Cloud Security Education teaches a kind of clarity that modern systems demand: you may not own the cloud’s hardware, but you still own the consequences of how you configure it. The diagram lays out that transformation. Learners arrive with inputs—concepts, examples, and a foundation in IT—but their learning is shaped by controls: policies, governance requirements, and compliance rules that force security to be more than good intentions. With mechanisms such as guided labs and real security tools, students practice the actions that actually protect systems: setting least-privilege access, securing identities, encrypting data, monitoring logs and alerts, and designing for resilience when something goes wrong. The output is practical capability—learners who can build and operate cloud resources in a way that is auditable, explainable, and responsibly defended, rather than merely “working.
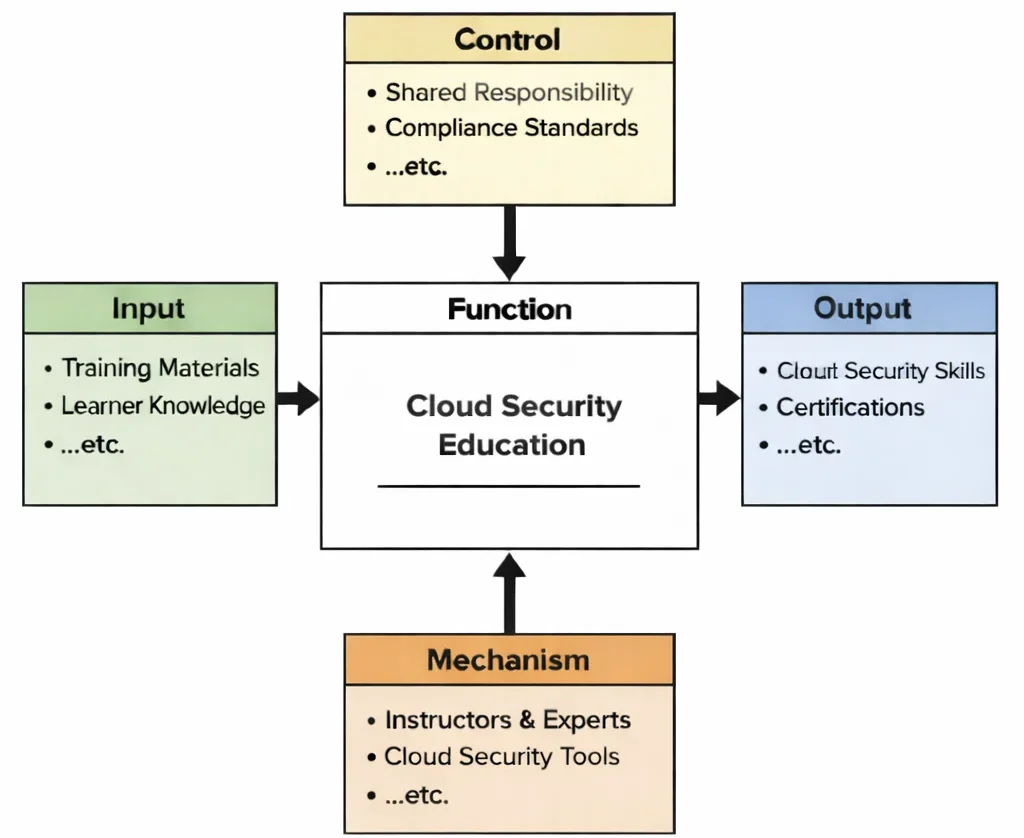
This IDEF0 (Input–Control–Output–Mechanism) diagram summarizes Cloud Security Education as a structured transformation. Inputs include training resources and learner baseline knowledge. Controls include security policies, governance rules, compliance expectations, and curriculum outcomes that define what “secure cloud” means in practice. Mechanisms such as instructors, experts, security tooling, and lab environments enable hands-on learning with identity, access control, monitoring, encryption, and incident response basics. Outputs include learners who can apply cloud security principles, configure protective controls, interpret security signals, and make defensible trade-offs between risk, usability, and cost.
Cloud security is now a core part of modern cybersecurity. Moving from on-prem to the cloud creates new risks—shared infrastructure, multi-tenant data, and fast-changing services. To manage them, combine security, compliance, and identity management with the fundamentals of cybersecurity and cryptography.
Cloud-native tech such as serverless and containers improves speed and scale, but it also demands tighter controls. Keep configurations reliable by baking checks into DevOps and Infrastructure as Code, and validate choices with sensible performance tuning.
Strong identity and access management is non-negotiable: least privilege, MFA, and short-lived credentials. Pair that with threat intelligence and behavior analytics to spot misuse quickly and prevent credential-based attacks.
AI and ML help detect anomalies in real time and predict risk. When issues do occur, well-rehearsed incident response and forensics turn alerts into fast, compliant action.
New patterns—like edge computing and richer cloud networking—boost performance but also widen the attack surface. Secure them with the same rigor you apply to core cloud services.
Protecting cloud apps means aligning with application security and understanding nearby systems such as cyber-physical and OT. Don’t forget the basics in hybrid setups: endpoint and network security.
People and process matter. Build security awareness, enforce clear policies, and use ethical hacking to test defenses before attackers do.
Stay ahead by tracking emerging areas and applying insights from data science and big-data analytics. Aim for automated, scalable defenses that match the speed and change of the cloud.

This image visualizes cloud security as a protected “core” inside a busy data-center environment. A luminous cloud symbol with a padlock hovers in the middle, implying encrypted storage and controlled access to cloud resources. On both sides, tall server racks suggest large-scale infrastructure, while floating shield icons and authentication-style symbols represent key defenses such as identity and access management, encryption, secure configuration, and continuous threat detection. The radiating lines and digital glow convey always-on vigilance—systems that watch, verify, and respond in real time to keep cloud platforms trustworthy for users and organizations.
Table of Contents
Cloud Account Hardening: 12-Step Quickstart
- Secure the root/org account – enable MFA for root, restrict root API keys, use break-glass only.
- Centralize identity – connect SSO; use roles over long-lived users; rotate creds automatically.
- Least-privilege IAM – start from deny-by-default; grant time-bound roles; review access monthly.
- Default encryption – turn on at-rest encryption for storage, DBs, and backups; enforce TLS in transit.
- Key & secret management – managed KMS for keys; managed vault for app secrets; never store in code.
- Network segmentation – private subnets/endpoints; WAF on public apps; minimal inbound rules.
- Logging & audit – enable control-plane and data-plane logs; keep immutable copies in a central account.
- Secure CI/CD – scan dependencies, images, and IaC; sign artifacts; generate SBOM; policy gates pre-deploy.
- Harden workloads – minimal base images; patch regularly; runtime sensors/EDR for VMs & containers.
- Detection & alerts – watch for role changes, key use, public buckets, anomalous network paths.
- Backups & DR – encrypted, tested restores; cross-region copies for critical data/services.
- Continuous posture – run CSPM/CNAPP; fix critical misconfigs fast; report time-to-remediate.
Top Cloud Misconfigurations (and Fast Fixes)
| Misconfiguration | Why it’s risky | Fast fix |
|---|---|---|
| Public object storage | Data exposure and ransomware staging | Block public access at account level; use bucket policies with allow-lists only. |
| Over-privileged roles | Lateral movement, data exfiltration | Replace wildcards; split duties; add time-bound elevation with approvals. |
| Long-lived access keys | Credential theft & resale | Rotate to short-lived, role-based access; monitor key creation/use events. |
| Unencrypted DB/snapshots | Data theft from backups | Enable default encryption; re-encrypt old snapshots; restrict snapshot sharing. |
| Flat VPC/VNet | Large blast radius | Segment by environment & tier; private endpoints; deny-by-default SG/NSG rules. |
| Open admin ports | Brute force & exploits | Close 22/3389 to internet; require VPN/bastion; JIT access with approvals. |
| Secrets in code/images | Instant compromise if leaked | Scan repos & images; move to a secrets manager; rotate exposed secrets. |
| No log retention | No forensics or detection | Centralize logs, set immutable retention, alert on logging gaps. |
Monitoring & Detection Watchlist
- Identity: new admin roles, policy changes, failed MFA spikes, unexpected token issuers.
- Keys & secrets: new access keys, unusual key use, vault access outside business hours.
- Storage & data: bucket/container made public, snapshot sharing, cross-region egress bursts.
- Network: sudden open inbound rules, WAF spikes, east-west traffic surges.
- Workloads: image drift, unsigned artifacts, container exec/privileged pods, unexpected process tree.
- Control plane: API calls from new geos, disabled logging, detector tampering.
Cloud Security – Quick Glossary
CSPM: Cloud Security Posture Management – finds misconfigurations across accounts.
CWPP: Cloud Workload Protection Platform – protects VMs/containers at runtime.
CNAPP: End-to-end posture + workload security across build and runtime.
SBOM: Software Bill of Materials – inventory of components in an image/application.
Key Topics in Cloud Security
Identity and Access Management (IAM) for Cloud Platforms:
- What It Does:
- Ensures that only authorized individuals and systems can access cloud resources.
- Key Practices:
- Implementing Role-Based Access Control (RBAC) to restrict access based on user roles.
- Using Multi-Factor Authentication (MFA) for enhanced security.
- Managing access keys, tokens, and API keys securely.
- Tools:
- AWS IAM, Azure Active Directory, Google Cloud IAM.
- Example:
- Assigning least-privilege access to developers, ensuring they can only access the resources necessary for their tasks.
- What It Does:
Protecting Cloud Storage and Databases:
- What It Involves:
- Safeguarding cloud storage and databases from unauthorized access, data breaches, and misconfigurations.
- Best Practices:
- Enforcing access control policies and logging all access attempts.
- Encrypting sensitive data stored in cloud databases.
- Regularly auditing storage configurations to prevent public exposure of data (e.g., unsecured S3 buckets).
- Tools:
- Amazon S3 bucket policies, Google Cloud Storage permissions, Azure Blob Storage access control.
- Example:
- Preventing misconfigured cloud storage from being exposed to the public internet.
- What It Involves:
Encryption of Data at Rest and In Transit:
- What It Involves:
- Encrypting data to ensure that it is secure during storage and while being transmitted.
- Data at Rest:
- Protects stored data using encryption standards like AES-256.
- Data in Transit:
- Encrypts data during transmission using protocols like TLS (Transport Layer Security) or HTTPS.
- Best Practices:
- Automating key rotation and management.
- Using services like AWS KMS, Azure Key Vault, or Google Cloud Key Management Service.
- Example:
- Encrypting customer payment information in e-commerce databases and ensuring secure payment transactions.
- What It Involves:
Applications of Cloud Security
Securing Multi-Cloud and Hybrid Cloud Environments:
- What It Entails:
- Protecting workloads and data that span across multiple cloud providers and on-premises environments.
- Challenges:
- Consistent security policies across platforms.
- Managing access and identities in diverse environments.
- Best Practices:
- Using unified security tools and dashboards to monitor and manage security across platforms.
- Employing container security solutions for hybrid deployments (e.g., Kubernetes security tools).
- Tools:
- Cloud Security Posture Management (CSPM) tools like Prisma Cloud or Dome9.
- Example:
- Monitoring security configurations across AWS, Azure, and GCP to ensure compliance with organizational policies.
- What It Entails:
Compliance with Regulations Like GDPR and HIPAA for Cloud Data:
- Why It’s Important:
- Organizations using cloud services must comply with regulations to avoid penalties and ensure customer trust.
- Compliance Requirements:
- GDPR: Protects personal data of EU citizens; mandates encryption and access control for stored data.
- HIPAA: Governs healthcare data, requiring strict security measures for protected health information (PHI).
- PCI DSS: Regulates payment card data security.
- Steps to Ensure Compliance:
- Conducting regular audits of cloud environments.
- Using encryption for sensitive data and maintaining access logs.
- Partnering with cloud providers that offer compliance certifications.
- Example:
- A healthcare organization ensuring its data stored in Azure complies with HIPAA by encrypting PHI and managing access controls.
- Why It’s Important:
Tools and Technologies in Cloud Security
Identity & Access Management (IAM)
- AWS IAM & IAM Identity Center, Microsoft Entra ID (Azure AD), Google Cloud IAM
- Okta, Auth0 (customer identity), policy-as-code (OPA)
Key Management, Secrets & Encryption
- AWS KMS, Azure Key Vault, Google Cloud KMS
- HashiCorp Vault (secrets), envelope encryption & HSM integrations
Posture & Configuration Management (CSPM)
- AWS Config & Security Hub, Microsoft Defender for Cloud, Google Security Command Center
- Wiz, Prisma Cloud, Orca, Lacework (multi-cloud visibility & misconfig detection)
Workload & Runtime Protection (CWPP / CNAPP)
- Amazon GuardDuty, Azure Defender plans, GCP Threat Detection
- Sysdig/Falco, Prisma Cloud Defender, Aqua, CrowdStrike (runtime anomaly & EDR for cloud)
Containers & Kubernetes Security
- Image scanning: Trivy, Anchore/Grype, Clair
- Admission & policy: OPA Gatekeeper, Kyverno
- Signing/SBOM: Cosign (Sigstore), Syft
- Managed K8s controls in EKS / AKS / GKE
Application & API Protection (WAAP)
- AWS WAF, Azure WAF, Google Cloud Armor, Cloudflare WAF
- API gateways & posture: API Gateway, Apigee, Kong
DDoS & Edge Security
- AWS Shield (Standard/Advanced), Azure DDoS Protection, Google Cloud Armor
- Cloudflare (network & L7 protections)
Monitoring, Logging, SIEM & SOAR
- Cloud logs/metrics: CloudTrail & CloudWatch (AWS), Azure Monitor, Cloud Logging/Monitoring (GCP)
- SIEM/SOAR: Microsoft Sentinel, Google Chronicle, Splunk
CI/CD & Supply-Chain Security
- SCA & IaC scanning: Snyk, Mend, Checkov, tfsec
- Container scanning & policies: Trivy, Prisma Cloud, Aqua
- Artifact signing & SBOM: Cosign, Syft
Data Protection & Governance
- S3/Blob/Object storage encryption & access policies
- Data discovery/DLP: Amazon Macie, Microsoft Purview, Google DLP
Emerging Trends in Cloud Security
Zero Trust Security for the Cloud:
- What It Entails:
- Adopting the “never trust, always verify” principle.
- Key Practices:
- Continuous authentication and monitoring.
- Micro-segmentation of cloud networks to limit the blast radius of breaches.
- What It Entails:
Cloud-Native Security Tools:
- Examples:
- AWS GuardDuty: Threat detection for AWS workloads.
- Azure Security Center: Centralized security management.
- Google Cloud Security Command Center: Provides visibility into security posture.
- Examples:
Serverless Security:
- Securing serverless architectures where the cloud provider manages the infrastructure.
- Key Concerns:
- Ensuring secure function configurations.
- Monitoring for over-permissioned functions.
Security through Artificial Intelligence and Machine Learning:
- AI-driven tools for threat detection and response.
- Examples:
- Detecting unusual cloud activity with machine learning algorithms.
- Automating incident response to reduce manual effort.
Challenges in Cloud Security
Shared Responsibility Model:
- What It Means:
- Cloud providers secure the infrastructure, but customers are responsible for securing their data and applications.
- Example:
- While AWS secures its data centers, the user must configure security for their applications hosted on AWS.
- What It Means:
Misconfigurations:
- Misconfigured cloud resources (e.g., public-facing databases) are a leading cause of breaches.
- Solution:
- Regular configuration audits using tools like AWS Config or Terraform.
Data Residency and Sovereignty:
- Some regulations require that data remain within specific geographic locations.
- Solution:
- Use region-specific cloud services and maintain awareness of local laws.
Tools for Cloud Security
Identity and Access Management:
- AWS IAM, Azure Active Directory, Google Cloud IAM.
Cloud Security Posture Management (CSPM):
- Prisma Cloud, Dome9, AWS Config.
Data Encryption and Key Management:
- AWS KMS, Azure Key Vault, Google Cloud KMS.
Threat Detection:
- AWS GuardDuty, Azure Sentinel, Google Cloud SCC.
Compliance Monitoring:
- CloudCheckr, Rapid7, Splunk.
Benefits of Cloud Security
Protects Sensitive Data:
Prevents unauthorized access, data breaches, and loss of intellectual property.
Ensures Business Continuity:
Safeguards against disruptions caused by cyberattacks.
Enables Innovation:
Secure cloud environments allow organizations to adopt cloud-native technologies confidently.
Maintains Regulatory Compliance:
Reduces legal and financial risks associated with non-compliance.
Why Study Cloud Security
Protecting Data and Services in the Cloud Era
Understanding Shared Responsibility and Security Models
Exploring Threats Unique to Cloud Environments
Applying Practical Security Tools and Frameworks
Preparing for Careers in Cloud and Cybersecurity
Cloud Security: FAQs
What is the shared responsibility model?
Cloud providers secure the cloud (infrastructure and managed services). You secure what you configure and run: identities, data, networks, workloads, and code.
What are the first controls to put in place?
Least-privilege IAM with MFA, short-lived credentials, default encryption for storage/databases, centralized logging, and deny-by-default network rules.
How do we secure CI/CD and the supply chain?
Scan dependencies and images, scan IaC, sign artifacts, generate an SBOM, enforce policy gates before deploy, and keep secrets out of code in a managed vault.
Do containers and serverless change security?
Yes—adopt image scanning, admission/Pod policies, runtime detection for containers, and least-privilege roles plus per-function secrets for serverless.
What should we monitor in the cloud?
Control-plane API calls (role changes, key use), public exposure of storage, unusual network paths, auth failures, and runtime anomalies—tied to an incident response plan.
Cloud Security: Conclusion
Cloud security is a critical aspect of modern cybersecurity strategies. As organizations increasingly rely on cloud environments, implementing robust security measures ensures data protection, compliance, and resilience against evolving threats.
Cloud Security: Exercise Questions
Review Questions and Answers:
1. What is cloud security and why is it critical in modern IT environments?
Answer: Cloud security refers to the practices, technologies, and policies implemented to protect data, applications, and infrastructure in cloud environments. It is critical because as organizations increasingly rely on cloud services, they expose sensitive information to a broader range of threats that require specialized protection. Effective cloud security mitigates risks associated with data breaches, unauthorized access, and cyberattacks by ensuring robust protection at every layer of the cloud stack. By adopting comprehensive security measures, organizations can maintain business continuity, protect user privacy, and comply with regulatory standards.
2. What are the key components of an effective cloud security strategy?
Answer: An effective cloud security strategy typically includes a multi-layered approach that integrates encryption, identity and access management, continuous monitoring, and threat detection systems. These components work in tandem to protect data both in transit and at rest, ensure that only authorized users have access, and continuously scan for potential vulnerabilities. A robust strategy also involves regular security audits and compliance checks to adapt to emerging threats and changing regulatory requirements. By combining technical controls with proactive governance, organizations can build a resilient defense against cyber threats in the cloud.
3. How does encryption contribute to cloud security?
Answer: Encryption transforms data into an unreadable format that can only be accessed with the proper decryption key, thus protecting sensitive information from unauthorized access. In cloud security, encryption is applied both to data at rest and data in transit, ensuring comprehensive protection throughout the data lifecycle. This measure helps safeguard confidential information even if other security layers are breached, reducing the risk of data theft and misuse. Overall, encryption is a foundational technology that supports data integrity, privacy, and compliance with various regulatory standards.
4. What role does identity management play in ensuring secure cloud access?
Answer: Identity management in cloud security involves the systematic control of user access to digital resources through authentication, authorization, and auditing processes. It ensures that only verified and authorized individuals can access sensitive data and applications, thereby reducing the risk of unauthorized access. Effective identity management utilizes techniques like multi-factor authentication and role-based access control to enforce strict access policies. This not only protects cloud assets from internal and external threats but also simplifies compliance with industry regulations by maintaining detailed records of access activities.
5. How do compliance requirements influence cloud security practices?
Answer: Compliance requirements dictate that cloud security practices adhere to established legal and regulatory standards to protect sensitive data and ensure privacy. These requirements drive organizations to implement robust security controls such as encryption, regular audits, and strict access management policies. Adhering to compliance standards helps prevent legal penalties, enhances customer trust, and ensures that security measures are both effective and transparent. As regulatory environments evolve, cloud security practices must be continuously updated to meet these stringent requirements and mitigate emerging risks.
6. What common cyber threats target cloud environments and how can they be mitigated?
Answer: Common cyber threats to cloud environments include malware, phishing attacks, ransomware, DDoS attacks, and insider threats. Mitigation strategies involve a multi-layered defense approach that includes advanced threat detection, robust firewalls, intrusion prevention systems, and comprehensive encryption techniques. Regular vulnerability assessments, employee training, and continuous monitoring further enhance the ability to detect and respond to these threats. By proactively addressing potential vulnerabilities and maintaining up-to-date security measures, organizations can effectively reduce the risk of cyberattacks on their cloud infrastructure.
7. How does continuous monitoring improve the security of cloud systems?
Answer: Continuous monitoring improves cloud security by providing real-time visibility into network activities, user behaviors, and system performance, which enables the early detection of anomalies and potential threats. This constant surveillance allows security teams to respond promptly to incidents, reducing the window of opportunity for attackers. By integrating automated alerts and analytics, continuous monitoring also supports proactive risk management and helps maintain compliance with security policies. Overall, this approach ensures that cloud systems remain resilient and can quickly adapt to emerging threats.
8. What are the challenges of securing cloud infrastructures, and how can organizations overcome them?
Answer: Securing cloud infrastructures poses challenges such as multi-tenancy risks, data visibility issues, and the complexity of managing distributed environments. Organizations must contend with ensuring consistent security controls across various cloud services and geographic regions, which can be difficult due to differing policies and configurations. To overcome these challenges, businesses can adopt a shared responsibility model, use centralized management tools, and enforce strict security protocols across all cloud platforms. Regular training, continuous monitoring, and robust encryption practices further help mitigate these challenges and enhance overall cloud security.
9. How can application security be integrated into cloud security strategies?
Answer: Application security can be integrated into cloud security strategies by embedding secure coding practices, regular vulnerability assessments, and automated testing throughout the software development lifecycle. This integration ensures that applications deployed in the cloud are resilient against threats such as SQL injection, cross-site scripting, and other common vulnerabilities. By incorporating security into the development process and leveraging tools like static and dynamic code analysis, organizations can identify and remediate vulnerabilities early. This proactive approach not only protects the application but also contributes to the overall security of the cloud environment.
10. What future trends are expected to shape cloud security, and why are they significant?
Answer: Future trends in cloud security include the adoption of artificial intelligence and machine learning for real-time threat detection, the implementation of zero-trust architectures, and the advancement of quantum-resistant encryption methods. These trends are significant because they address the evolving nature of cyber threats and the increasing complexity of cloud environments. As attackers become more sophisticated, AI-driven security measures and zero-trust models provide proactive and adaptive defenses that are essential for protecting digital assets. These innovations will redefine best practices in cloud security, ensuring robust protection and resilience in the face of emerging challenges.
Cloud Security: Thought-Provoking Questions and Answers
1. How might the integration of AI and machine learning revolutionize cloud security strategies in the future?
Answer: The integration of AI and machine learning into cloud security strategies has the potential to revolutionize how threats are detected and mitigated. AI algorithms can analyze vast amounts of data in real time, identifying subtle patterns and anomalies that may indicate an attack, often much faster than human analysts. This capability enables a proactive approach to security, where potential breaches can be anticipated and prevented before they cause significant harm. Furthermore, as these technologies evolve, they can continuously adapt to new threat vectors, ensuring that security measures remain robust in a rapidly changing digital landscape.
AI-driven systems can also automate many routine security tasks, such as patch management, log analysis, and incident response, thereby reducing the burden on IT teams and improving overall efficiency. This not only accelerates the response to threats but also frees up resources for strategic security initiatives. In essence, the integration of AI and machine learning can lead to smarter, more adaptive cloud security frameworks that are capable of addressing both current and emerging cyber risks.
2. What are the potential benefits and drawbacks of implementing a zero-trust model in cloud security?
Answer: Implementing a zero-trust model in cloud security can offer significant benefits, such as enhanced protection against unauthorized access and improved visibility into user activities. By assuming that no user or device is inherently trustworthy, the zero-trust model enforces strict authentication and continuous verification, thereby reducing the risk of internal and external breaches. This approach enhances data security by limiting lateral movement within the network and ensuring that access to sensitive resources is granted on a need-to-know basis. However, the transition to a zero-trust model can also introduce challenges, such as increased complexity in managing access controls and potential disruptions during the implementation phase.
Organizations may face resistance from employees accustomed to traditional security models, and integrating zero-trust principles with existing infrastructure may require significant investment in new technologies and training. To overcome these challenges, a phased implementation strategy and clear communication of the benefits are essential. Despite the initial complexities, the long-term security advantages and improved risk management offered by a zero-trust model make it a compelling approach for modern cloud environments.
3. How can organizations ensure robust data protection in cloud environments while maintaining user accessibility and performance?
Answer: Ensuring robust data protection in cloud environments while maintaining user accessibility and performance requires a balanced approach that incorporates strong encryption, access controls, and efficient network architectures. Organizations can implement end-to-end encryption for data both at rest and in transit, ensuring that sensitive information remains secure even if intercepted. Coupling this with identity and access management solutions, such as multi-factor authentication and role-based access controls, helps ensure that only authorized users have access to critical data. This multi-layered strategy allows for secure data handling without compromising the performance or accessibility of cloud services.
In addition, continuous monitoring and regular security audits play a crucial role in maintaining this balance by identifying potential vulnerabilities and enabling prompt remediation. Organizations can also leverage adaptive security measures that adjust protection levels based on user behavior and risk assessment. By adopting these best practices, businesses can create a secure, user-friendly cloud environment that meets both performance and compliance requirements, ultimately supporting a resilient digital infrastructure.
4. What strategies can be employed to mitigate insider threats in cloud security, and how can they be integrated with existing security protocols?
Answer: Mitigating insider threats in cloud security involves implementing robust identity and access management, continuous monitoring, and behavioral analytics to detect unusual activities from within the organization. Strategies such as enforcing the principle of least privilege, using multi-factor authentication, and maintaining detailed audit logs can limit the potential damage caused by insider threats. Integrating these measures with existing security protocols requires a holistic approach that aligns technical controls with organizational policies and employee training. Regular risk assessments and periodic reviews of user permissions further help ensure that only necessary access is granted, reducing the risk of malicious or negligent actions.
Furthermore, organizations can adopt automated systems that use AI to analyze user behavior in real time, identifying patterns that may indicate insider threats. These systems can trigger alerts and initiate incident response protocols, thereby minimizing potential damage. By combining these strategies with a strong security culture and clear communication, organizations can effectively reduce the risk posed by insider threats and safeguard their critical assets.
5. How might advancements in quantum computing impact current encryption methods used in cloud security?
Answer: Advancements in quantum computing have the potential to disrupt current encryption methods by significantly reducing the time required to break classical cryptographic algorithms. Quantum computers can process vast amounts of data using quantum algorithms, which may render traditional encryption techniques, such as RSA and ECC, vulnerable to attacks. As a result, there is a growing need for quantum-resistant encryption algorithms that can withstand the computational power of quantum machines. This shift will drive extensive research and development in post-quantum cryptography to ensure that cloud security remains robust in the face of emerging quantum threats.
To prepare for these changes, organizations must begin integrating quantum-resistant technologies into their cybersecurity frameworks and update existing encryption protocols accordingly. This proactive approach will not only protect sensitive data from future quantum attacks but also ensure compliance with evolving security standards. The transformation brought about by quantum computing is expected to redefine the landscape of digital security, prompting widespread adoption of new cryptographic solutions that secure cloud environments against next-generation threats.
6. What role does continuous monitoring play in maintaining cloud security, and how can it be optimized using AI?
Answer: Continuous monitoring plays a crucial role in maintaining cloud security by providing real-time visibility into system activities, network traffic, and potential security incidents. It enables organizations to detect anomalies and respond promptly to threats, thereby reducing the risk of successful cyberattacks. By integrating AI into continuous monitoring systems, organizations can enhance their ability to analyze large volumes of data, identify subtle patterns, and predict emerging threats. AI-powered monitoring tools can automate the detection process and trigger immediate responses, ensuring that the security infrastructure remains resilient and adaptive.
Optimizing continuous monitoring with AI also helps reduce false positives and improves the accuracy of threat detection. By learning from historical data and adapting to new attack vectors, AI systems can fine-tune alert thresholds and prioritize critical incidents, enabling more efficient resource allocation. This intelligent monitoring framework not only strengthens security but also supports proactive risk management, ensuring that cloud environments remain secure against dynamic threats.
7. How can organizations leverage threat intelligence to create a proactive cybersecurity posture in cloud environments?
Answer: Organizations can leverage threat intelligence by collecting and analyzing data from various sources such as global threat feeds, security communities, and internal logs to identify patterns and trends in cyberattacks. This information allows them to anticipate potential threats and implement preemptive measures to mitigate risks before an attack occurs. Integrating threat intelligence with automated security tools and continuous monitoring systems creates a proactive cybersecurity posture that dynamically adjusts defenses based on real-time insights. This approach not only enhances the speed and effectiveness of incident response but also enables better strategic planning for future security investments.
By regularly updating threat intelligence databases and correlating them with internal data, organizations can refine their security policies and enhance the precision of their protective measures. This proactive strategy reduces the likelihood of successful breaches and ensures that the cloud environment is continually fortified against both known and emerging threats. The overall effect is a resilient and agile security framework that supports long-term digital transformation.
8. What challenges might organizations face when integrating cloud security solutions with legacy systems, and what strategies can mitigate these challenges?
Answer: Integrating cloud security solutions with legacy systems can be challenging due to compatibility issues, outdated technologies, and differing security protocols. Legacy systems may lack the scalability, flexibility, and advanced features of modern cloud solutions, making it difficult to implement unified security measures across the organization. To mitigate these challenges, organizations can adopt a phased integration approach that gradually modernizes legacy systems while leveraging hybrid architectures that bridge the gap between old and new technologies. Utilizing middleware solutions and standardized interfaces can also facilitate smoother integration and data exchange between disparate systems.
Furthermore, providing targeted training and support for IT staff can help ensure that legacy systems are securely managed during the transition period. By continuously evaluating and updating security protocols across all systems, organizations can achieve a cohesive security posture that protects both legacy and cloud-based assets. This strategy not only minimizes disruption but also enables a gradual, sustainable path toward digital modernization.
9. How can regulatory compliance shape the future of cloud security, particularly in terms of data privacy and protection?
Answer: Regulatory compliance plays a significant role in shaping the future of cloud security by enforcing stringent standards for data privacy, protection, and reporting. As governments and international bodies introduce more comprehensive regulations, organizations will need to adopt advanced security measures to ensure that their cloud environments meet these legal requirements. Compliance influences the design of security frameworks, driving investments in encryption, access controls, and continuous monitoring solutions that safeguard sensitive data. These regulatory pressures ensure that cloud security practices are robust, transparent, and capable of protecting user privacy while minimizing the risk of data breaches.
In addition, adherence to regulatory standards fosters trust among customers and stakeholders, providing a competitive advantage in a market where data protection is paramount. Organizations that proactively integrate compliance into their security strategies can avoid costly penalties and enhance their overall risk management. This forward-looking approach is essential for building resilient, secure cloud infrastructures that support sustainable digital transformation.
10. How might the evolution of threat landscapes impact the development of cloud security technologies in the coming years?
Answer: The evolution of threat landscapes, characterized by increasingly sophisticated and targeted cyberattacks, will drive the development of advanced cloud security technologies that are more adaptive and proactive. As attackers employ new techniques and leverage emerging technologies, security solutions must evolve to counter these threats with real-time analytics, AI-driven detection, and automated response mechanisms. This evolution will likely lead to the integration of technologies such as machine learning, behavioral analytics, and quantum-resistant encryption, ensuring that cloud security remains robust and future-proof. The dynamic nature of cyber threats necessitates continuous innovation, pushing the boundaries of current security practices to develop next-generation defenses.
In response to these evolving threats, cloud security vendors and organizations will invest heavily in research and development to create systems that can predict and neutralize potential attacks before they occur. The increased collaboration between industry, academia, and government bodies will also facilitate the sharing of threat intelligence and best practices, accelerating the pace of innovation. Ultimately, the ongoing evolution of threat landscapes will shape a more resilient and adaptive cloud security ecosystem that is capable of withstanding even the most advanced cyber adversaries.
11. What potential benefits and drawbacks could arise from the widespread adoption of zero-trust models in cloud security?
Answer: The widespread adoption of zero-trust models in cloud security offers significant benefits by enforcing continuous verification for all users and devices, which minimizes the risk of unauthorized access and lateral movement within networks. This model enhances security by eliminating the notion of a trusted network perimeter and ensuring that every access request is thoroughly authenticated. However, implementing a zero-trust architecture can be complex and resource-intensive, requiring substantial changes to existing security policies and infrastructure. The transition may involve increased costs, extensive training, and potential disruptions during the integration process.
Despite these challenges, zero-trust models promise a higher level of security and are particularly effective in protecting against advanced persistent threats and insider attacks. Organizations that successfully implement zero-trust architectures can expect improved risk management, reduced exposure to cyberattacks, and enhanced compliance with regulatory standards. The long-term benefits of a robust zero-trust framework often outweigh the initial challenges, making it a compelling approach for future cloud security.
12. How can the integration of continuous monitoring and automated response systems transform cloud security operations?
Answer: The integration of continuous monitoring and automated response systems can transform cloud security operations by providing real-time insights and rapid mitigation of threats. Continuous monitoring ensures that any anomalies or suspicious activities are detected as soon as they occur, enabling security teams to take immediate action. Automated response systems can then execute predefined protocols to isolate and neutralize threats, significantly reducing response times and minimizing potential damage. This combination of real-time analytics and swift action not only enhances overall security posture but also improves the efficiency of security operations by reducing manual intervention and human error.
Furthermore, the synergy between continuous monitoring and automation enables organizations to maintain a proactive security environment that adapts dynamically to evolving threats. Over time, the data collected through monitoring can be used to refine response strategies and predict future incidents, leading to more robust risk management. This integrated approach is critical for achieving resilience in cloud security, ensuring that digital assets are protected in an ever-changing cyber landscape.
Cloud Security: Numerical Problems and Solutions
1. Calculating Annual Savings from Reduced Data Breach Costs
Solution:
Step 1: Assume the average cost per data breach is $1,000,000 and improved security reduces breach frequency by 2 incidents per year.
Step 2: Annual savings = 2 × $1,000,000 = $2,000,000.
Step 3: Verify by noting that without improvements, costs would be higher by $2,000,000 per year.
2. Estimating ROI for an AI-Driven Cloud Security Solution
Solution:
Step 1: Suppose the solution costs $400,000 to implement and saves $120,000 annually in breach mitigation and operational costs.
Step 2: Payback period = $400,000 ÷ $120,000 ≈ 3.33 years.
Step 3: Over 5 years, total savings = $120,000 × 5 = $600,000; ROI = (($600,000 – $400,000) ÷ $400,000) × 100 = 50%.
3. Calculating the Reduction in Incident Response Time
Solution:
Step 1: Assume the average incident response time is 50 minutes, reduced to 30 minutes after automation.
Step 2: Time saved per incident = 50 – 30 = 20 minutes.
Step 3: Percentage improvement = (20 ÷ 50) × 100 = 40%.
4. Estimating the Cost Savings from Improved Security Awareness Training
Solution:
Step 1: Suppose a training program costs $25,000 per year and reduces security incidents by 3, with each incident costing $150,000.
Step 2: Annual cost of incidents avoided = 3 × $150,000 = $450,000.
Step 3: Net savings = $450,000 – $25,000 = $425,000 annually.
5. Calculating the Average Cost Reduction per User for Enhanced Access Control
Solution:
Step 1: Assume enhanced access control reduces breach costs by $80 per user per year for 10,000 users.
Step 2: Total annual savings = 10,000 × $80 = $800,000.
Step 3: Average cost reduction per user = $80.
6. Determining the Reduction in False Positive Rates
Solution:
Step 1: Assume traditional systems have a 30% false positive rate and AI reduces it to 10%.
Step 2: Reduction = 30% – 10% = 20 percentage points.
Step 3: Relative reduction = (20 ÷ 30) × 100 ≈ 66.67%.
7. Calculating the Savings from Automated Monitoring
Solution:
Step 1: Assume manual monitoring costs $60,000 per year and automation reduces costs by 70%.
Step 2: Savings = $60,000 × 0.70 = $42,000.
Step 3: New cost = $60,000 – $42,000 = $18,000 per year.
8. Estimating the Annual Downtime Cost Reduction
Solution:
Step 1: Assume downtime costs $200,000 per hour and improvements reduce downtime by 15 hours per year.
Step 2: Annual savings = 15 × $200,000 = $3,000,000.
Step 3: Confirm that the reduction is significant compared to the baseline.
9. Calculating the Cost Efficiency of a Multi-Factor Authentication (MFA) System
Solution:
Step 1: Assume MFA implementation costs $50,000 per year and reduces breach costs by $250,000 annually.
Step 2: Net savings = $250,000 – $50,000 = $200,000.
Step 3: ROI = ($200,000 ÷ $50,000) × 100 = 400%.
10. Determining the Average Annual Cost of a Data Breach
Solution:
Step 1: Suppose total annual breach costs amount to $3,000,000 for 6 breaches.
Step 2: Average cost per breach = $3,000,000 ÷ 6 = $500,000.
Step 3: Verify by multiplying: 6 × $500,000 = $3,000,000.
11. Calculating the Percentage Decrease in Security Incident Frequency
Solution:
Step 1: Assume there were 40 security incidents last year and new measures reduce incidents by 25%.
Step 2: Reduction in number of incidents = 40 × 0.25 = 10 incidents.
Step 3: New incident count = 40 – 10 = 30; percentage decrease = (10 ÷ 40) × 100 = 25%.
12. Break-even Analysis for a Cloud Security Upgrade
Solution:
Step 1: Assume a security upgrade costs $500,000 and yields monthly savings of $45,000 in operational efficiencies and breach mitigation.
Step 2: Payback period = $500,000 ÷ $45,000 ≈ 11.11 months, rounded to 12 months.
Step 3: Over 5 years (60 months), total savings = $45,000 × 60 = $2,700,000, confirming a strong return on investment.
