Network Architecture and Protocols Education is an education in invisible agreements. When devices communicate, they do so through layered rules—naming, addressing, routing, reliability, congestion control, security handshakes—most of which the user never sees. The diagram clarifies how those rules become teachable skill. Inputs bring purpose and relevance: learners arrive with goals (connect systems, secure traffic, improve performance), while industry requirements bring constraints (scale, uptime, compliance, cost, interoperability). Controls keep the subject disciplined, ensuring students don’t just memorise acronyms but learn to justify design choices, validate behaviour, and document decisions with care. Mechanisms then supply the workshop: tools to simulate and measure, labs to build and break safely, and resources that guide students from simple topologies to robust architectures. The outputs—capable practitioners and real projects—signal the end goal: not merely knowing what a protocol is, but knowing how and why it behaves, and how to design networks that remain trustworthy under stress.
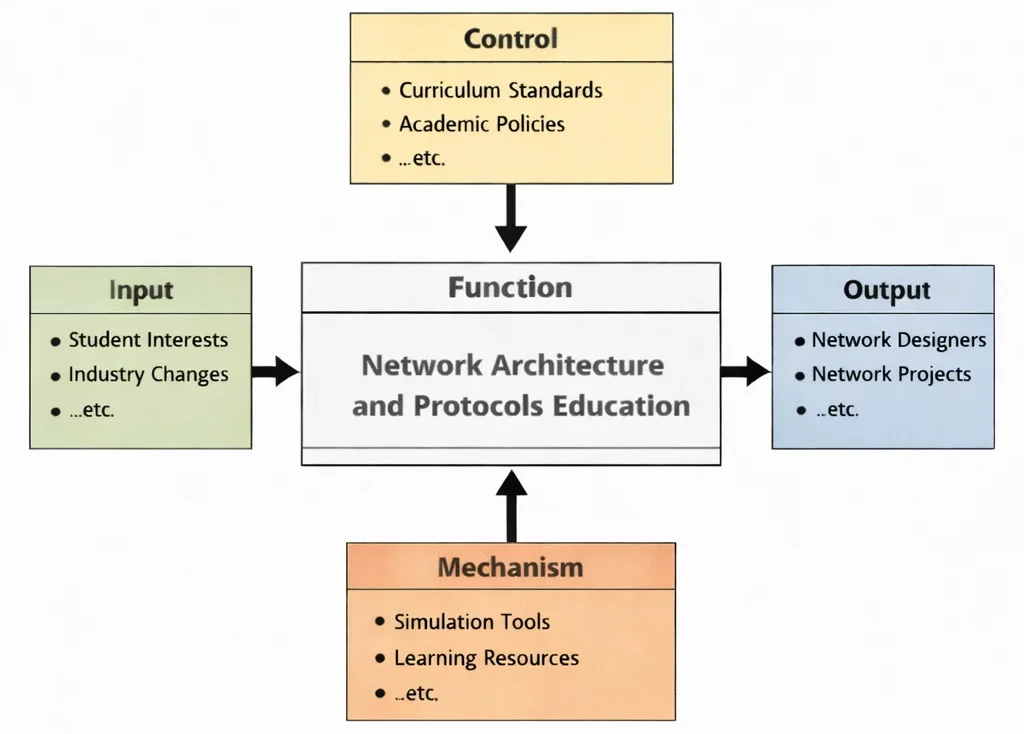
This IDEF0 diagram presents “Network Architecture and Protocols Education” as a structured transformation. From the left, inputs such as student needs and industry requirements enter the learning function. From above, controls—curriculum standards and academic policies—shape the scope, sequencing, rigor, and assessment of what is taught. On the right, outputs emerge as skilled practitioners and completed network projects that demonstrate applied understanding. From below, mechanisms such as networking tools, lab environments, and learning resources provide the practical means for building, testing, tracing, troubleshooting, and refining protocol-driven systems.
Understanding network architecture and protocols is fundamental to the design, operation, and evolution of modern digital infrastructure. At its core, network architecture defines the structure and organization of how data is communicated across systems, while protocols specify the rules and standards that govern these interactions. These concepts underpin nearly every aspect of STEM fields, particularly within Information Technology, where they support everything from small-scale applications to large-scale cloud and enterprise systems.
The role of network management and administration is vital in maintaining efficient operations, ensuring network uptime, and resolving performance bottlenecks. Meanwhile, concerns around security are addressed through layered network security protocols that detect, prevent, and respond to cyber threats. Protocols such as TCP/IP, HTTP, and DNS form the backbone of the internet, but these are increasingly complemented by newer models tailored for dynamic environments.
In global communications, telecommunication systems and standards ensure interoperability across devices and networks. The rise of wireless and mobile communications has transformed user expectations for seamless connectivity, placing new demands on protocol efficiency and reliability in 4G, 5G, and beyond.
These architectural and protocol foundations intersect significantly with software development. Developers must understand protocol behavior when designing distributed systems, APIs, and cloud-native applications. Similarly, the growth of the Internet of Things (IoT) is fueled by innovations in embedded systems and IoT development, which rely on lightweight communication protocols for sensor data transmission and device coordination.
Effective digital systems also prioritize usability, as addressed in HCI and UX design. These interfaces, while seemingly unrelated to low-level protocols, depend on the speed and accuracy of underlying network services. For developers targeting smartphones, an understanding of mobile application development requires proficiency with mobile protocols and backend integrations.
Languages like Python, Java, and C++—explored in programming languages and paradigms—are employed in developing software that interacts with networking layers. This process is guided by principles discussed in software architecture and design and refined through software engineering practices. These efforts continue through stages of maintenance and evolution, where protocol updates and architectural changes must be managed carefully.
System robustness is validated through software testing and QA, which often involve simulating network loads and examining how protocols behave under stress. These testing insights are especially relevant for developers working in web development and design, where real-time interactivity depends on efficient client-server communication.
In modern web applications, back-end development handles the server-side logic and databases, often interacting directly with network protocols to deliver content and services. Content Management Systems (CMS) streamline web deployment but still rely on HTTP, HTTPS, and DNS protocols. Platforms focusing on e-commerce development require secure protocols such as SSL/TLS to ensure safe transactions.
Meanwhile, front-end development ensures the user-facing interface communicates efficiently with the back-end via AJAX, REST, and WebSocket protocols. Developers pursuing full-stack development must grasp the full spectrum of protocol use across the application stack. This includes optimizing web visibility through SEO and monitoring user behavior using web analytics tools.
Finally, good web design ensures that networked applications are not only functional but also responsive and accessible—qualities that rely on low-latency, protocol-efficient delivery. For learners and developers alike, mastering network architecture and protocols provides the technical foundation for building secure, scalable, and user-centric digital solutions.

This image presents computer networking as a luminous “city grid” of interconnected blocks, where each glowing tower suggests a major node such as a server cluster, router, or switch. Bright pathways run between components like multilane highways, symbolizing data packets traveling through a network. Floating labels such as TCP/IP and HTTP point to the protocol layers that make communication possible—from addressing and routing, to transport reliability, to application-level messaging. The stacked, modular look of the components evokes layered architecture: physical links and devices at the bottom, logical routing and transport in the middle, and higher-level services on top. Overall, the illustration captures the idea that network performance, security, and scalability come from both good architecture (how systems are arranged) and well-defined protocols (the shared rules that keep data flowing correctly).
- Networking & Telecommunication topics:
- Overview
- Telecommunication Systems & Standards
- Data Transmission & Communication Technologies
- Network Architecture & Protocols
- Network Management & Administration
- Network Security
- Cloud Networking
- Wireless & Mobile Communications
- Internet & Web Technologies
- Network & Transmission – Emerging Technologies
Table of Contents
Key Topics in Network Architecture and Protocols
OSI and TCP/IP Models:
- These layered frameworks simplify the complexities of networking by dividing communication tasks into discrete layers, each responsible for specific functions.
- OSI Model: Comprises seven layers, from the physical to the application layer, offering a universal reference for understanding network processes.
- TCP/IP Model: Focuses on four layers and forms the foundation of internet communication.
Routing Protocols:
- Enable data packets to find the most efficient paths across networks.
- Examples include:
- OSPF (Open Shortest Path First): Determines optimal paths based on link-state information.
- BGP (Border Gateway Protocol): Manages routing between large networks, such as ISPs.
- RIP (Routing Information Protocol): A simpler protocol suitable for smaller networks.
Switching Techniques:
- Facilitate the transfer of data within networks.
- Circuit Switching: Establishes a dedicated communication path (e.g., telephone networks).
- Packet Switching: Breaks data into packets sent independently across the network (e.g., the internet).
- Virtual Circuits: Combine features of circuit and packet switching for reliable communication.
Wireless Protocols:
- Govern wireless communication between devices.
- Examples include:
- Wi-Fi (802.11): Enables high-speed wireless internet connectivity.
- Bluetooth: Facilitates short-range communication between devices.
- 5G: Supports ultra-fast speeds and low latency for modern mobile networks.
Applications of Network Architecture and Protocols
Enterprise Networks:
- Designing scalable and secure infrastructures for businesses, supporting collaboration and productivity.
- Example: Implementing VLANs and VPNs for secure communication.
Service Providers:
- Building robust backbones to support high traffic demands, such as in ISPs and cloud services.
- Example: Deploying BGP to manage internet traffic across global networks.
Emerging Technologies:
- Supporting IoT, 5G, and cloud applications by optimizing network performance and interoperability.
Sub-Areas in the Study of Network Architecture and Protocols
Network Topologies:
- Study of physical and logical arrangements of network components.
- Types: Star, ring, bus, mesh, and hybrid topologies.
- Applications: Determining optimal setups for specific environments, such as data centers or smart grids.
Network Virtualization:
- Abstraction of physical network resources into virtual networks.
- Tools: VMware NSX, Cisco ACI, and SD-WAN solutions.
- Applications: Enhancing flexibility, reducing costs, and enabling dynamic network reconfiguration.
Protocol Design and Analysis:
- Developing and evaluating new communication protocols.
- Tools: Wireshark for analyzing existing protocols and ns-3 for simulation.
- Applications: Ensuring efficient and secure communication in cutting-edge technologies.
Network Security Protocols:
- Specialized protocols designed to secure data transmission.
- Examples: SSL/TLS for secure web communication, IPSec for VPNs.
- Applications: Protecting sensitive information in financial transactions and healthcare systems.
Quality of Service (QoS):
- Mechanisms to prioritize certain types of network traffic.
- Techniques: Traffic shaping, bandwidth management, and resource reservation.
- Applications: Ensuring smooth video streaming, VoIP calls, and real-time gaming.
Wireless and Mobile Networks:
- Advanced study of wireless communication technologies and protocols.
- Focus Areas: LTE, 5G, and satellite networks.
- Applications: Supporting mobile connectivity, remote access, and IoT ecosystems.
Why Study Network Architecture and Protocols
Designing the Blueprint of Connectivity
Network architecture defines how systems are structured and connected, while protocols determine how data flows. Mastering this equips students to build efficient and scalable networks.
Foundational to Systems Engineering
Students learn about OSI and TCP/IP models, routing algorithms, IP addressing, and protocol design—vital for configuring complex networks.
Gateway to Advanced Networking Roles
This knowledge is essential for network architects, protocol engineers, and infrastructure planners in large organizations.
Network Architecture and Protocols Summary
By delving into network architecture and protocols, students and professionals gain a comprehensive understanding of the frameworks that underpin global communication systems. This knowledge is instrumental in building and managing networks that are secure, scalable, and optimized for modern technological demands.
Network Architecture and Protocols: Review Questions and Answers:
1. What is network architecture and why is it critical in modern telecommunication systems?
Answer: Network architecture refers to the design and structure of a network, including its hardware, software, connectivity, protocols, and data flow. It is critical because it determines how efficiently and securely data is transmitted across various devices and locations. A well-designed network architecture ensures high performance, reliability, and scalability, which are essential for supporting today’s data-intensive applications. Moreover, it forms the backbone of global communications by enabling seamless interconnectivity and robust security measures.
2. How do communication protocols facilitate effective data transmission in networks?
Answer: Communication protocols are standardized rules that govern the exchange of data between network devices, ensuring interoperability and reliability. They manage how data packets are formatted, transmitted, and received, which minimizes errors and maintains the integrity of the information. Protocols such as TCP/IP and HTTP are integral to internet communications, enabling devices from different manufacturers to communicate effectively. Their role is essential for delivering consistent, secure, and efficient data transmission across diverse network environments.
3. What are the key layers of the OSI model and their functions in network communication?
Answer: The OSI model consists of seven layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer has specific functions that facilitate the smooth transfer of data, from the physical transmission of bits over a medium to the presentation and interpretation of data for the end user. The Physical and Data Link layers handle hardware-level data transmission, while the Network and Transport layers manage routing and error recovery. The upper layers (Session, Presentation, and Application) focus on user interaction and ensuring that data is formatted and delivered correctly to applications.
4. How do routing protocols contribute to network efficiency and reliability?
Answer: Routing protocols are algorithms used to determine the optimal path for data packets to travel across networks. They contribute to efficiency by dynamically adjusting routes based on current network conditions and traffic loads. This adaptability ensures that data is transmitted via the most efficient path, reducing latency and preventing congestion. Moreover, routing protocols enhance reliability by providing mechanisms for rerouting in case of network failures, ensuring continuous connectivity and robust communication.
5. What role does network security play in the design of network architectures and protocols?
Answer: Network security is a fundamental aspect of network design that focuses on protecting data integrity, confidentiality, and availability across the network. It involves implementing measures such as encryption, firewalls, intrusion detection systems, and secure authentication protocols to guard against unauthorized access and cyber threats. Effective security ensures that sensitive information is transmitted safely and that the network remains resilient against attacks. This, in turn, builds trust among users and stakeholders and supports the reliable operation of critical communication systems.
6. How do cloud networking solutions integrate with traditional network architectures?
Answer: Cloud networking solutions integrate with traditional network architectures by leveraging virtualization and centralized management to extend network capabilities. They allow organizations to dynamically scale resources, improve redundancy, and facilitate remote access through cloud-based infrastructures. This integration enables seamless communication between on-premises and cloud environments, ensuring that data is accessible and securely managed regardless of its location. By combining the strengths of traditional and cloud networks, businesses can achieve greater flexibility, scalability, and cost efficiency in their communications.
7. What is the importance of network protocols such as TCP/IP in global communications?
Answer: TCP/IP is the foundational protocol suite that underpins global communications, enabling data exchange over the Internet. It is important because it standardizes the way data is packetized, transmitted, and received, ensuring interoperability among devices from different manufacturers and across diverse networks. TCP/IP manages error checking and data integrity, which are essential for reliable and efficient communication. Its universal adoption has allowed the Internet to evolve into a robust and scalable global network, facilitating the seamless transfer of information worldwide.
8. How do emerging technologies like SDN and NFV impact network architecture and data transmission?
Answer: Emerging technologies such as Software-Defined Networking (SDN) and Network Functions Virtualization (NFV) have a transformative impact on network architecture by decoupling network functions from physical hardware. SDN centralizes network control, allowing for dynamic and flexible management of network resources, while NFV virtualizes network services to run on standard servers. These innovations enable more efficient routing, rapid provisioning, and improved scalability, which are critical for handling increasing data volumes and complex network demands. They ultimately result in faster, more reliable, and more cost-effective data transmission solutions.
9. What challenges do traditional networking technologies face that emerging transmission technologies aim to solve?
Answer: Traditional networking technologies often struggle with limitations such as lower bandwidth, higher latency, and less flexibility in managing dynamic data flows. These challenges can hinder performance, especially in an era of massive data consumption and real-time applications. Emerging transmission technologies aim to solve these issues by leveraging advanced fiber optics, enhanced wireless standards, and sophisticated routing protocols. They offer higher speeds, reduced latency, and improved reliability, ensuring that modern networks can support the demands of contemporary digital communication and global connectivity.
10. How do web technologies and internet protocols contribute to the seamless integration of various network systems?
Answer: Web technologies and internet protocols provide a standardized framework for data exchange, ensuring that disparate network systems can communicate effectively. Protocols such as HTTP, FTP, and DNS enable the smooth transfer of data between servers and clients, regardless of the underlying hardware or software differences. These standards promote interoperability and allow for the seamless integration of various network components, from local networks to global internet systems. By facilitating uniform data transmission and processing, these technologies play a crucial role in maintaining a cohesive and efficient global communication infrastructure.
Network Architecture and Protocols: Thought-Provoking Questions and Answers
1. How will the evolution of 6G technology impact the future of network architecture and data transmission?
Answer: The evolution of 6G technology is expected to bring unprecedented speeds, ultra-low latency, and massive connectivity, fundamentally transforming network architecture and data transmission. 6G could enable seamless integration of advanced applications such as real-time augmented reality, holographic communications, and enhanced IoT capabilities, pushing the boundaries of current network performance. The technology promises to reduce latency to nearly zero, facilitating near-instantaneous communication across global networks.
In addition, the adoption of 6G will require a complete rethinking of network infrastructure, emphasizing scalability, flexibility, and robust security measures to manage the enormous data flows. This evolution will not only drive innovations in consumer technology but also reshape enterprise communications, smart cities, and critical infrastructure, ultimately fostering a more connected and intelligent digital ecosystem.
2. What ethical implications arise from the increased data transmission speeds enabled by emerging technologies, and how should they be addressed?
Answer: The increased data transmission speeds enabled by emerging technologies raise ethical implications related to data privacy, surveillance, and equitable access. Faster transmission allows for the rapid collection and processing of vast amounts of personal and sensitive data, which can lead to concerns about unauthorized monitoring and breaches of privacy. Additionally, if only certain regions or organizations have access to these high-speed networks, it may widen the digital divide and create disparities in access to information and services.
To address these ethical concerns, it is essential to implement robust data protection frameworks, enforce strict privacy regulations, and ensure transparency in data collection practices. Organizations must work closely with regulators and stakeholders to develop guidelines that balance the benefits of high-speed data transmission with the need to protect individual rights. Continuous monitoring, ethical audits, and public engagement are key strategies in fostering a responsible digital environment.
3. How can artificial intelligence be leveraged to optimize network protocols and improve data transmission efficiency?
Answer: Artificial intelligence can be leveraged to optimize network protocols by analyzing real-time network performance data and dynamically adjusting routing and transmission parameters to enhance efficiency. AI algorithms can detect anomalies, predict traffic congestion, and optimize bandwidth allocation, ensuring that data is transmitted along the most efficient paths. This proactive management not only reduces latency and packet loss but also improves overall network reliability and user experience.
Moreover, AI-driven network management can automate routine tasks such as error correction, load balancing, and resource allocation, freeing up human resources for more strategic initiatives. The continuous learning capability of AI ensures that the network adapts to evolving conditions, making it resilient to disruptions and scalable to meet future demands. As these technologies mature, they will play a pivotal role in shaping the next generation of smart, efficient communication networks.
4. What impact will quantum communication have on the security of data transmission in global networks?
Answer: Quantum communication promises to revolutionize data security by leveraging the principles of quantum mechanics to create virtually unbreakable encryption methods. Through techniques such as quantum key distribution (QKD), it ensures that any attempt to intercept data alters the quantum state, alerting parties to potential breaches. This breakthrough has the potential to dramatically enhance the security of global networks, making data transmission resistant to even the most sophisticated cyber attacks.
The implementation of quantum communication could also lead to the development of new standards and protocols for secure data exchange, fundamentally changing the way sensitive information is protected. However, integrating quantum technologies with existing network infrastructures poses significant technical challenges, including compatibility and cost considerations. Addressing these issues will require ongoing research, collaboration, and substantial investment in new hardware and software solutions.
5. How might the convergence of cloud networking and edge computing improve data transmission in remote and underserved areas?
Answer: The convergence of cloud networking and edge computing can significantly improve data transmission in remote and underserved areas by bringing processing capabilities closer to the data source. Edge computing reduces latency by processing data locally, while cloud networking provides scalable storage and centralized management for complex tasks. This hybrid approach enables faster, more reliable communication even in areas with limited infrastructure, bridging the connectivity gap and enhancing service delivery.
By leveraging these technologies, remote communities can access high-speed internet, advanced digital services, and real-time data analytics, driving economic and social development. Additionally, this integration facilitates efficient resource utilization and robust network management, ensuring that even low-bandwidth areas receive optimized performance and improved overall connectivity.
6. What are the potential challenges in integrating traditional networking systems with emerging communication technologies, and how can they be overcome?
Answer: Integrating traditional networking systems with emerging communication technologies presents challenges such as compatibility issues, increased complexity, and potential security vulnerabilities. Traditional systems may not be designed to support the high-speed, high-capacity demands of modern technologies like 5G and cloud networking, leading to interoperability problems and inefficiencies. Additionally, merging legacy infrastructure with cutting-edge solutions can introduce security risks if not managed properly.
To overcome these challenges, organizations can adopt phased integration strategies that gradually upgrade legacy systems while implementing robust middleware and APIs to ensure seamless communication. Investing in training and adopting flexible, modular architectures will also help mitigate these issues. By ensuring that new technologies are compatible with existing systems, businesses can achieve a smooth transition and harness the benefits of emerging communication solutions.
7. How do modern web technologies contribute to the evolution of internet communication infrastructures?
Answer: Modern web technologies, including advanced protocols, dynamic content delivery networks, and responsive design, contribute to the evolution of internet communication infrastructures by enabling faster, more reliable, and secure data exchange. These technologies improve the efficiency of web services and enhance the user experience by optimizing content delivery and reducing latency. They also support the growing demand for interactive and real-time applications, facilitating seamless global connectivity.
As web technologies continue to evolve, they drive innovation in network architecture, allowing for more scalable and flexible infrastructures that can adapt to emerging trends. This evolution is crucial for supporting the increasing complexity of digital communication and ensuring that the Internet remains a robust platform for information exchange.
8. What is the significance of protocol standardization in global network communication, and how does it impact interoperability?
Answer: Protocol standardization is essential in global network communication because it ensures that different devices and systems can communicate effectively regardless of their underlying hardware or software. Standardized protocols like TCP/IP, HTTP, and DNS create a common language that facilitates seamless data exchange and interoperability across diverse networks. This uniformity allows for the integration of new technologies and supports the scalability of global communication systems.
The impact of protocol standardization is far-reaching, as it reduces complexity and promotes a consistent, reliable framework for data transmission. This, in turn, leads to enhanced security, improved performance, and reduced development costs, ultimately driving the efficiency and growth of the global digital ecosystem.
9. How might advancements in software-defined networking (SDN) and network virtualization influence the design of future internet architectures?
Answer: Advancements in software-defined networking (SDN) and network virtualization are set to revolutionize internet architectures by enabling more dynamic and flexible network management. SDN allows centralized control of the network, enabling real-time adjustments and efficient resource allocation, while virtualization decouples network functions from physical hardware. Together, they facilitate rapid deployment, enhanced scalability, and improved security across network infrastructures.
These technologies can transform the design of internet architectures by providing a more adaptive and resilient framework that responds to fluctuating demands and emerging challenges. The shift towards virtualized networks will also drive cost efficiencies and operational agility, paving the way for next-generation communication systems that are both robust and versatile.
10. How can the integration of IoT devices enhance data transmission in modern networks, and what challenges does this integration pose?
Answer: The integration of IoT devices enhances data transmission in modern networks by generating large volumes of data from a diverse array of sources, enabling more comprehensive monitoring and real-time analytics. This connectivity allows for improved automation, smarter resource management, and innovative applications such as smart cities and industrial automation. However, the integration of IoT also poses challenges such as increased network congestion, security vulnerabilities, and the need for effective data management strategies to handle the vast data flow.
Addressing these challenges requires robust network architectures that can scale efficiently, enhanced security measures to protect sensitive information, and advanced analytics tools to process and interpret the data. By overcoming these obstacles, organizations can fully leverage the benefits of IoT integration to drive innovation and improve global connectivity.
11. What role do content delivery networks (CDNs) play in optimizing data transmission for web technologies?
Answer: Content delivery networks (CDNs) play a critical role in optimizing data transmission by distributing content across multiple servers located closer to end users. This geographical distribution reduces latency, speeds up load times, and improves the overall performance of web applications. CDNs ensure that data is delivered efficiently even during high traffic periods by balancing the load across various nodes, thereby preventing bottlenecks.
The use of CDNs enhances user experience and supports the scalability of internet services by providing robust, high-speed connectivity. This optimization is especially important for global audiences, ensuring that content is accessible and delivered promptly regardless of the user’s location.
12. How might the continuous evolution of internet protocols shape the future of global digital communication?
Answer: The continuous evolution of internet protocols will shape the future of global digital communication by enhancing the efficiency, security, and reliability of data transmission. New protocols are expected to support higher speeds, lower latency, and improved error correction, enabling more robust interactions between devices and networks. These advancements will drive innovation in various sectors, including e-commerce, telemedicine, and virtual collaboration, by ensuring that digital communications are fast, secure, and reliable.
As protocols evolve, they will also facilitate the integration of emerging technologies such as IoT, 5G, and edge computing, creating a more interconnected and dynamic digital ecosystem. This evolution is critical for meeting the growing demands of the digital age, fostering innovation, and ensuring that global communication infrastructures remain resilient and adaptable to future challenges.
Network Architecture and Protocols: Numerical Problems and Solutions:
1. A cloud network transmits data at 120 Mbps. Calculate the total data transmitted in one hour in gigabytes, then in 24 hours, and finally the average data transmitted per minute.
Solution:
• Step 1: Data per second = 120 Mbps = 120 × 10^6 bits.
• Step 2: Data per hour = 120 × 10^6 × 3600 = 432 × 10^9 bits; convert to GB: 432 × 10^9 ÷ (8 × 10^9) = 54 GB.
• Step 3: Data per day = 54 GB × 24 = 1,296 GB; average per minute = 1,296 ÷ (24×60) = 1,296 ÷ 1440 = 0.9 GB per minute.
2. A router processes 2,500 packets per second. Calculate the number of packets processed per minute, per hour, and per day (24 hours).
Solution:
• Step 1: Packets per minute = 2,500 × 60 = 150,000 packets.
• Step 2: Packets per hour = 150,000 × 60 = 9,000,000 packets.
• Step 3: Packets per day = 9,000,000 × 24 = 216,000,000 packets.
3. A telecommunication link operates at 80 Mbps. For 2 hours, calculate the total data transmitted in gigabytes, and determine the average data rate per minute in MB.
Solution:
• Step 1: Data per second = 80 Mbps = 80 × 10^6 bits.
• Step 2: Total data in 2 hours = 80 × 10^6 × 2 × 3600 = 576 × 10^9 bits; convert to GB: 576 × 10^9 ÷ (8 × 10^9) = 72 GB.
• Step 3: Average per minute = 72 GB ÷ (2×60) = 72 ÷ 120 = 0.6 GB per minute, which equals 600 MB per minute.
4. A fiber optic cable exhibits a latency of 3 ms per 100 km. Calculate the latency for 700 km, then for 1,200 km, and find the difference between these two latencies.
Solution:
• Step 1: Latency per km = 3 ms ÷ 100 = 0.03 ms/km.
• Step 2: Latency for 700 km = 700 × 0.03 = 21 ms; for 1,200 km = 1,200 × 0.03 = 36 ms.
• Step 3: Difference = 36 ms – 21 ms = 15 ms.
5. A network experiences a packet loss rate of 0.15%. If 5,000,000 packets are transmitted, calculate the number of lost packets, then the number of successfully transmitted packets, and the overall success percentage.
Solution:
• Step 1: Lost packets = 5,000,000 × 0.0015 = 7,500 packets.
• Step 2: Successful packets = 5,000,000 – 7,500 = 4,992,500 packets.
• Step 3: Success percentage = (4,992,500 ÷ 5,000,000) × 100 ≈ 99.85%.
6. A wireless access point transmits at 300 Mbps. Calculate the total data transmitted in 15 minutes in megabytes.
Solution:
• Step 1: Data per second = 300 Mbps = 300 × 10^6 bits.
• Step 2: Total data in 15 minutes = 300 × 10^6 × 900 = 270 × 10^9 bits.
• Step 3: Convert to MB: 270 × 10^9 ÷ (8 × 10^6) = 33,750 MB.
7. A network monitoring system logs 500,000 events per hour. Calculate the total events logged in one day, then in one week, and finally the average events per minute over the week.
Solution:
• Step 1: Daily events = 500,000 × 24 = 12,000,000 events.
• Step 2: Weekly events = 12,000,000 × 7 = 84,000,000 events.
• Step 3: Average per minute = 84,000,000 ÷ (7×24×60) = 84,000,000 ÷ 10,080 ≈ 8,333.33 events per minute.
8. A network upgrade increases bandwidth from 90 Mbps to 135 Mbps. Calculate the percentage increase, the additional data transmitted per second in Mbps, and then the additional data transmitted in one hour in GB.
Solution:
• Step 1: Percentage increase = ((135 – 90) ÷ 90) × 100 = 50%.
• Step 2: Additional bandwidth = 135 – 90 = 45 Mbps = 45 × 10^6 bits per second.
• Step 3: Additional data per hour = 45 × 10^6 × 3600 = 162 × 10^9 bits; in GB = 162 × 10^9 ÷ (8 × 10^9) = 20.25 GB.
9. A network’s average latency is 18 ms. If an optimization reduces latency by 20%, calculate the new latency, the absolute reduction, and the percentage decrease.
Solution:
• Step 1: New latency = 18 × 0.80 = 14.4 ms.
• Step 2: Absolute reduction = 18 – 14.4 = 3.6 ms.
• Step 3: Percentage decrease = (3.6 ÷ 18) × 100 = 20%.
10. A router transmits 3,000 packets per second. Calculate the number of packets transmitted per minute, per hour, and per day (24 hours).
Solution:
• Step 1: Packets per minute = 3,000 × 60 = 180,000 packets.
• Step 2: Packets per hour = 180,000 × 60 = 10,800,000 packets.
• Step 3: Packets per day = 10,800,000 × 24 = 259,200,000 packets.
11. A telecom provider serves 20,000 subscribers, each using 2.5 GB of data per month. Calculate the total monthly data usage, then the annual usage, and finally the average data usage per subscriber per year.
Solution:
• Step 1: Monthly usage = 20,000 × 2.5 = 50,000 GB.
• Step 2: Annual usage = 50,000 × 12 = 600,000 GB.
• Step 3: Average per subscriber per year = 600,000 ÷ 20,000 = 30 GB per year.
12. A network monitoring system processes 800,000 logs per day. If 0.1% of these logs are flagged as critical, calculate the number of critical logs per day, then per month (30 days), and finally the percentage of critical logs relative to the total logs.
Solution:
• Step 1: Critical logs per day = 800,000 × 0.001 = 800 logs.
• Step 2: Critical logs per month = 800 × 30 = 24,000 logs.
• Step 3: Percentage of critical logs = (800 ÷ 800,000) × 100 = 0.1%.
