protocol.
- Stateful Inspection Firewalls: Monitor the state of active connections and determine which packets to allow.
- Next-Generation Firewalls (NGFWs): Combine traditional firewall functions with advanced features like application awareness and intrusion prevention.
Intrusion Detection and Prevention Systems (IDS/IPS):
- IDS: Monitors network traffic for suspicious activities and alerts administrators.
- IPS: Detects and actively blocks malicious activities in real time.
- Techniques:
- Signature-based detection (matches known attack patterns).
- Anomaly-based detection (flags unusual traffic behavior).
Virtual Private Networks (VPNs):
- Securely connect remote users or branch offices to a corporate network.
- Encrypt data transmitted over public networks to prevent eavesdropping.
- Types of VPNs:
- Site-to-Site VPNs: Connect entire networks.
- Remote Access VPNs: Secure connections for individual users.
Secure Socket Layer (SSL)/Transport Layer Security (TLS):
- Protocols for encrypting data in transit.
- Ensure secure communication between web browsers and servers (e.g., HTTPS).
- Protect sensitive data like login credentials, credit card information, and emails.
Wireless Network Security:
- Protects Wi-Fi networks from unauthorized access.
- Key Measures:
- Use strong encryption protocols (e.g., WPA3).
- Secure access points to prevent rogue devices.
- Implement MAC address filtering and hidden SSIDs.
- Wireless threats include eavesdropping, man-in-the-middle (MITM) attacks, and rogue access points.
Zero Trust Network Architecture:
- Assumes no part of the network is inherently secure.
- Continuously verifies user and device authenticity before granting access.
- Enforces least-privilege principles.
Network Access Control (NAC):
- Ensures that only authenticated and authorized devices can connect to the network.
- Monitors and enforces security policies.
Common Network Attacks & Mitigations (by OSI Layer)
Use this quick map to connect typical network attack vectors to practical defenses. It reinforces Zero Trust ideas (authenticate, authorize, segment, verify) and aligns naturally with CIS Controls / NIST CSF.
| Layer / Surface | Typical Attacks | What Actually Mitigates It |
|---|---|---|
| Physical / Link (L1–L2) |
• MAC spoofing / ARP spoofing • VLAN hopping (double-tagging) • STP manipulation, CAM table overflow • Rogue AP, evil-twin Wi-Fi |
|
| Network (L3) |
• IP spoofing & scans • ICMP tunneling / misuse • Route hijacking (e.g., BGP) |
|
| Transport (L4) |
• TCP SYN floods, UDP/Amplification DDoS • RDP/SSH brute force |
|
| Session / Presentation (L5–L6) |
• TLS downgrade / weak ciphers • NTLM/SMB relay; LLMNR/NBT-NS poisoning • DNS cache poisoning |
|
| Application (L7) |
• HTTP(S) attacks (SQLi, XSS, path-traversal) • API abuse / credential stuffing • DoH/DoT evasion of DNS policies |
|
| Control Plane / Management |
• Misconfig / exposed admin planes • SNMP leaks (v1/v2c), default creds |
|
| Visibility & Telemetry | • Blind spots → delayed detection |
|
Tip: Pair this table with your existing “Tools & Technologies” section—link each tool to the threats it mitigates, and you’ve created a mini design guide students (and Google) love.
Packet-Flow Walkthrough & Lab: Build a Minimal Zero-Trust Network
Stand up a tiny, **Zero-Trust-flavoured** network: clients authenticate into a private segment, can reach only one service over 443/tcp, and everything else is denied and logged.
Minimal Topology
# Three lightweight Linux VMs/containers (Ubuntu/Alpine ok)
[client] 10.10.10.10 ----\
\ (public) (private)
\ eth0 wg0 eth1
\-->[edge]--------------------->[app]
| 1.2.3.4 10.200.0.1 10.20.0.10
|
Internet
- WireGuard (wg0) forms an authenticated tunnel: client <--> edge
- Edge forwards ONLY tcp/443 to app 10.20.0.10; logs and drops others
If you can’t run three VMs, run client on your laptop and host edge + app as containers/VMs on the same box.
Prereqs
- Basic Linux shell; sudo privileges
- Install wireguard, iptables (or nftables), tcpdump, curl
# Ubuntu/Debian
sudo apt update
sudo apt install -y wireguard iptables tcpdump curl nginx
Objectives
- Enforce “default-deny” at the edge and allow only 443/tcp to an app service.
- Require device/user authentication to enter the private segment (WireGuard).
- Trace the packet path and validate controls with logs and captures.
Maps to CIS 4/5/8 • NIST CSF PR.AC, PR.DS, DE.CM
Step 1 — Secure tunnel (WireGuard)
On edge (public IP 1.2.3.4):
sudo wg genkey | tee /etc/wireguard/edge.key | wg pubkey > /etc/wireguard/edge.pub
sudo bash -c 'cat >/etc/wireguard/wg0.conf' <<EOF
[Interface]
Address = 10.200.0.1/24
ListenPort = 51820
PrivateKey = $(cat /etc/wireguard/edge.key)
PostUp = sysctl -w net.ipv4.ip_forward=1
PostDown = sysctl -w net.ipv4.ip_forward=0
# add client peer after you generate its keys
EOF
sudo systemctl enable --now wg-quick@wg0
On client:
sudo wg genkey | tee ~/client.key | wg pubkey > ~/client.pub
# copy client.pub to edge; copy edge.pub back to client
sudo bash -c 'cat >/etc/wireguard/wg0.conf' <<EOF
[Interface]
Address = 10.200.0.2/24
PrivateKey = $(cat ~/client.key)
[Peer]
PublicKey = <edge.pub>
Endpoint = 1.2.3.4:51820
AllowedIPs = 10.20.0.0/24, 10.200.0.0/24
PersistentKeepalive = 15
EOF
sudo systemctl enable --now wg-quick@wg0
Step 2 — Default-deny firewall & strict forward to the app
On edge (iptables):
# Reset & default policies
sudo iptables -F; sudo iptables -t nat -F; sudo iptables -X
sudo iptables -P INPUT DROP; sudo iptables -P FORWARD DROP; sudo iptables -P OUTPUT ACCEPT
# Allow WireGuard and established traffic
sudo iptables -A INPUT -p udp --dport 51820 -j ACCEPT
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
# From wg0 (10.200.0.0/24) to app (10.20.0.10) ONLY tcp/443
sudo iptables -A FORWARD -i wg0 -o eth1 -p tcp -d 10.20.0.10 --dport 443 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT
sudo iptables -A FORWARD -i eth1 -o wg0 -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
# Log then drop all else
sudo iptables -A FORWARD -i wg0 -j LOG --log-prefix "ZTLAB-DROP "
sudo iptables -A FORWARD -i wg0 -j DROP
# SNAT for app replies
sudo iptables -t nat -A POSTROUTING -s 10.200.0.0/24 -o eth1 -j MASQUERADE
On app (serve HTTPS):
sudo apt install -y nginx
sudo systemctl enable --now nginx
# optional self-signed cert
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 \
-keyout /etc/ssl/private/lab.key -out /etc/ssl/certs/lab.crt \
-subj "/CN=lab.local"
Step 3 — Validate the packet flow
# On client — should SUCCEED
curl -I https://10.20.0.10
# Should FAIL (blocked) — different port
curl -I http://10.20.0.10:80
# Should FAIL (blocked) — different host
curl -I https://10.20.0.11
On the edge, watch for ZTLAB-DROP in /var/log/kern.log or journalctl -f.
Observe packets
# On edge
sudo tcpdump -nni wg0 host 10.200.0.2
sudo tcpdump -nni eth1 host 10.20.0.10 and port 443
Troubleshooting
- No handshake? Check UDP/51820 and time skew.
- No return traffic? Verify MASQUERADE and app’s gateway.
- Unexpected blocks? Check rule order and counters.
Step 5 — Tighten with context
- Enable mTLS on the app; verify who connects, not just where.
- Use a bastion with MFA for admin access; no direct SSH to app.
- Rotate WireGuard keys; restrict to an IP-set of known devices.
Teardown
sudo systemctl stop wg-quick@wg0
sudo iptables -F; sudo iptables -t nat -F; sudo iptables -X
sudo iptables -P INPUT ACCEPT; sudo iptables -P FORWARD ACCEPT; sudo iptables -P OUTPUT ACCEPT
Extend the lab
- Add a second service and prove segmentation with per-service allow-lists.
- Swap iptables for nftables or a cloud NACL.
- Ship logs to a SIEM and alert on ZTLAB-DROP.
Network Security Reference Architectures & Patterns
Four common patterns you can mix-and-match: classic DMZ perimeter, Zero-Trust micro-segmentation, SASE/SD-WAN, and service-mesh for east-west traffic. Each card explains where it fits, must-have controls (firewalls/ACLs, IDS/IPS, WAF, NAC, VPN, TLS), and typical misconfigurations to avoid.
1) Classic Perimeter with DMZ (north–south)
# Internet ──[Edge FW/WAF]── DMZ (reverse proxy, WAF, mail) ──[Internal FW]── App / DB # Controls: edge firewall, IDS/IPS span, DDoS scrubbing, WAF, TLS offload or mTLS pass-through
- Hosting public-facing apps needing a buffer zone (DMZ) and strong north–south controls.
- You rely on appliances/WAFs and simple, centralized policy.
- Flat LAN behind the DMZ (easy lateral movement).
- TLS terminated but not re-encrypted to backends; blind to east-west traffic.
2) Zero-Trust Segments (east–west)
# User/device posture checked by NAC/IdP → policy engine → allow least-privilege to a specific service segment # Enforce with host firewalls, SGs/NACLs (VPC), identity-aware proxies, mTLS between services
- Stopping lateral movement is a priority; you can label workloads (env, app, data class).
- Endpoints support mTLS, identity-aware access, and per-service allow-lists.
- “Any to any” rules during cutover; forgotten egress policies.
- Inconsistent identity signals (CN/SAN mismatch, stale device posture).
3) SASE/SD-WAN for branch & remote
# Branch/remote → SD-WAN edge → SSE (CASB, SWG, ZTNA) → SaaS/IaaS; backhaul optional per-app # Controls: identity-centric access, DNS/HTTP proxy, DLP, inline TLS inspection (lawful), device posture
- You have many branches/remote users and heavy SaaS usage.
- You want central policy with local breakout and app-aware routing.
- Over-inspection of TLS causing breakage or privacy issues.
- Shadow IT bypassing SSE—enforce DNS/DoH policy and egress controls.
4) Service Mesh for east–west inside clusters
# Sidecar proxies inject mTLS, authZ (RBAC/ABAC), retries & rate-limits between services # Controls: mTLS, policy (OPA), network policies (K8s), ingress/egress gateways, WAF for north–south
- You run microservices (Kubernetes) and need fine-grained mTLS + observability.
- Security teams can manage certs and policy as code (GitOps).
- Mesh sprawl & mis-scoped policies; noisy default-allow egress.
- Certificate rotation and telemetry costs not planned.
Choosing a pattern: quick decision matrix
| Need | Best fit | Key controls |
|---|---|---|
| Public-facing apps & north–south hardening | Perimeter + DMZ | Edge FW, WAF, DDoS, IDS/IPS, TLS |
| Stop lateral movement & least-privilege | Zero-Trust Segmentation | NAC, IdP, SG/NACL, mTLS, device posture |
| Many branches/remote + SaaS | SASE / SD-WAN | ZTNA, SWG/CASB, DNS policy, DLP |
| Kubernetes microservices (east–west) | Service Mesh | mTLS, policy as code, K8s NetPol, ingress/egress GW |
Tip: in practice you’ll combine these (e.g., DMZ + Zero-Trust segments + SASE for branches + mesh in clusters).
Network hardening checklist (copy/paste into your runbook)
- Default-deny inbound and egress; maintain per-service allow-lists (ports, CIDRs, FQDNs).
- Enforce TLS 1.2+ everywhere; prefer mTLS for east–west; rotate certs automatically.
- Segment by environment (prod/stage/dev) and data class; tag resources and drive policy from tags.
- Turn on DNS filtering & egress controls; block direct Internet access from sensitive subnets.
- Mirror traffic to IDS/IPS selectively; ship flow logs to SIEM; alert on “first-seen” egress.
- Harden VPN (IKEv2/WireGuard), MFA for admin, bastion-only SSH/RDP; disable direct mgmt from WAN.
- Document change windows, rollback steps, and test plans for ACL updates.
Keywords covered: firewall rules/ACLs, WAF, IDS/IPS, VPN, TLS/mTLS, micro-segmentation, NAC, SD-WAN/SASE, service mesh, Kubernetes network policies.
Cloud Network Security Mapping: AWS vs Azure vs GCP
A side-by-side of core network-security building blocks across the “big three,” plus safe defaults and Terraform starter snippets for common allow-lists. Use this when translating designs or reviewing controls.
| Capability | AWS | Azure | GCP | Notes |
|---|---|---|---|---|
| Virtual network | VPC | Virtual Network (VNet) | VPC Network | Subnets + route tables define reachability. |
| Instance-level firewall | Security Groups (stateful) | NSG (stateful) | GCE Firewall Rules (stateful) | Primary place for app allow-lists; treat as “least-privilege ports.” |
| Subnet-level ACL | NACL (stateless) | — | Hierarchical FW Policy (org/folder/project) | Use sparingly for coarse blocks (egress deny, “scorched earth”). |
| L7 WAF | AWS WAF (ALB/CloudFront/API GW) | Azure WAF (App GW/Front Door) | Cloud Armor | Protect public apps; rate-limit, bot, OWASP rules. |
| Private service access | PrivateLink / VPC Endpoint | Private Endpoint | Private Service Connect | Keep PaaS traffic off the Internet. |
| NAT & egress control | NAT Gateway / Egress-only IGW (IPv6) | NAT Gateway | Cloud NAT | Pair with egress allow-lists (SG/NSG/FW) + DNS policy. |
| DDoS protection | AWS Shield (Std/Adv) | Azure DDoS Protection | Cloud Armor Adaptive | Attach to public endpoints/load balancers. |
| Traffic logging | VPC Flow Logs | NSG Flow Logs (Network Watcher) | VPC Flow Logs | Export to SIEM; alert on “first-seen” destinations. |
| Threat detection | GuardDuty | Defender for Cloud | Cloud IDS / Security Command Center | Enrich with DNS/HTTP proxy logs for egress anomalies. |
| Private connectivity | TGW, VPC Peering | vWAN, Peering | Cloud Router, VPC Peering | Plan CIDR and route domains up-front. |
| Bastion / zero-SSH | SSM Session Manager | Azure Bastion | IAP / OS Login | Avoid direct SSH/RDP from Internet; MFA required. |
Also map: DNS (Route 53 / Azure DNS / Cloud DNS), LBs (ALB/NLB, App GW/Front Door, GLB/NEG).
“Sane defaults” for cloud networks
- Default-deny outbound from workloads; allow only necessary FQDNs/ports via egress policies/DNS proxy.
- Put public apps behind a WAF + DDoS; terminate TLS 1.2+ and re-encrypt to backends or enforce mTLS.
- Use private endpoints for PaaS; block *.blob.core/windows.net etc. except via private DNS zones.
- Segment by env (prod/stage/dev) and data class; tag resources and drive SG/NSG rules from tags.
- Enable Flow Logs + DNS logs to SIEM; alert on new external IPs, high-risk ASN, or blocked spikes.
- Prefer Session Manager / Bastion / IAP over direct SSH/RDP; require MFA & just-in-time access.
Common cloud misconfigurations to watch
- Security Groups/NSGs with
0.0.0.0/0inbound (SSH/DB) or overly permissive egress. - Public storage buckets or load balancers bypassing the WAF (direct backend exposure).
- GCP implied allow rules left in place; Azure “Any-to-Any” NSG during cutover that never got tightened.
- Private endpoints created but public DNS still resolvable → traffic leaks to Internet.
Terraform quick starts (copy/paste & adapt)
AWS: SG allow-list for HTTPS from a branch CIDR; deny everything else by default.
# AWS Security Group (HTTPS only)
resource "aws_security_group" "web_sg" {
name = "web-sg"
description = "Allow HTTPS from branch; default deny all egress tightened below"
vpc_id = var.vpc_id
ingress {
description = "Branch CIDR to ALB"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = [var.branch_cidr]
}
egress { # tighten to required egress later (egress proxy, OCSP, time)
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = []
ipv6_cidr_blocks = []
prefix_list_ids = [aws_ec2_managed_prefix_list.egress_proxy.id]
}
}Azure: NSG rule allowing only 443 from an Application Gateway; deny other inbound.
# Azure NSG (bind to subnet or NIC)
resource "azurerm_network_security_group" "web_nsg" {
name = "web-nsg"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
}
resource "azurerm_network_security_rule" "https_from_appgw" {
name = "Allow-HTTPS-from-AppGW"
priority = 100
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_address_prefixes = [azurerm_application_gateway.appgw.frontend_ip_configuration[0].private_ip_address]
destination_port_range = "443"
destination_address_prefix = "*"
resource_group_name = azurerm_resource_group.rg.name
network_security_group_name = azurerm_network_security_group.web_nsg.name
}GCP: Project firewall restricting egress to an egress-proxy tag + DNS/OCSP.
# GCP: restrict egress to proxy + DNS + OCSP
resource "google_compute_firewall" "egress_policy" {
name = "egress-restricted"
network = google_compute_network.vpc.self_link
direction = "EGRESS"
priority = 1000
target_tags = ["app"]
allow { protocol = "tcp"; ports = ["53","80","443"] } # DNS over TCP if using proxy; adjust as needed
destination_ranges = ["10.10.10.10/32"] # egress proxy, tighten per environment
log_config { metadata = "INCLUDE_ALL_METADATA" }
}Pair with Private Service Connect/Endpoints and WAF to keep traffic private and inspected.
Egress & DNS Security: stop data exfiltration by default
Most breaches need an outbound path. Lock down egress to a proxy, control DNS, and monitor for tunneling. This playbook gives safe defaults, copy-paste rules, and detection ideas for your SIEM.
Safe defaults (policy)
- Default-deny outbound from workloads. Allow only required destinations (FQDNs) via an HTTPS egress proxy or private endpoints.
- Centralize DNS: force all queries to a resolver you control (DoT/DoH to your resolver; block direct UDP/53 & TCP/53 to the Internet).
- No direct admin: use Bastion/SSM/IAP for admin; block outbound SSH/RDP from apps.
- Time, CRL/OCSP, updates: explicitly allow NTP, CRL/OCSP, package mirrors, and observability endpoints.
- Log & alert: VPC/NSG/GCE firewall logs + DNS logs to SIEM; alert on “first-seen” domains/IPs.
Common mistakes
- Security groups/NSGs with
0.0.0.0/0egress. - Letting workloads resolve public DNS directly (no RPZ/sinkhole; easy tunnel path).
- Public endpoints to PaaS still reachable even after enabling private endpoints.
- Permitting outbound SMTP/SSH from app subnets (exfil channel).
Linux host: minimal egress policy (iptables)
Allow only proxy (443), corporate DNS, NTP; drop everything else. Adapt addresses to your environment.
# Default drop sudo iptables -P OUTPUT DROP sudo iptables -A OUTPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT # Allow loopback & metadata if needed sudo iptables -A OUTPUT -o lo -j ACCEPT # DNS to corporate resolver sudo iptables -A OUTPUT -p udp --dport 53 -d 10.10.0.53 -j ACCEPT sudo iptables -A OUTPUT -p tcp --dport 53 -d 10.10.0.53 -j ACCEPT # NTP (time sync) sudo iptables -A OUTPUT -p udp --dport 123 -d 10.10.0.123 -j ACCEPT # Egress proxy (HTTPS CONNECT) sudo iptables -A OUTPUT -p tcp --dport 443 -d 10.10.0.80 -j ACCEPT # Optional: package mirror allow-list (example) sudo iptables -A OUTPUT -p tcp --dport 443 -d 151.101.0.0/16 -j ACCEPT # cdn example # Log & drop remainder (rate limited) sudo iptables -A OUTPUT -m limit --limit 10/min -j LOG --log-prefix "EGRESS-DROP " sudo iptables -A OUTPUT -j DROP
For nftables, use an inet table with a default policy drop and named sets for FQDN-to-IP automation.
Windows Server: lock egress (PowerShell)
# Default block outbound, then add explicit allows New-NetFirewallProfile -Profile Domain,Private,Public -DefaultOutboundAction Block # Allow to corporate DNS New-NetFirewallRule -DisplayName "DNS-out" -Direction Outbound -Protocol UDP -RemotePort 53 -RemoteAddress 10.10.0.53 -Action Allow New-NetFirewallRule -DisplayName "DNS-out TCP" -Direction Outbound -Protocol TCP -RemotePort 53 -RemoteAddress 10.10.0.53 -Action Allow # Allow HTTPS proxy New-NetFirewallRule -DisplayName "HTTPS-proxy" -Direction Outbound -Protocol TCP -RemotePort 443 -RemoteAddress 10.10.0.80 -Action Allow # Allow NTP New-NetFirewallRule -DisplayName "NTP" -Direction Outbound -Protocol UDP -RemotePort 123 -RemoteAddress 10.10.0.123 -Action Allow
Resolver controls (Unbound example)
server: interface: 0.0.0.0 access-control: 10.0.0.0/8 allow tls-cert-bundle: "/etc/ssl/certs/ca-certificates.crt" qname-minimisation: yes harden-short-bufsize: yes do-ip6: no # Response Policy Zone (RPZ) / local blocklist include: "/etc/unbound/rpz.conf" forward-zone: name: "." forward-tls-upstream: yes forward-addr: 9.9.9.9@853#dns.quad9.net
Force clients to use this resolver (block direct :53 to Internet on edge/SG/NSG). Add RPZ/sinkhole to stop known bad domains.
Detection: DNS tunneling & suspicious egress
| Signal | Why it matters | Example idea |
|---|---|---|
| Very long FQDNs / high entropy labels | Data chunks encoded in subdomains | Alert when len(qname)>=80 or Shannon entropy > threshold |
| Unusual RR types at scale (TXT, NULL) | Common for tunnels | Count TXT queries per host > X/min |
| Excessive NXDOMAIN | Brute-force subdomain probing/tunnels | NXDOMAIN rate per src > baseline |
| First-seen external IP/domain | Beaconing & C2 staging | Maintain first-seen set; alert on new + egress allow |
# Sigma (conceptual): Excessive TXT queries per host
title: Suspicious DNS TXT Query Volume
logsource: { product: dns, service: resolver }
detection:
sel: { qtype: "TXT" }
by_src: selection | count() by src_ip over 5m
condition: by_src >= 200
level: mediumAlso alert when an app subnet attempts outbound SMTP/SSH, or when traffic bypasses the proxy/private endpoints.
Cloud egress patterns
- AWS: SG egress to proxy ENI or Managed Prefix List; use VPC Endpoints/PrivateLink for PaaS.
- Azure: NSG egress → Private Endpoint/App Gateway; use Private DNS zones so PaaS resolves privately.
- GCP: use Cloud NAT + Hierarchical Firewall egress allows; Private Service Connect for PaaS.
Control mapping (quick)
- NIST CSF: PR.AC-5, PR.DS-5, DE.AE-1, DE.AE-2
- NIST 800-53: AC-4, SC-7, SC-18, SI-4 (selection)
- ISO/IEC 27001: Annex A (network security, monitoring, web filtering — map in your SoA)
Use your GRC tool to record the authoritative mappings for your environment.
Zero Trust Segmentation & ZTNA Patterns
Move from flat, IP-based networks to identity-aware segmentation. Combine L3/L4 controls (SG/ACL) with L7 policies (service mesh, proxies) and ZTNA for human access.
Segmentation approaches at a glance
| Approach | What it controls | Good for | Limits |
|---|---|---|---|
| L3/L4 SG/ACL | IP/CIDR, ports, proto | Coarse isolation, blast-radius control, egress pins | IP drift, hard to express identity/app semantics |
| Host firewalls (Windows FW, iptables/nftables) | Per-workload enforcement | East-west control, immutable/base-image rules | Manageability at scale without tooling |
| L7 gateways / reverse proxies | HTTP/TCP policy, authn/z, header claims | Per-service allow-lists, token checks, mTLS termination | Needs consistent identity and app awareness |
| Service mesh (mTLS + AuthZ) | Workload/workload identity, SVID/SANs | Fine-grained, identity-first east-west policy | Sidecars/overhead, operational complexity |
| ZTNA / SDP | Human access via broker | JIT admin, device posture, SSO, short-lived creds | Does not replace workload segmentation |
Kubernetes: NetworkPolicy (namespace to service)
Allow only frontend to reach payment on 8443; default deny elsewhere.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-frontend-to-payment
namespace: payment
spec:
podSelector:
matchLabels: { app: payment }
policyTypes: [Ingress]
ingress:
- from:
- namespaceSelector:
matchLabels: { name: frontend }
ports:
- protocol: TCP
port: 8443Service mesh: mTLS + AuthZ (Istio)
apiVersion: security.istio.io/v1
kind: PeerAuthentication
metadata: { name: mtls-strict, namespace: payment }
spec: { mtls: { mode: STRICT } }
---
apiVersion: security.istio.io/v1
kind: AuthorizationPolicy
metadata: { name: only-frontend, namespace: payment }
spec:
selector: { matchLabels: { app: payment } }
rules:
- from:
- source:
principals: ["spiffe://corp.local/ns/frontend/sa/web"]
to:
- operation: { ports: ["8443"] }Identity is the SPIFFE/SAN of the calling workload, not its IP.
AWS SG example (L3/L4)
# Inbound: only from ALB SG to port 443
aws ec2 authorize-security-group-ingress \
--group-id sg-payment \
--ip-permissions IpProtocol=tcp,FromPort=443,ToPort=443,UserIdGroupPairs=[{GroupId=sg-alb}]
# Egress: only PrivateLink VPCe to DB and logging endpoint
aws ec2 authorize-security-group-egress \
--group-id sg-payment \
--ip-permissions IpProtocol=tcp,FromPort=5432,ToPort=5432,PrefixListIds=[{PrefixListId=pl-DB}]Prefer prefix lists and VPC Endpoints over broad CIDRs.
Host microsegmentation (Linux nftables)
sudo nft add table inet seg
sudo nft add chain inet seg out { type filter hook output priority 0 \; policy drop \; }
sudo nft add rule inet seg out ct state established,related accept
sudo nft add rule inet seg out ip daddr 10.0.20.80 tcp dport 8443 accept # payment API
sudo nft add rule inet seg out ip daddr 10.0.0.53 udp dport 53 accept # DNS
sudo nft add rule inet seg out log prefix \"SEG-DROP \" counter dropBake base rules into the image; manage per-app sets via config mgmt.
Admin access via ZTNA (JIT)
- SSO + device posture → ZTNA broker → short-lived access to a bastion or SSM/IAP.
- Issue SSH certificates with brief TTL instead of static keys.
# Example: sign a short-lived SSH cert (OpenSSH CA) ssh-keygen -t ed25519 -f ~/.ssh/dev -N '' ssh-keygen -s ca_user -I user@corp -n alice -V +10m ~/.ssh/dev.pub
Record commands and session metadata; disable direct SSH from app subnets.
Migrate from flat → segmented (checklist)
- Discover flows: VPC/NSG logs, Zeek, eBPF; baseline by service.
- Default-deny non-prod; add minimal allows; test with synthetic probes.
- Introduce mTLS between tier pairs; pin SAN/SpiffeIDs.
- Translate IP rules → identities (namespaces, service accounts, tags/SGs).
- Instrument: counters, rule-hit metrics; alert on policy bypass.
- Break-glass runbook: time-boxed allow, ticket, post-incident cleanup.
Pitfalls
- Patchy mTLS (some services clear-text internally).
- Implicit egress via NATs that bypass proxies/private endpoints.
- Over-reliance on IPs; no ownership of identity lifecycle (SVID/Cert rotation).
Monitor & map to frameworks
- MITRE Contain Lateral Movement; detect C2 beacons via egress controls.
- NIST 800-53 AC-4, SC-7, SC-12/13, SC-23; NIST CSF PR.AC-5, DE.AE-2.
- KPIs: % workloads in default-deny, mTLS coverage, first-seen egress alerts closed.
Network Telemetry & Detection: Flow Logs, Zeek, IDS/IPS & SIEM
Visibility drives defense. Collect flow (who talks to whom), DNS/HTTP metadata (what they ask for), and deep packet signals where lawful and necessary. Normalize, alert, and hunt through a SIEM or data lake.
Telemetry sources at a glance
| Source | Signal | Use cases | Retention (typ.) |
|---|---|---|---|
| VPC/NetFlow/IPFIX | 5-tuple, bytes/packets, start/stop | East-west mapping, egress anomalies, allow-list drift | 90–180 days (roll-up after 30) |
| DNS logs | Queries, responses, NXDOMAIN, RR types | DGA/beaconing, domain age risk, data exfil (TXT) | 180–365 days (compressed) |
| Proxy/HTTP | URL, method, status, UA, bytes | Malvertising/C2, suspicious uploads, policy enforcement | 90–180 days |
| Zeek | Rich protocol metadata (ssl, http, dhcp…) | Threat hunting, TLS inventory, strange JA3/ALPN | 30–90 days (cold archive later) |
| IDS/IPS (Suricata/Snort) | Signature & anomaly alerts | Known bad detection, lateral movement, exploit attempts | 90–180 days for alerts |
Flow logs: find first-seen egress
Example pseudo-SQL over flow logs to catch new external peers.
SELECT dst_ip, dst_port, COUNT(*) AS hits FROM vpc_flow WHERE action='ACCEPT' AND direction='egress' AND first_seen_ts > now() - interval '24 hours' AND is_internal(dst_ip)=false GROUP BY dst_ip,dst_port ORDER BY hits DESC;
- Create alerts for first-seen domain/IP outside allow-lists.
- Gate risky ports (e.g., 25, 6667, uncommon 22 outbound).
Zeek: TLS inventory
# zeek -r capture.pcap local # Look for legacy TLS or weak params in ssl.log ts, id.orig_h, id.resp_h, version, cipher, ja3, alpn ...
Flag TLSv1.0/1.1, null ciphers, or odd JA3 hashes to hunt C2 families.
Suricata rule (example)
alert dns any any -> any 53 (msg:"Suspicious TXT exfil"; dns.query; content:"TXT"; nocase; threshold:type both, track by_src, count 20, seconds 60; sid:420001; rev:1;)
High TXT volume to rare domains can indicate tunneling/exfiltration.
SIEM hunting: beaconing heuristics
// Pseudocode (translate to your SIEM DSL)
WITH windows AS (
SELECT src_ip, dst_ip, dst_port, bin(60s) AS minute, COUNT(*) AS hits
FROM netflow WHERE direction='egress'
GROUP BY src_ip,dst_ip,dst_port,minute
)
SELECT src_ip, dst_ip, dst_port,
stddev(hits) AS jitter, avg(hits) AS avg_hits, count(*) AS windows
FROM windows
GROUP BY src_ip,dst_ip,dst_port
HAVING jitter < 0.5 AND windows > 20;Low-jitter periodic connections are classic beacon signatures.
Enrichment & scoring
- Tag with geo/ASN/domain age and threat intel (TLP-C).
- Maintain a known-good catalog (SaaS, APIs, registries).
- Auto-quarantine only on strong multi-signal confidence.
Operational checklist
- Enable flow logs on all VPC/VNet/subnets; sample if cost-pressured, but never 0%.
- Forward DNS (resolver) logs and enforce a single egress resolver path.
- Mirror/span critical segments to Zeek/IDS sensors (lawful + approved).
- Normalize to a common schema (ECS/OCSF) before landing in SIEM/lake.
- Define first-seen, rare destination, and data-volume detections.
- Test detections with replay pcaps and red-team beacons; tune thresholds.
Pitfalls
- Collecting everything but retaining nothing useful (no roll-ups/indexing).
- Multiple DNS paths (on-box resolvers) → blind spots in egress monitoring.
- Alert floods without ownership/severity triage (who closes what, when?).
KPIs & frameworks
- Coverage: % subnets with flow + DNS + proxy logs enabled.
- MTTD / MTTR for egress anomalies and known-bad hits.
- MITRE C2 & Exfil (TA0011/TA0010); NIST CSF DE.CM-1/7, DE.AE-1/2.
Applications of Network Security in Cybersecurity
Preventing Distributed Denial of Service (DDoS) Attacks:
- What is a DDoS Attack?: An attacker overwhelms a network or server with a flood of traffic, rendering it unavailable.
- Prevention Techniques:
- Traffic filtering using firewalls and intrusion prevention systems.
- DDoS mitigation services like Cloudflare or Akamai.
- Rate-limiting and traffic shaping to manage load.
Monitoring Network Traffic for Suspicious Activities:
- Tools like Wireshark, Zeek, and Splunk analyze traffic patterns.
- Identify anomalies such as unexpected data flows, port scans, or unauthorized access attempts.
- Use AI-driven tools to detect and respond to emerging threats.
Securing IoT Devices in Networks:
- IoT devices are particularly vulnerable to attacks due to weak security measures.
- Applications:
- Segmenting IoT devices on separate networks.
- Regularly updating firmware and monitoring device behavior.
Enhancing Remote Work Security:
- With the rise of remote work, securing endpoints and connections to corporate networks is crucial.
- VPNs and endpoint security solutions play a key role in protecting sensitive corporate data.
Network Forensics:
- Analyzing network data to investigate cyber incidents and breaches.
- Identifies the source, method, and impact of an attack.
Tools and Technologies for Network Security in Cybersecurity
Firewalls:
Cisco ASA, Palo Alto Networks, Fortinet FortiGate.
Intrusion Detection/Prevention Systems:
Snort, Suricata, McAfee Network Security Platform.
VPN Solutions:
OpenVPN, Cisco AnyConnect, NordVPN for businesses.
Network Monitoring Tools:
SolarWinds Network Performance Monitor, Nagios, Zabbix.
DDoS Protection Services:
Cloudflare, Akamai Kona Site Defender, AWS Shield.
Emerging Trends in Network Security in Cybersecurity
Artificial Intelligence and Machine Learning:
- AI-powered tools for detecting anomalies and automating threat responses.
- Example: AI-driven network intrusion detection systems.
5G Network Security:
- Ensuring the security of high-speed 5G networks used in IoT and edge computing.
Blockchain in Network Security:
- Using decentralized ledger technology for secure communication and transaction validation.
Software-Defined Networking (SDN):
- Centralized management of network resources to improve scalability and security.
Why Study Network Security in Cybersecurity
Protecting the Backbone of Digital Communication
Understanding Key Threats and Defensive Strategies
Learning to Secure Modern and Legacy Network Architectures
Applying Hands-On Skills Through Labs and Simulations
Preparing for Careers in Cybersecurity, IT, and Beyond
Network Security – Frequently Asked Questions
These FAQs introduce the core ideas, tools, and skills behind network security so that students can connect theory about protocols and threats with practical ways to defend modern networks.
What is network security in cybersecurity?
Network security is the practice of protecting the integrity, confidentiality, and availability of data as it travels across or is stored on computer networks. It combines hardware devices, software controls, policies, and monitoring to prevent unauthorised access, misuse, modification, or disruption of network services. Typical measures include firewalls, intrusion detection and prevention systems, secure network protocols, access control, encryption, and continuous monitoring using logs and security analytics. For students, understanding network security provides the foundation for topics such as ethical hacking, secure system design, and incident response in larger cybersecurity architectures.
What are the main types of network security threats?
The main types of network security threats include malware infections, phishing and social engineering, denial-of-service and distributed denial-of-service attacks, man-in-the-middle attacks, and unauthorised access through weak or stolen credentials. Other important threats are eavesdropping on unencrypted traffic, exploitation of software vulnerabilities, misconfigured network devices, and insider misuse of network resources. Many of these threats target both technical weaknesses and human behaviour, so effective network security requires a combination of technical controls, secure configuration, and user awareness. Learning to classify threat types helps students choose appropriate countermeasures and design layered defences that do not rely on any single control.
How do firewalls help protect a network?
Firewalls protect a network by controlling incoming and outgoing traffic based on a defined security policy. They filter packets or connections using rules that consider source and destination addresses, ports, protocols, and sometimes application-level information. Traditional firewalls focus on network and transport layers, while next-generation firewalls add deep packet inspection, intrusion prevention, and application awareness to detect more sophisticated attacks. In practice, firewalls are used to create security zones, limit exposure of internal systems, and enforce the principle of least privilege for network access between segments and to the internet.
What is the difference between IDS and IPS in network security?
An Intrusion Detection System (IDS) monitors network traffic for suspicious patterns and policy violations and alerts security teams when potential attacks are detected. An Intrusion Prevention System (IPS) goes a step further by actively blocking or modifying traffic in real time to prevent malicious activity from reaching its target. Both systems can use signature-based detection, which matches known attack patterns, and anomaly-based detection, which looks for deviations from normal behaviour. Understanding the difference between IDS and IPS helps students reason about where to place controls in a network and how to balance detection accuracy against the risk of blocking legitimate traffic.
Why is network segmentation important for security?
Network segmentation is important because it divides a large network into smaller, isolated segments, limiting how far an attacker or malware can move if a breach occurs. By placing high-value systems, sensitive data, and critical services in protected zones, organisations can apply stricter access controls and monitoring where the risk is highest. Segmentation supports the principle of least privilege by ensuring that users and systems only have network access to the resources they truly need. For students, network segmentation illustrates how good architecture and design can reduce the impact of security incidents even when individual devices or users are compromised.
How do VPNs contribute to network security?
Virtual Private Networks (VPNs) contribute to network security by creating encrypted tunnels between remote users or sites and the organisation’s internal network. This encryption protects data in transit from eavesdropping, tampering, and man-in-the-middle attacks, especially over untrusted networks such as public Wi-Fi. VPNs also enforce authentication, ensuring that only authorised users and devices can establish a secure connection to internal resources. In a broader security architecture, VPNs are often combined with network segmentation, multi-factor authentication, and endpoint protection to secure hybrid and remote access scenarios.
What skills are useful for students who want to specialise in network security?
Students who want to specialise in network security benefit from strong foundations in computer networks, TCP/IP, and common routing and switching technologies. Practical skills include configuring routers, switches, and firewalls; analysing network traffic with tools like Wireshark; and working with VPNs, IDS/IPS, and secure protocols. An understanding of operating systems, scripting for automation, and basic programming helps in writing security rules, processing logs, and building custom detection logic. Soft skills such as documentation, communication, and the ability to translate technical risks into business language are also important for real-world security roles and collaboration with non-technical stakeholders.
Cybersecurity for Networks: Summing Up
Network security is never “done”—it’s a living program that blends layered controls, identity-centric access, high-quality telemetry, and disciplined response. In complex, hybrid environments, the winning posture is Zero-Trust aware: authenticate and authorize every request, encrypt by default, segment aggressively, and assume breach to limit blast radius and dwell time.
- Prevent: least-privilege access, hardened configs, micro-segmentation, strong DNS/TLS hygiene.
- Detect: rich telemetry (DNS/HTTP, flow, IDS), baselines, prioritized alerts mapped to MITRE ATT&CK.
- Respond & recover: practiced runbooks, containment steps, forensics, and measurable RTO/RPO.
Keep iterating: automate routine enforcement, validate with red-team exercises, and fold lessons learned back into policy and architecture. Done well, network security becomes a reliable, auditable fabric that protects data, enables the business, and earns stakeholder trust.
Where to go next: Identity & Access · Cloud Security · Threat Intelligence · Incident Response & Forensics
Cybersecurity for Networks: Simple Review
1. What is network security and why is it essential for modern organizations?
Answer: Network security is the practice of protecting a computer network from intruders, misuse, or theft by employing various technologies and processes. It is essential for modern organizations because it safeguards sensitive information and critical systems from cyber attacks. Effective network security prevents unauthorized access, data breaches, and disruptions to business operations. In addition, it helps ensure regulatory compliance and maintains customer trust by providing a secure digital environment.
2. What are the primary components of a robust network security strategy?
Answer: A robust network security strategy typically includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), encryption, and secure network architecture. These components work together to detect, block, and mitigate cyber threats before they can cause damage. They also provide mechanisms for monitoring, logging, and analyzing network activity to quickly respond to potential incidents. Furthermore, regular updates and policy reviews ensure that the security strategy remains effective against evolving threats.
3. How do firewalls contribute to network security?
Answer: Firewalls act as a critical barrier between trusted internal networks and untrusted external networks by filtering incoming and outgoing traffic based on predefined security rules. They contribute to network security by blocking unauthorized access and preventing potential threats from reaching sensitive systems. Firewalls also help in segmenting networks, thereby isolating vulnerable areas and reducing the spread of infections. Additionally, they provide logging capabilities that enable security teams to monitor and analyze network traffic for suspicious activity.
4. What role do intrusion detection systems (IDS) and intrusion prevention systems (IPS) play in protecting networks?
Answer: Intrusion detection systems (IDS) and intrusion prevention systems (IPS) work together to monitor network traffic for signs of suspicious activity and potential threats. IDS are responsible for detecting anomalies and alerting security personnel, while IPS take it a step further by automatically blocking or mitigating detected threats. These systems help protect networks by providing real-time analysis and immediate responses to potential attacks. As a result, they reduce the risk of data breaches and limit the damage caused by malicious activities.
5. How does encryption help secure network communications?
Answer: Encryption helps secure network communications by converting sensitive data into a coded format that is unreadable to unauthorized users. This ensures that even if data is intercepted during transmission, it remains protected from prying eyes. Encryption is essential for safeguarding confidential information, such as financial data and personal records, during online transactions and communications. Moreover, it plays a key role in maintaining data integrity and trust in digital interactions by preventing unauthorized modifications.
6. What are some common network threats and vulnerabilities that organizations face?
Answer: Organizations face various network threats such as malware, phishing, ransomware, and distributed denial-of-service (DDoS) attacks. Vulnerabilities can arise from misconfigurations, outdated software, weak passwords, and unpatched systems. These threats can compromise data integrity, disrupt business operations, and result in significant financial losses. Consequently, continuous monitoring, regular updates, and comprehensive security measures are critical to mitigating these risks and protecting network infrastructure.
7. How does network segmentation improve overall security posture?
Answer: Network segmentation improves overall security by dividing a large network into smaller, isolated segments. This approach limits the spread of malware and unauthorized access, as a breach in one segment does not necessarily compromise the entire network. It also allows organizations to apply tailored security controls and access policies based on the sensitivity of each segment. By containing potential threats and reducing the attack surface, network segmentation significantly enhances an organization’s resilience against cyber attacks.
8. What is the importance of regular network monitoring and vulnerability assessments?
Answer: Regular network monitoring and vulnerability assessments are crucial because they enable organizations to detect potential security issues before they escalate into serious breaches. Continuous monitoring provides real-time insights into network activity, allowing for rapid response to anomalies and threats. Vulnerability assessments help identify weaknesses in the network infrastructure that could be exploited by attackers. Together, these practices ensure that security measures are up-to-date and that the network remains robust against evolving cyber threats.
9. How do policies and user education contribute to network security?
Answer: Policies and user education contribute to network security by establishing clear guidelines and best practices for safe online behavior. Security policies define acceptable use, access controls, and incident response procedures, ensuring that everyone in the organization understands their responsibilities. User education programs reinforce these policies and help employees recognize and avoid common threats like phishing and social engineering. By fostering a security-aware culture, organizations can significantly reduce the risk of breaches caused by human error.
10. What future trends are expected to shape network security strategies for modern enterprises?
Answer: Future trends in network security are expected to include the increased adoption of artificial intelligence and machine learning, the integration of cloud security solutions, and the expansion of zero-trust architectures. These trends will enable more proactive threat detection and real-time response capabilities. Additionally, the growing number of IoT devices and the increasing complexity of network infrastructures will drive the need for scalable and adaptive security measures. As cyber threats continue to evolve, organizations will need to continuously update their strategies to protect against sophisticated attacks.
Cybersecurity for Networks: Provoking Questions
1. How might the integration of artificial intelligence transform network security defenses in the future?
Answer: Artificial intelligence (AI) has the potential to revolutionize network security defenses by enabling systems to automatically detect, analyze, and respond to threats in real time. AI-driven security tools can analyze vast amounts of network data to identify patterns and anomalies that may indicate malicious activities. This not only improves threat detection accuracy but also reduces the time taken to respond to incidents, allowing for faster mitigation.
The integration of AI will also facilitate predictive analytics, where systems learn from historical attack data to anticipate future threats and adjust defenses proactively. As a result, organizations can transition from reactive to proactive security strategies, creating a dynamic defense system that evolves alongside emerging cyber threats.
2. What impact could quantum computing have on current network encryption methods, and how should organizations prepare?
Answer: Quantum computing poses a significant threat to current encryption methods because it can solve complex mathematical problems much faster than classical computers. This capability could potentially break widely used encryption algorithms such as RSA and ECC, leaving network communications vulnerable to interception and decryption. Organizations need to begin preparing for a post-quantum era by researching and implementing quantum-resistant encryption algorithms.
Preparing for quantum computing involves investing in next-generation cryptographic research and updating security infrastructures to support new protocols. By proactively transitioning to quantum-safe technologies, organizations can ensure that their network security remains robust even as quantum computing becomes more prevalent.
3. In what ways can network segmentation be optimized to enhance both security and operational efficiency?
Answer: Network segmentation can be optimized by strategically dividing the network based on data sensitivity, user roles, and application functions. This approach limits the potential damage of a security breach by confining it to a smaller portion of the network while still allowing seamless communication between segments that require interconnectivity. Effective segmentation involves implementing micro-segmentation, where even individual workloads are isolated, to further reduce the attack surface.
Balancing security and operational efficiency requires careful planning to avoid excessive fragmentation that could hinder business processes. Organizations should leverage software-defined networking (SDN) solutions to dynamically manage and adjust network segments as needed, ensuring that both security and performance are maintained.
4. How might the rise of IoT devices challenge traditional network security models, and what innovative solutions could address these challenges?
Answer: The proliferation of IoT devices significantly expands the network’s attack surface, as these devices often have limited processing power and may lack robust security measures. Traditional network security models, which were designed for fewer, more homogeneous endpoints, may struggle to accommodate the diversity and scale of IoT environments. This challenge necessitates innovative solutions such as lightweight encryption, continuous monitoring, and specialized IoT security gateways that can manage the unique vulnerabilities of these devices.
Innovative solutions could also involve the integration of AI and machine learning to monitor IoT behavior and detect anomalies in real time. By implementing comprehensive IoT security frameworks that include device authentication, secure firmware updates, and network segmentation, organizations can effectively mitigate the risks posed by the increasing number of connected devices.
5. What role does user behavior analytics play in modern network security, and how can organizations leverage it to improve defenses?
Answer: User behavior analytics (UBA) plays a critical role in modern network security by analyzing patterns in user activity to detect unusual or suspicious behavior that may indicate a breach. By monitoring and modeling normal behavior, UBA systems can quickly identify deviations that could signify compromised credentials or insider threats. This proactive approach enables organizations to intervene before potential attacks cause significant harm.
Organizations can leverage UBA by integrating it with their existing security information and event management (SIEM) systems to provide a comprehensive view of network activity. Continuous analysis of user behavior allows security teams to fine-tune access controls, detect emerging threats, and implement targeted security measures, thereby enhancing overall network resilience.
6. How can continuous network monitoring transform incident response strategies in large-scale enterprises?
Answer: Continuous network monitoring transforms incident response strategies by providing real-time visibility into network traffic and system behavior. This constant surveillance enables organizations to detect anomalies and potential security incidents as they occur, allowing for immediate action to contain and mitigate threats. By automating data collection and analysis, continuous monitoring reduces the time to detect incidents, which is crucial for minimizing damage and recovery costs.
For large-scale enterprises, continuous monitoring supports a proactive approach where incident response teams can use detailed, real-time data to rapidly identify the source of a breach and implement countermeasures. This strategy not only enhances operational efficiency but also strengthens the overall security posture by enabling swift and informed decision-making during crises.
7. What are the potential benefits and risks of adopting a zero-trust network security model, and how might organizations implement it effectively?
Answer: The zero-trust network security model offers significant benefits by assuming that no user or device, whether inside or outside the network, is inherently trustworthy. This approach requires continuous verification of every access request, which minimizes the risk of unauthorized access and lateral movement within the network. Implementing zero-trust can greatly enhance security by enforcing strict access controls and segmenting the network to limit potential damage from breaches.
However, adopting a zero-trust model also presents challenges such as increased complexity in managing continuous authentication and potential disruptions to user productivity. Organizations must carefully design and implement zero-trust architectures, ensuring that security measures are balanced with usability. Effective implementation involves robust identity management, continuous monitoring, and clear policies that guide access decisions, thereby maximizing benefits while mitigating associated risks.
8. How might advancements in cloud security influence network security architectures, and what are the key considerations for integrating these solutions?
Answer: Advancements in cloud security are reshaping network security architectures by introducing scalable, dynamic, and centralized security solutions that can protect data and applications hosted in the cloud. These advancements enable organizations to monitor and secure network traffic across hybrid environments, blending on-premises and cloud-based infrastructures. Key considerations for integrating cloud security solutions include ensuring interoperability between different platforms, maintaining data sovereignty, and enforcing consistent security policies across all environments.
Additionally, organizations must evaluate the risk profiles of their cloud services and implement multi-layered security measures such as encryption, access controls, and continuous monitoring. By adopting cloud-centric security architectures, enterprises can enhance their overall defense capabilities, streamline management, and respond more effectively to evolving threats.
9. In what ways can incident response teams improve collaboration with digital forensics experts to enhance post-incident analysis?
Answer: Incident response teams can improve collaboration with digital forensics experts by establishing clear communication channels and integrating their workflows from the outset of an incident. Joint training sessions, shared tools, and coordinated response protocols help ensure that both teams work together seamlessly to capture, analyze, and preserve critical evidence. This collaboration enables a more comprehensive understanding of the incident, allowing for more effective remediation and improved preventive measures in the future.
Moreover, regular debriefings and post-incident reviews involving both incident response and forensic teams can help identify lessons learned and refine processes. By fostering a culture of cooperation and continuous improvement, organizations can enhance their ability to respond to and recover from cyber incidents, ultimately strengthening their overall security posture.
10. How could emerging technologies such as blockchain and distributed ledger systems be utilized to enhance the integrity of forensic evidence?
Answer: Emerging technologies like blockchain and distributed ledger systems can enhance the integrity of forensic evidence by providing an immutable and transparent record of data collection and handling. These technologies ensure that once evidence is recorded, it cannot be altered or tampered with, thereby preserving its authenticity for legal and investigative purposes. This enhanced integrity is crucial for maintaining a reliable chain of custody and ensuring that forensic findings are admissible in legal proceedings.
Furthermore, integrating blockchain technology with digital forensics can automate and secure the evidence management process, reducing the risk of human error. By providing real-time audit trails and verifiable logs, blockchain-based systems improve accountability and trust in the forensic process, paving the way for more robust and defensible investigations.
11. What strategies can organizations adopt to balance rapid incident response with the need for thorough forensic analysis in high-pressure situations?
Answer: Organizations can adopt a dual-track approach that separates immediate containment efforts from in-depth forensic analysis. Rapid incident response teams should focus on quickly isolating affected systems and mitigating damage, while specialized forensic teams work concurrently to collect and preserve evidence without interrupting the containment process. This separation of duties ensures that critical evidence is not compromised and that immediate risks are addressed efficiently.
Implementing automation tools for preliminary data collection can also accelerate the forensic process without delaying the overall incident response. By establishing clear protocols and communication channels between response and forensic teams, organizations can maintain a balance between swift action and comprehensive analysis, ensuring both immediate protection and long-term security improvements.
12. How might the evolution of regulatory requirements shape the future practices of incident response and digital forensics?
Answer: The evolution of regulatory requirements is likely to drive incident response and digital forensics toward more standardized, transparent, and accountable practices. As governments and international bodies impose stricter data protection and breach notification laws, organizations will need to develop more rigorous incident response plans and forensic methodologies that comply with these standards. This evolution will encourage the adoption of advanced technologies, such as AI-driven analytics and blockchain-based evidence logging, to ensure that investigations are both efficient and legally sound.
Future practices may also involve greater collaboration between public and private sectors to establish best practices and unified frameworks for incident response. As regulations become more comprehensive, organizations that proactively align their forensic and response capabilities with these requirements will be better positioned to mitigate legal risks, enhance trust, and build a resilient cybersecurity infrastructure.
Cybersecurity for Networks: Master the Numbers
1. A company experiences 200 network intrusion attempts per day. If its security system blocks 98% of these attempts, calculate the number of blocked attempts per day, the number of successful intrusions, and the annual successful intrusion count.
Solution:
• Step 1: Blocked attempts per day = 200 × 0.98 = 196.
• Step 2: Successful intrusions per day = 200 – 196 = 4.
• Step 3: Annual successful intrusions = 4 × 365 = 1,460 intrusions.
2. A firewall processes 500,000 packets per minute. If a DDoS attack increases traffic by 150%, calculate the new packet rate per minute, the total extra packets per hour, and the extra packets per day.
Solution:
• Step 1: Increased packet rate = 500,000 × 1.50 = 750,000 packets per minute (extra = 750,000 – 500,000 = 250,000 extra packets per minute).
• Step 2: Extra packets per hour = 250,000 × 60 = 15,000,000 packets.
• Step 3: Extra packets per day = 15,000,000 × 24 = 360,000,000 packets.
3. A network monitoring system logs 2,000 events per minute. If 0.25% of these events are flagged as critical, calculate the number of critical events per minute, per hour, and per day.
Solution:
• Step 1: Critical events per minute = 2,000 × 0.0025 = 5 events.
• Step 2: Critical events per hour = 5 × 60 = 300 events.
• Step 3: Critical events per day = 300 × 24 = 7,200 events.
4. An intrusion detection system (IDS) has a false positive rate of 0.5% over 1,000,000 events. Calculate the number of false positives, then determine the number if an upgrade reduces the false positive rate by 80%, and finally compute the total reduction.
Solution:
• Step 1: False positives = 1,000,000 × 0.005 = 5,000.
• Step 2: New false positive rate = 0.5% × (1 – 0.80) = 0.1%; new false positives = 1,000,000 × 0.001 = 1,000.
• Step 3: Total reduction = 5,000 – 1,000 = 4,000 fewer false positives.
5. A network security tool scans 10,000 IP addresses in 30 minutes. Calculate the scanning rate per minute, the time required to scan 100,000 IP addresses, and the percentage increase in time if the scanning speed drops by 20%.
Solution:
• Step 1: Scanning rate = 10,000 ÷ 30 ≈ 333.33 IPs per minute.
• Step 2: Time for 100,000 IPs = 100,000 ÷ 333.33 ≈ 300 minutes.
• Step 3: With a 20% slower speed, new time = 300 × 1.20 = 360 minutes; percentage increase = 20%.
6. A secure network uses 256-bit encryption. Estimate the total number of possible keys and then calculate the brute-force time if 10^9 keys can be tested per second, finally converting that time into years using 3.15×10^7 seconds per year.
Solution:
• Step 1: Total keys = 2^256 (an extremely large number).
• Step 2: Brute-force time in seconds = 2^256 ÷ 10^9.
• Step 3: Converting to years = (2^256 ÷ 10^9) ÷ 3.15×10^7; result is astronomically high, indicating impracticality of brute-force attacks.
7. A network segmentation project divides a network into 8 segments, reducing lateral movement by 70%. If an initial breach could affect 1,000 devices, calculate the potential devices affected after segmentation, and determine the reduction in percentage.
Solution:
• Step 1: Without segmentation, breach affects 1,000 devices.
• Step 2: With 70% reduction, affected devices = 1,000 × 0.30 = 300 devices.
• Step 3: Reduction = 1,000 – 300 = 700 devices; percentage reduction = (700 ÷ 1,000) × 100 = 70%.
8. A network security audit finds 120 vulnerabilities in a system. If a remediation plan fixes 85% of them, calculate the number of fixed vulnerabilities, the number remaining, and the overall reduction percentage.
Solution:
• Step 1: Fixed vulnerabilities = 120 × 0.85 = 102.
• Step 2: Remaining vulnerabilities = 120 – 102 = 18.
• Step 3: Reduction percentage = (102 ÷ 120) × 100 = 85%.
9. A network monitoring tool generates 800,000 logs per day. If an AI system improves threat detection and flags 0.1% of logs as potential threats, calculate the number of flagged logs per day, per week (7 days), and per month (30 days).
Solution:
• Step 1: Flagged logs per day = 800,000 × 0.001 = 800 logs.
• Step 2: Per week = 800 × 7 = 5,600 logs.
• Step 3: Per month = 800 × 30 = 24,000 logs.
10. A firewall upgrade reduces network latency by 15% from an initial 100 ms latency. Calculate the new latency, the time saved per 1,000 requests, and the total time saved for 1,000,000 requests.
Solution:
• Step 1: New latency = 100 ms × (1 – 0.15) = 85 ms.
• Step 2: Time saved per request = 100 – 85 = 15 ms; for 1,000 requests = 15,000 ms = 15 seconds.
• Step 3: For 1,000,000 requests = 15 × 1,000 = 15,000 seconds saved.
11. A network access control system enforces policies on 5,000 devices, reducing unauthorized access attempts by 90%. If initially there were 2% unauthorized attempts per device per day, calculate the number of unauthorized attempts before and after enforcement and the total daily reduction.
Solution:
• Step 1: Unauthorized attempts per day before = 5,000 × 0.02 = 100 attempts.
• Step 2: After a 90% reduction, attempts per day = 100 × (1 – 0.90) = 10 attempts.
• Step 3: Total daily reduction = 100 – 10 = 90 fewer attempts.
12. An incident response drill reduces recovery time from 50 minutes to 20 minutes per incident. If an organization conducts 12 drills per year, calculate the total time saved annually in minutes, then convert that to hours.
Solution:
• Step 1: Time saved per drill = 50 – 20 = 30 minutes.
• Step 2: Total time saved annually = 30 × 12 = 360 minutes.
