Networking and Telecommunication Education is the study of the world’s quiet infrastructure—the invisible agreements, signals, and protocols that allow messages to travel farther than any voice can carry. The diagram tells a simple story: learners and industry provide the raw material, standards provide the discipline, tools provide the workshop, and the outcome is competence that can survive contact with reality.
On the input side, students arrive with different starting points: some are curious about Wi-Fi and routers, others want cybersecurity, cloud networking, or mobile systems. At the same time, industry trends keep shifting—faster networks, new wireless standards, software-defined everything, and an ever-louder demand for reliability. These inputs ensure the curriculum does not drift into outdated trivia.
Controls give the learning process its backbone. Curriculum standards and academic policies define what “good” looks like: foundational concepts (addressing, routing, switching, radio basics), safe and ethical practice, and assessments that reward not just memorisation but correct reasoning. In networking, confidence without method can be expensive—so the controls encourage habits: verify assumptions, test systematically, document clearly, and design for resilience.
Mechanisms are where understanding becomes usable. With lab tools, simulators, configurations, and well-designed training resources, students learn to build networks, break them on purpose, and repair them intelligently. They practice reading logs, tracing packets, measuring performance, and diagnosing failures that hide behind “it works sometimes.” When the function is working well, the outputs speak for themselves: technicians who can keep systems running, and projects that demonstrate practical design, real troubleshooting skill, and an appreciation for how communication networks underpin modern life.
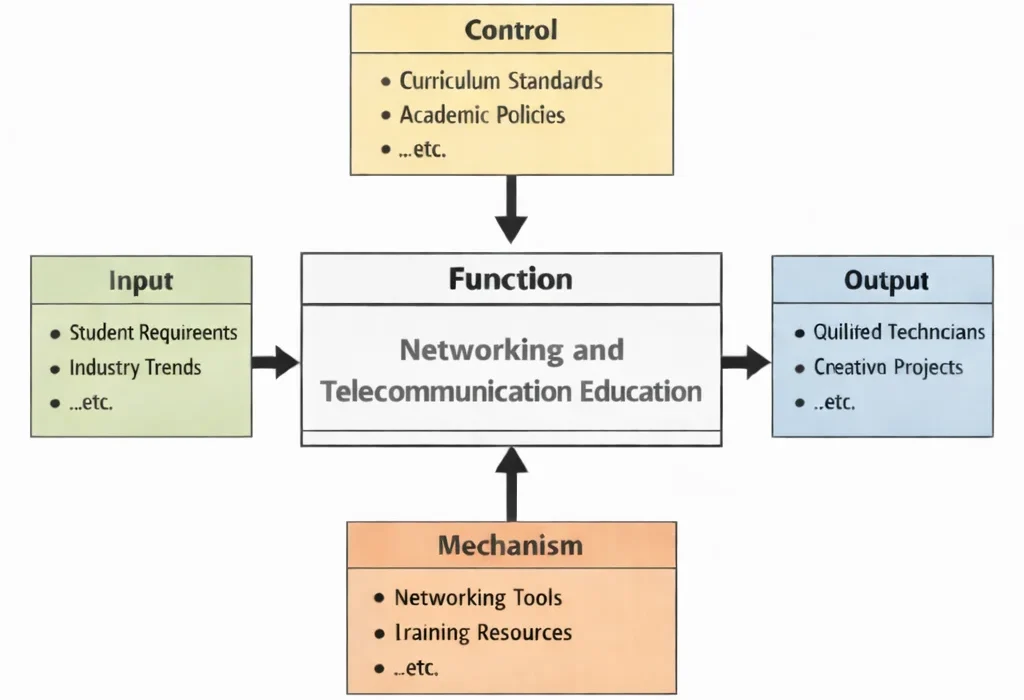
This IDEF0 diagram models “Networking and Telecommunication Education” as a structured transformation. Inputs such as student requirements and industry trends enter from the left, while controls—curriculum standards and academic policies—guide content, sequencing, assessment, and professional expectations from above. The central function produces outputs on the right, including qualified technicians and completed projects. The process is enabled by mechanisms from below, such as networking tools and training resources, which support hands-on configuration, testing, troubleshooting, documentation, and iterative skill-building.
Computer networking is how devices agree to talk: addressing, routing, name resolution, and rules that keep traffic orderly. This page gives you a practical path from zero to confident: what an IP packet looks like, how switches and routers differ, why DNS matters, and how the web’s request–response flow works. You’ll trace a packet across a small network, read a routing table, and see how latency, bandwidth, and loss shape user experience.
We keep the maths light and the practice real. Start by identifying your own IP and default gateway, then use common tools to test reachability and name resolution. Move on to subnets and CIDR, NAT vs public addressing, and the basics of secure transport. By the end, you’ll be able to sketch a small office/home network, explain each box’s job, and diagnose the most common failures with intent.
Why this matters. Digital networking and telecommunication underpin the global infrastructure that enables modern communication, data exchange, and online services. As society becomes increasingly connected, understanding the protocols, architecture, and security of these systems is critical.
Security foundations. In practice, fields such as network security and endpoint security keep networks fast and reliable while guarding against unauthorized access and data breaches. At the heart of secure networking lies cryptography, paired with identity and access management to authenticate users and protect resources. Organizations rely on formal cybersecurity policy to make these protections consistent.
Critical infrastructure. Networked systems are embedded in real-world operations via CPS security and operational technology (OT) security, supporting energy, transport, and manufacturing. When breaches occur, incident response and forensics teams trace the origin and impact so systems can recover and harden.
What’s changing. Emerging areas such as 5G security, quantum-safe encryption, and zero-trust networking are reshaping how we secure communication. Ethical hacking stress-tests systems proactively, while threat intelligence tracks global trends and anticipated risks.
Data & analytics for networks. Digital communication generates huge data streams. Data science & analytics help teams process and interpret them: from data analysis and big-data analytics to data cleaning & preprocessing. Clear data visualization surfaces anomalies and performance issues, while evolving tools & technologies improve monitoring and forecasting.
Ethics & society. Networking intersects with ethics and social issues—privacy, digital rights, equitable access, and misinformation. Sector-specific practice (see domain-specific analytics) ensures decisions make sense in context.
Interactive & real-time media. Principles of digital networking power experiences like game development, where multiplayer requires low latency and resilient servers. Technologies from game engine development pair with real-time APIs and server optimization, while VR/AR demand high-bandwidth links to synchronize spatial data across devices.
AI-driven communication. Modern platforms add intelligence—chatbots and NPCs draw on AI in games and thoughtful narrative design to deliver context-aware experiences. The fusion of cybersecurity, analytics, and interactive media is a rich area for innovation.

This illustration visualizes the scope of networking: core IP routing and switching at the base, wireless access and IoT at the edge, and secured, cloud-scale services tying everything together. Use it as a guide to move from fundamentals to real systems—addressing, VLANs, Wi-Fi, segmentation, and cloud/edge patterns.
Exploring Networking & Telecommunication – From Physical Links to the Cloud
Networking and telecommunication keep the modern digital world connected – from the physical cables and wireless signals that move bits, to the protocols and services that make the internet and cloud platforms work. On Prep4Uni.Online, this hub links foundational ideas such as data transmission, network architectures, and telecommunication standards with applied areas like cloud networking, wireless and mobile communications, and network security. It is designed to help you bridge school-level IT and physics with university courses in computer networks, telecommunications engineering, and internet infrastructure.
Networking & Telecommunication – Overview
Use this page as your entry point into how devices talk to each other. It introduces the layered view of networks, the difference between local and wide-area networks, and the role of standards bodies. From here you can navigate to more detailed pages on data transmission, protocols, management, cloud networking, wireless systems, and the security concerns that arise whenever systems are interconnected.
Telecommunication Systems & Standards
Focuses on how large-scale communication systems are organised and regulated. This subpage looks at telephone networks, mobile networks, fibre and satellite links, and the international standards (such as ITU and 3GPP frameworks) that keep systems interoperable. It helps you see how engineering, policy, and economics meet in the global communications infrastructure.
Data Transmission & Communication Technologies
Explores how bits are physically encoded and transmitted. Topics include analogue vs digital signalling, bandwidth, modulation schemes, error detection and correction, and the trade-offs between speed, reliability, and cost. This page connects school physics (waves, signals, noise) to practical questions in networking and telecom design.
Network Architecture & Protocols
Looks at how networks are structured in layers and how protocols coordinate communication. You will meet ideas like the OSI and TCP/IP models, routing and switching, addressing, and core protocols such as IP, TCP, UDP, and HTTP. This subpage prepares you for more advanced study of internet engineering, routing, and distributed systems.
Network Management & Administration
Covers the practical work of keeping networks running. Topics include configuration, monitoring, performance tuning, fault diagnosis, and documentation. You will see how tools such as SNMP, logging, and dashboards support day-to-day operations, and how good network administration underpins reliability for businesses, campuses, and data centres.
Network Security
Focuses on how to protect data in transit and defend networked systems from attack. This subpage connects to your Cybersecurity hub by looking at firewalls, VPNs, intrusion detection and prevention systems, secure protocols (such as TLS), and common network-level threats. It prepares you for further study in cybersecurity, ethical hacking, and secure system design.
Cloud Networking
Examines how networking changes when services move into the cloud. You will explore virtual networks, load balancing, software-defined networking (SDN), and how connectivity is managed across regions and providers. This page links directly to your Cloud Computing hub and prepares students for roles in cloud architecture and DevOps.
Wireless & Mobile Communications
Looks at Wi-Fi, cellular networks, and other wireless systems that support mobility. Topics include radio propagation, frequency bands, handover, spectrum reuse, and generations of mobile standards from 2G to 5G and beyond. This subpage bridges concepts in physics, signal processing, and network design with real-world applications like smartphones and IoT devices.
Internet & Web Technologies
Connects core networking ideas to the web services users see every day. You will meet domain names and DNS, client–server vs API-driven architectures, HTTP/HTTPS, content delivery networks (CDNs), and basic web performance considerations. This page links networking to software engineering, web development, and cloud-based applications.
Network & Transmission – Emerging Technologies
Highlights new directions in networking and telecommunication, such as software-defined networks, network function virtualisation, 5G and beyond, optical advances, and low-power wide-area networks for IoT. This subpage is especially useful for students curious about where the next wave of infrastructure innovation may come from.
- Networking & Telecommunication topics:
- Overview
- Telecommunication Systems & Standards
- Data Transmission & Communication Technologies
- Network Architecture & Protocols
- Network Management & Administration
- Network Security
- Cloud Networking
- Wireless & Mobile Communications
- Internet & Web Technologies
- Network & Transmission – Emerging Technologies
Table of Contents
Quick start: how a web request travels
When you open a web page, a short chain of network steps happens in milliseconds. Knowing each step tells you where to look when something breaks.
- DNS lookup – your device asks a recursive resolver to find the site’s address and gets an A/AAAA record (IPv4/IPv6).
- TCP handshake – the client opens a connection to the server’s port
443(HTTPS): SYN → SYN-ACK → ACK. - TLS handshake – client and server agree keys; the server presents a certificate; traffic becomes encrypted.
- HTTP request/response – the browser sends
GET /with headers; the server returns a status (200/301/404) and content. - Connection reuse – keep-alive; with HTTP/2 multiple requests are multiplexed on one TLS session.
Key metrics: latency (RTT), throughput, packet loss, and jitter. Most “the internet is slow” issues are one of these.
Interactive: Trace a Web Request
Round 1: Put the steps in order. Round 2: Pick the best place to diagnose each problem. Click Check for instant feedback.
Round 1 — Sequence Builder
Arrange the five steps a request takes across the network.
Round 2 — Troubleshooting Match
Choose where you’d look first to validate or fix each symptom.
- DNS: run
nslookup prep4uni.online(ordig) and note A/AAAA + TTL. - Path:
traceroute prep4uni.online(Windows:tracert) and count hops. - HTTP:
curl -I https://prep4uni.online/to read status + headers. - Browser: DevTools → Network; reload and read the waterfall (DNS, TLS, TTFB).
IP addressing & subnets (CIDR)
IP vs MAC. An IP address identifies devices end-to-end; a MAC address identifies them on the local link. ARP maps IP→MAC on the LAN; routers forward packets between subnets.Private space. Common IPv4 private ranges are10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. Your router does NAT so many private devices share one public IP.- CIDR basics.
/24means 24 network bits.192.168.1.0/24has hosts192.168.1.1–192.168.1.254; the gateway is often.1. - Splitting networks.
192.168.1.0/25yields two subnets:192.168.1.0–127and192.168.1.128–255(126 hosts each). - Default route. Routing tables typically show
0.0.0.0/0 via 192.168.1.1—send everything else to the gateway.
- Find IP/gateway. Windows:
ipconfig; macOS/Linux:ip addr&ip route(look fordefault via). - Same subnet? Are
192.168.1.20/24and192.168.1.130/24the same subnet? (Yes.) With/25? (No—different halves.) - View routes. Windows:
route print; macOS/Linux:netstat -rnorip route. Identify the default route and one connected network.
Switching vs routing
Layer 2 (switching) moves frames inside a LAN using a MAC address table; Layer 3 (routing) moves packets between subnets using a routing table. In practice you’ll use both: switches build the local segments; routers (or L3 switches) connect those segments and the internet.
- Switch essentials. Learns MAC→port from traffic; unknowns are flooded. Broadcast domains can be split with VLANs (802.1Q). Trunks carry multiple VLANs between switches. STP/RSTP prevents loops.
- Router essentials. Chooses next hop by longest-prefix match; needs a default route for “everything else.” Performs inter-VLAN routing and often NAT at the edge. Routes can be static or learned (OSPF, BGP, etc.).
- When to use which. Same subnet = switching; different subnets/VLANs or internet = routing. Campus cores often use L3 switches to route at wire speed.
- Common pitfalls. Layer-2 loops without STP, VLAN not allowed on trunk, wrong default gateway, asymmetric routing through multiple firewalls.
Mini-lab (10 min):
- See neighbors. Windows:
arp -a; macOS/Linux:ip neigh. (These are L2 entries learned by your host.) - Find your default gateway. Windows:
ipconfig; macOS/Linux:ip route(look fordefault via). - Confirm first hop.
traceroute 8.8.8.8(Windows:tracert)—hop 1 should be your gateway. - Bonus (managed switch). On a lab switch:
show mac address-tableto see L2 learning;show spanning-treeto confirm loop protection.
DNS in one page
DNS maps names to data (usually IPs). Your device asks a recursive resolver, which follows referrals to authoritative servers, then caches the answer for its TTL.- Core records. A/AAAA (IPv4/IPv6 address), CNAME (alias to another name), TXT (free-text—SPF/verification), MX (mail exchangers), NS (delegation), SOA (zone info).
- Caching & TTLs. Resolvers cache answers for the TTL; negative caching stores NXDOMAIN briefly. Lower TTLs help during migrations.
- Authority path. Root → TLD (e.g., .online) → your zone’s authoritative nameservers.
dig +traceshows the full walk. - Common gotchas. CNAME cannot coexist with other records at the same name (especially at zone apex); stale caches after changes; mixing private/internal names with public DNS.
- Query basics.
nslookup prep4uni.online(ordig prep4uni.online) and note A/AAAA + TTL. - Other types.
nslookup -type=NS prep4uni.online,nslookup -type=MX prep4uni.online(ordig NS/MX). - Trace authority.
dig +trace prep4uni.onlineto see root → TLD → authoritative responses. - Flush cache. Windows:
ipconfig /flushdns; macOS:sudo dscacheutil -flushcache && sudo killall -HUP mDNSResponder; Linux (systemd):resolvectl flush-caches.
NAT, firewalls & common topologies
NAT lets many private devices share one public IP; firewalls control which flows are allowed. Together they shape how homes, offices and internet-facing apps connect.- NAT in practice. SNAT/PAT changes the source (many-to-one with port translation) for outbound traffic; DNAT/port forwarding maps a public port to an internal host for inbound access. Know hairpin NAT (internal clients reaching a service via its public name) and CGNAT at some ISPs (you don’t truly own the public IP).
- Firewalls 101. Stateful firewalls track connections (reply traffic is allowed); stateless match each packet. Use default-deny inbound, allow only what you need; consider egress rules too. L3/4 rules match IP/port; L7 options (WAF/proxies) understand HTTP/headers.
- Home/SMB network. ISP ONT/Modem → edge router (NAT, DHCP, DNS, firewall) → switch/APs. Use VLANs to segment staff / guest / IoT; avoid double NAT (modem in bridge mode or single router only).
- Site-to-site. Branch ↔ HQ via IPsec VPN (or SSL). Choose full-tunnel (all traffic) vs split-tunnel (only specific subnets). Dynamic routing (e.g., OSPF/BGP) across the tunnel prevents static-route drift.
- Public-facing apps. Anycast DNS → CDN → WAF/LB → app instances. Health checks, blue/green or canary deployments reduce downtime; keep a least-privilege security group on every tier.
- Common pitfalls. Wrong default gateway, missing VLAN on trunks, NAT loopback disabled (services not reachable by public name inside), port forwarding to the wrong host, two WAN links causing asymmetric routing, permissive “allow any” egress rules.
- Your public IP. Visit
https://ifconfig.me(or search “what is my IP”). Compare to your router’s WAN IP. If different, you may be behind CGNAT. - Test NAT & port forward (safe demo). On an internal machine, run a temporary server (e.g.,
python -m http.server 8000). Forward TCP 8000 on the router to that host. From a mobile on 4G/5G, browsehttp://<your-public-ip>:8000. Remove the rule when done. - Firewall sanity. Confirm default-deny inbound. Create one explicit allow (e.g., 8000/tcp) then delete it after the test.
- Draw your topology. Sketch: ISP → Edge router (NAT/VPN) → Switch → VLANs (Staff/Guest/IoT) → APs. Note gateways and allowed flows between VLANs.
Wireless & mobile networking (Wi-Fi/5G)
Wi-Fi connects devices over unlicensed spectrum; cellular (4G/5G) uses licensed spectrum managed by carriers. Good performance comes from clean channels, strong signal-to-noise (SNR), and sensible security.- Bands & channels. 2.4 GHz travels farther but is crowded—use channels 1/6/11. 5 GHz is faster with more channels; 6 GHz (Wi-Fi 6E) adds clean spectrum. Wider channels (40/80 MHz) increase throughput but raise interference risk.
- Signal & roaming. Aim for RSSI ≳ −65 dBm and SNR ≳ 25 dB for smooth video calls. Multiple APs should overlap ~15–20% for roaming; avoid “sticky clients” by tuning power and enabling 802.11k/v/r where supported.
- Security. Prefer WPA3-Personal (or WPA2-Personal if needed). For organizations, use WPA2/3-Enterprise (802.1X) with unique credentials per user/device. Disable WPS; isolate guest SSIDs; segment IoT on its own VLAN.
- Interference. Microwaves/Bluetooth/neighbor APs add noise on 2.4 GHz; DFS radar can force 5 GHz channel changes. Place APs high and away from metal/brick; don’t max transmit power—balanced power reduces co-channel contention.
- Cellular basics. LTE/5G offer high throughput with higher latency variance than wired. Great for backup WAN or mobile sites. Note many carriers use CGNAT (no inbound ports); use a VPN or reverse proxy for remote access.
- Tethering & hotspots. Fine for short tasks; for stable work, use a 5G router with external antennas and position for best RSRP/RSRQ/SINR.
- Survey Wi-Fi. Use a Wi-Fi analyzer (phone/laptop) to view SSIDs, channels, RSSI. If crowded on 2.4 GHz, move your AP to 1/6/11 with 20 MHz width; try 5 GHz for laptops/TVs.
- Gateway latency. Ping your default gateway (e.g., 20–50 packets). Jitter > 10–15 ms suggests interference or weak signal.
- Roam test (multi-AP). Walk between APs while streaming a call; note if the client “sticks.” Enable 802.11k/v/r if available and retest.
- 5G sanity. On mobile data, check “what is my IP.” If it’s private/changes often, you’re behind CGNAT—plan VPN/reverse-proxy for inbound access.
Performance: latency, throughput & loss
Good user experience depends on latency (RTT in ms), throughput (goodput in Mbps, not just link speed), packet loss (%), and jitter (latency variation). MTU/MSS, congestion control, Wi-Fi quality and server distance all shape these.
- Latency. Round-trip time to the first hop (gateway) should be < 2–3 ms on wired, < 10–20 ms on Wi-Fi. Long physical distance and poor radio signal increase RTT.
- Throughput vs bandwidth. A “100 Mbps” link won’t deliver 100 Mbps app throughput if the server is slow, congested, far away, or packets drop. Look at goodput (actual payload rate).
- Loss & jitter. Even 0.5–1% loss can crush TCP throughput; jitter harms real-time apps. Bufferbloat (oversized queues) makes latency spike under load.
- MTU/MSS. A wrong MTU causes fragmentation or black-holed packets (e.g., PMTUD issues through VPNs). Typical Ethernet MTU is 1500; many tunnels use 1400–1472.
- Server & path. Anycast DNS/CDNs bring content closer; poor peering or hot potato routing can add delay. TCP stacks (CUBIC/BBR), TLS handshakes, and app backends also matter.
- Quick wins. Prefer wired for stability; fix Wi-Fi channels/SNR; reduce image sizes and enable compression/caching; place services behind a CDN; right-size queues (SQM/CoDel) to fight bufferbloat.
Mini-lab (10–15 min):
- Baseline RTT. Ping your gateway (e.g., 50 packets):
ping -c 50 <gateway-ip>. Mean < 3 ms wired, < 10–20 ms Wi-Fi; stdev < 5 ms. - Path & loss.
traceroute prep4uni.online(Windows:tracert); look for a big RTT jump or loss on a specific hop. - Throughput. If you control both ends, use
iperf3 -c <server>(and-Rfor reverse). Otherwise compare reputable speed tests on wired vs Wi-Fi. - MTU check. Linux/macOS:
ping -D -s 1472 prep4uni.online(don’t fragment). If it fails, lower size until it passes; add 28 bytes for IP/ICMP headers to estimate MTU. - Web timing. In your browser DevTools → Network, read DNS, TLS, TTFB, content download. Large TTFB = server/app delay; large download = payload size/throughput.
Troubleshooting playbook
Fix issues layer by layer. Change one thing at a time; take notes. Decide quickly if the problem is this device, this network, or the far end.- Link & local checks (L1/L2). Cables seated? Link lights on? Wi-Fi connected with strong RSSI (≥ −65 dBm)? Airplane mode off? Try another port/SSID.
- IP config (L3). Does the host have a valid IP/subnet/gateway/DNS? Windows:
ipconfig /all; macOS/Linux:ip addr&ip route. Renew DHCP if needed. - Gateway reachability. Ping the default gateway. If it fails, the issue is local (cable/Wi-Fi/VLAN). If it works, the local segment is good.
- DNS vs connectivity. Can you ping a public IP (
8.8.8.8)? If yes but names fail, it’s DNS. Checknslookup/digand resolvers. - Routing & path.
traceroute/tracertto the destination. A stall at the edge suggests NAT/firewall or upstream trouble. - Ports & services. Test the service port (e.g.,
curl -v https://site/,telnet host 443, or a simple TCP test). For internal apps, confirm the correct host/IP/port after any changes. - App & server. Check server logs, health checks, certificates (expiry/hostname), and recent deploys. Roll back or restart only with understanding.
- Scope & changes. One user or many? One site or global? What changed: new firmware, rules, cables, routes, certificates, DNS records?
- Document & escalate. Capture screenshots, commands, timestamps, and the smallest failing test. Share topology and exact error text.
- Local vs remote. Ping gateway → ping public IP → resolve & ping a name. Note where it fails; that’s your layer.
- DNS proof.
nslookup prep4uni.onlinewith your default resolver; then try a public one (nslookup prep4uni.online 1.1.1.1). Compare. - HTTP check.
curl -I https://prep4uni.online/should return a 200/301. If handshake fails, inspect TLS/certs and firewall egress. - Wi-Fi vs wired. Repeat a failing test on Ethernet. If Ethernet works, fix Wi-Fi (channel, power, placement) instead of the server.
- Packet capture (advanced). Reproduce once with
Wiresharkortcpdump -i <iface> host <server-ip>; look for DNS failures, SYN retries, or TLS alerts.
See also: DNS in one page, Wireless & mobile, and Network security.
Where networking shows up
- Enterprise IT. Design, segment and monitor campus/WAN networks to keep services up and users safe.
- Cloud Computing. Reliable networking underpins scalable apps—load balancers, VPCs/subnets, VPN/peering.
- Telecom providers. Build and operate carrier networks that deliver voice, data and content at global scale.
- Cybersecurity. Firewalls, IDS/IPS, Zero Trust access, and incident response secure traffic and identities.
- IoT & CPS. Sensor networks and industrial control systems require resilient, low-latency links.
Study paths in networking
Go deeper with these focused guides. Each link covers key ideas, mini-labs, and common pitfalls.
Network architecture & protocols
How networks are structured and how devices agree to talk.
- OSI & TCP/IP layers
- Routing vs switching
- Wireless stacks (802.11/5/6)
Network security
Protecting traffic and identities across segments and the internet.
- TLS/HTTPS, IPsec/VPN
- Firewalls, IDS/IPS, zero-trust
- Keys, certificates, policies
Wireless & mobile
Wi-Fi and cellular technologies for mobility and coverage.
- Wi-Fi 5/6, channels & roaming
- 4G/5G basics
- Bluetooth, NFC
Cloud networking
Virtual networks that tie apps and regions together.
- VPCs/subnets, peering/VPN
- SDN/NFV
- CDNs & edge
Data transmission
Media, modulation and error control for reliable links.
- Fiber vs copper
- QAM/PSK
- CRC, Hamming, Reed–Solomon
Network management
Keeping networks healthy at scale.
- Monitoring & telemetry
- Config & change management
- Fault handling, QoS
Emerging technologies
New capabilities shaping the next decade.
- 5G/6G, edge computing
- Quantum networking
- AI for networks
Telecom systems & standards
Voice/data systems and the standards that govern them.
- PSTN, VoIP
- ITU/IEEE standards
- Broadcast systems
Internet & web technologies
How the web stays fast and reliable.
- DNS, HTTP/2–3
- Caching & content delivery
- IPv6 adoption
Why study networking? It’s the backbone of modern systems. Skills here unlock roles in enterprise IT, cloud, security, telecom and IoT—and help you design, debug and defend real networks.
Architecture & Protocols
OSI / TCP-IP · Routing · Switching
Emerging Tech
5G/6G · Edge · Quantum · AI
Network Security
TLS · VPN · Firewalls · Zero-trust
Network Management
Telemetry · Config · QoS
Wireless & Mobile
Wi-Fi · 4G/5G · Bluetooth/NFC
Internet & Web
DNS · HTTP/2–3 · Caching · IPv6
Cloud Networking
VPC · Peering/VPN · CDNs/Edge
Data Transmission
Fiber/Copper · Modulation · FEC
Networking
study paths
FAQ
What should I learn first in networking?
Start with IP addressing and subnets, then DNS lookups, routing tables, and the HTTP request flow. With those four, most troubleshooting makes sense.
How do I tell if a problem is DNS or connectivity?
Ping your gateway → ping a public IP (8.8.8.8) → resolve a name (nslookup prep4uni.online). If IP works but names fail, it’s DNS.
What’s the difference between switching and routing?
Switching (L2) forwards frames inside a subnet using MAC tables; routing (L3) forwards packets between subnets using a routing table. Inter-VLAN traffic requires routing.
What’s NAT, and when do I need port forwarding?
NAT lets many private hosts share one public IP. Port forwarding (DNAT) maps a public port to an internal host so external clients can reach your service.
What Wi-Fi signal is “good”?
Aim for RSSI ≳ −65 dBm and SNR ≳ 25 dB for calls/video. Prefer 5 GHz with sensible channel width; on 2.4 GHz stick to channels 1/6/11.
My internet feels slow—what should I check first?
Baseline latency to the gateway, channel/SNR on Wi-Fi, packet loss & jitter, MTU/MSS (tunnels/VPNs), and server distance. Wired tests help isolate Wi-Fi issues.
Glossary
- IP address
- Logical address for end-to-end delivery (IPv4/IPv6).
- MAC address
- Link-layer hardware identifier used inside a LAN.
- ARP
- Protocol that maps IP addresses to MAC addresses on a local network.
- CIDR / Subnet
- Notation (e.g., /24) that defines network vs host bits for grouping IPs.
- Default gateway
- The router a host uses to reach non-local networks.
- DNS
- Name system that resolves domains to records (A/AAAA, CNAME, MX, etc.).
- TTL
- Time-to-Live: how long a DNS answer is cached (also a hop limit in IP).
- VLAN
- Virtual LAN that splits a switch into multiple broadcast domains.
- Trunk
- Link that carries multiple VLANs between switches (802.1Q tags).
- STP/RSTP
- Spanning Tree Protocols that prevent Layer-2 loops.
- NAT (SNAT/DNAT)
- Address translation for outbound (SNAT/PAT) and inbound (DNAT/port-forward) traffic.
- MTU / MSS
- Maximum frame/payload sizes; wrong values cause fragmentation or drops.
- Latency & jitter
- Delay (RTT) and its variation; critical for voice/video.
- Throughput / goodput
- Data rate achieved by applications (payload) as opposed to raw link speed.
- Packet loss
- Percentage of packets dropped; even small loss can cripple TCP.
- TLS / HTTPS
- Encryption and authentication for web traffic over TCP.
- TCP vs UDP
- Reliable, connection-oriented vs lightweight, connectionless transports.
Further Reading
- Computer Networks: A Systems Approach (online book) — End-to-end view of the Internet stack, routing, congestion control, and network design.
- Stanford CS144: Intro to Computer Networking (course site) — Lectures, labs, and a hands-on tiny TCP project for practical understanding.
- Beej’s Guide to Network Programming — Practical sockets (TCP/UDP) programming; concepts transferable beyond C.
- RFC 9000 — QUIC: A UDP-Based Multiplexed and Secure Transport — Connection migration, streams, congestion control, and loss recovery.
- RFC 9114 — HTTP/3 — How HTTP runs over QUIC; multiplexing and performance implications.
- Practical Networking: Subnetting & CIDR Guides — Step-by-step IPv4/IPv6 subnetting, VLSM, and route summarization drills.
Frequently Asked Questions about Networking and Telecommunication
What is networking and telecommunication, and why is it important in modern IT systems?
Networking and telecommunication are about connecting computers, devices, and services so that they can exchange data reliably and securely. This includes local networks in homes and offices, wide-area networks across cities and countries, and the global infrastructure of the internet and mobile networks. Modern IT systems depend on networking and telecommunication for everything from cloud services and video conferencing to online banking and streaming, so understanding this area is essential for many technical and business careers.
Do I need strong mathematics and physics to study networking and telecommunication at university?
You do not need to be a specialist in advanced mathematics or physics to begin studying networking and telecommunication, but a comfortable foundation helps. Algebra, basic probability, and logical reasoning are useful for understanding protocols, addressing schemes, and performance analysis. If your programme includes communication theory or wireless systems, you may also encounter more mathematical topics such as signals, bandwidth, and error control. Building confidence with school-level mathematics will make these subjects easier to follow at university.
How is a networking and telecommunication focus different from a general computer science or IT degree?
A general computer science or IT degree covers a broad range of topics such as programming, algorithms, databases, and software engineering. A networking and telecommunication focus goes deeper into how data moves across networks, how routing and switching work, how wireless and mobile systems are designed, and how large-scale communication infrastructures are managed. Many degree programmes allow you to specialise in networking and telecommunication through modules, lab work, and projects that emphasise protocols, network design, and service quality.
What skills should I develop in secondary school if I am interested in networking and telecommunication?
If you are interested in networking and telecommunication, start by building skills in problem-solving, logical thinking, and basic programming. Getting familiar with operating systems, simple command-line tools, and how to configure home routers or Wi-Fi networks can also be helpful. Reading about how the internet works, experimenting with small networks in school labs, and joining technology or robotics clubs will give you early exposure to practical issues like addressing, cabling, and troubleshooting.
What concepts and tools should I know about before starting a networking and telecommunication degree?
Before starting a networking and telecommunication degree, it is helpful to know basic concepts such as IP addresses, routers, switches, Wi-Fi, and client–server communication. You do not need to be an expert, but recognising terms like TCP/IP, DNS, HTTP, and OSI layers will make university material more familiar. Simple tools such as ping, traceroute, and basic router settings are good starting points. Some students also explore entry-level network simulators or virtual labs to visualise how data moves through a network.
How does networking and telecommunication relate to cloud computing and cybersecurity?
Networking and telecommunication are closely linked to both cloud computing and cybersecurity. Cloud services rely on reliable, high-performance networks to connect users to remote data centres, while concepts such as virtual networks, load balancing, and edge computing are built on networking foundations. Cybersecurity depends on understanding how traffic flows, where vulnerabilities may appear, and how to protect data in transit using techniques such as encryption, firewalls, and intrusion detection. Students who understand networking find it easier to specialise in cloud or security later.
What kinds of labs and projects might I encounter in a university networking and telecommunication programme?
In a university networking and telecommunication programme, you can expect labs and projects that involve designing and configuring networks, working with routers and switches, analysing traffic, and troubleshooting performance or reliability problems. You may use physical equipment, virtual machines, or network simulators to build enterprise-style networks, secure wireless setups, or small-scale internet service provider scenarios. Some programmes also include projects on voice over IP, software-defined networking, or 5G and beyond, linking theory to real-world systems.
What university majors and careers can grow from an interest in networking and telecommunication?
An interest in networking and telecommunication can lead to university majors such as computer science, information technology, network engineering, telecommunications engineering, or cybersecurity. Career paths include network administrator, network engineer, systems engineer, telecommunications specialist, infrastructure architect, and security analyst. The same skills are also in demand in cloud operations, data centre management, internet service providers, and organisations that run large corporate or campus networks.
Networking & Telecommunications — Review, Challenges, and Practice
This capstone section consolidates the unit. Start with a quick review,
stretch your thinking with challenge questions, and finish by applying concepts to
worked numerical problems. Use it to check mastery, uncover gaps, and build exam confidence.
What you should be able to do (at a glance)
- Explain key models and mechanics: OSI & TCP/IP, addressing & subnetting,
routing/switching, and wireless fundamentals. - Analyze protocol behavior: DNS, HTTP/2–3/QUIC, TLS,
NAT, DHCP, BGP/OSPF basics. - Reason about performance: latency, throughput, bandwidth–delay product, queueing,
QoS, caching, and CDNs. - Apply security principles: TLS/PKI, VPNs, firewalls, and zero-trust ideas.
- Solve quantitative tasks: prefix math, CIDR, link budgets, utilization, speedup, availability.
How to use this section
- Review Questions & Answers — quick checks on core facts and definitions.
- Thought-Provoking Q&A — “why/what-if” prompts to connect topics and reason about trade-offs.
- Numerical Problems & Solutions — step-by-step worked examples with units and sanity checks.
Networking and Telecommunications: Review Questions and Answers:
1. What is networking and why is it essential in modern telecommunications?
Answer: Networking refers to the interconnection of computers, devices, and systems that allows them to communicate and share resources. It is essential in modern telecommunications because it enables the efficient transfer of data across local and global networks, facilitating communication and information sharing. A robust network infrastructure supports critical applications, including voice, video, and data services, ensuring reliable connectivity. This connectivity is vital for businesses, governments, and individuals to operate efficiently in a digital age.
2. What are the fundamental components of a network infrastructure?
Answer: The fundamental components of a network infrastructure include devices such as routers, switches, firewalls, and servers, along with the cabling and wireless technologies that connect them. These elements work together to manage data traffic, secure the network, and ensure efficient communication between devices. Routers and switches direct data along optimal paths, while firewalls protect the network from unauthorized access. Together, they form the backbone of any communication system, supporting both internal operations and external connectivity.
3. How do communication protocols facilitate data exchange in a network?
Answer: Communication protocols are standardized rules and conventions that govern how data is transmitted and received over a network. They ensure that devices can understand each other’s signals, regardless of the underlying hardware or software differences. Protocols such as TCP/IP, HTTP, and FTP facilitate reliable data exchange by managing error checking, data segmentation, and routing. These protocols are essential for maintaining efficient and secure communication between systems in both local and wide-area networks.
4. What role do routers and switches play in a network infrastructure?
Answer: Routers and switches are critical components in a network infrastructure that manage and direct data traffic. Routers connect different networks, such as a local network to the internet, and determine the best paths for data to travel based on routing protocols. Switches operate within a local network, directing data packets between devices to optimize performance and reduce collisions. Together, these devices ensure that data is efficiently transmitted, maintaining high performance and reliability across the network.
5. How does telecommunication infrastructure support global connectivity?
Answer: Telecommunication infrastructure supports global connectivity through a combination of wired and wireless technologies that link regional networks, data centers, and internet exchange points around the world. This infrastructure includes fiber optic cables, satellite links, cellular networks, and undersea cables that transmit high-speed data over long distances. These interconnected systems allow for seamless communication and data exchange between different geographic regions. Global connectivity is critical for international business, information sharing, and accessing services regardless of location.
6. What is the significance of wireless communication in modern networks?
Answer: Wireless communication is significant in modern networks because it provides the flexibility and mobility required for today’s connected world. It eliminates the need for physical cables, enabling devices to communicate over the air through Wi-Fi, cellular networks, and Bluetooth. This technology is crucial for supporting mobile devices, remote access, and the Internet of Things (IoT), which collectively drive innovation in various sectors. Wireless communication also facilitates rapid deployment and scalability, making it an essential component of modern network infrastructures.
7. How does network security contribute to the reliability of telecommunications?
Answer: Network security contributes to the reliability of telecommunications by protecting data integrity, ensuring privacy, and preventing unauthorized access and cyber attacks. Security measures such as firewalls, encryption, intrusion detection systems, and secure authentication protocols safeguard the network against potential threats. These protections help maintain uninterrupted communication, reduce the risk of data breaches, and ensure that services remain available to users. Effective network security is critical for building trust and ensuring the smooth operation of both private and public networks.
8. What challenges are associated with scaling network infrastructures, and how can they be addressed?
Answer: Scaling network infrastructures involves challenges such as managing increased data traffic, ensuring interoperability between diverse systems, and maintaining performance and security across larger networks. As networks grow, issues like latency, bandwidth limitations, and network congestion can arise, affecting overall performance. To address these challenges, organizations can implement scalable architectures, upgrade hardware, and adopt advanced technologies like software-defined networking (SDN) and network virtualization. These strategies help ensure that networks can expand efficiently while maintaining high levels of performance and security.
9. How do emerging technologies like 5G influence the future of networking and telecommunication?
Answer: Emerging technologies like 5G are set to revolutionize networking and telecommunication by offering significantly higher speeds, lower latency, and increased capacity compared to previous generations. 5G enables more reliable and rapid data transmission, which is essential for supporting the growing number of connected devices and high-bandwidth applications. This advancement facilitates innovations in areas such as smart cities, autonomous vehicles, and the Internet of Things (IoT), creating new opportunities for improved services and enhanced connectivity. As a result, 5G is expected to drive economic growth and transform how people and businesses interact globally.
10. What role does network management and monitoring play in ensuring efficient telecommunications?
Answer: Network management and monitoring play a crucial role in ensuring the efficient operation of telecommunications systems by continuously tracking network performance, identifying issues, and optimizing resource allocation. They involve the use of software tools to monitor traffic, detect anomalies, and provide real-time alerts, which help maintain network reliability and security. Effective management allows for proactive maintenance and rapid troubleshooting, minimizing downtime and improving overall service quality. By keeping a close watch on network operations, organizations can ensure that their systems are running smoothly and efficiently, supporting the demands of modern communication.
Networking and Telecommunications: Thought-Provoking Questions and Answers
1. How will the evolution of software-defined networking (SDN) impact the future scalability and flexibility of global networks?
Answer: The evolution of software-defined networking (SDN) is poised to significantly enhance the scalability and flexibility of global networks by decoupling the control plane from the data plane. This separation allows for centralized management of network resources, enabling rapid configuration changes and more efficient traffic routing. SDN’s dynamic nature means networks can adapt in real time to changing demands, facilitating better load balancing and improved performance across vast infrastructures.
Furthermore, SDN opens up opportunities for network automation and virtualization, which can lead to cost savings and reduced operational complexity. As these systems become more advanced, they will empower organizations to build more resilient and adaptable networks that can seamlessly integrate new technologies, ultimately driving innovation in global telecommunications.
2. What are the potential security challenges in modern telecommunications networks, and how might emerging technologies address them?
Answer: Modern telecommunications networks face significant security challenges, including increased vulnerability to cyber-attacks, data breaches, and sophisticated phishing or malware campaigns. As networks become more interconnected and complex, traditional security measures may struggle to keep pace with evolving threats. Emerging technologies such as artificial intelligence (AI) and machine learning can enhance threat detection by analyzing patterns and identifying anomalies in real time, allowing for quicker responses to potential breaches.
Additionally, advancements in encryption technologies and blockchain can improve data integrity and secure transactions across networks. By integrating these technologies into network management systems, organizations can build more robust defenses against cyber threats, ensuring that telecommunications infrastructures remain secure and reliable in the face of increasingly sophisticated attacks.
3. How might the implementation of 5G technology transform network infrastructure and user experiences on a global scale?
Answer: The implementation of 5G technology is set to transform network infrastructure by offering unprecedented data speeds, lower latency, and greater connectivity density. This advancement will facilitate seamless communication, enhance the performance of mobile applications, and support the exponential growth of IoT devices across various industries. With faster data transfer and improved network responsiveness, 5G will enable innovative applications such as remote surgery, autonomous vehicles, and smart cities, dramatically altering user experiences worldwide.
On a global scale, 5G has the potential to bridge the digital divide by providing high-speed connectivity to underserved areas. This widespread access can lead to improved economic opportunities, better education, and enhanced public services. As 5G networks become more prevalent, they will redefine the capabilities of modern telecommunications and drive a new era of digital transformation.
4. In what ways can network monitoring and management tools drive proactive maintenance and reduce downtime in large-scale networks?
Answer: Network monitoring and management tools drive proactive maintenance by continuously tracking performance metrics, identifying potential issues, and providing real-time alerts that allow administrators to address problems before they escalate. These tools utilize advanced analytics to predict failures and optimize resource allocation, which helps in scheduling maintenance during off-peak hours to minimize disruptions. By automating these processes, organizations can significantly reduce network downtime, ensuring that critical services remain available and reliable.
Proactive monitoring also supports faster troubleshooting and efficient incident response, as detailed logs and performance data enable quicker diagnosis of issues. This leads to enhanced network stability and better overall performance, ultimately reducing the long-term costs associated with downtime and maintenance. Such systems are indispensable for managing the complexities of modern telecommunications infrastructures.
5. What are the key factors influencing the design of secure and efficient network architectures in the digital age?
Answer: Key factors influencing the design of secure and efficient network architectures include scalability, reliability, and security. In the digital age, networks must support an ever-growing number of connected devices and handle vast amounts of data while maintaining performance and security. Architectural designs need to incorporate advanced encryption, robust access controls, and continuous monitoring to protect against cyber threats. Scalability ensures that networks can expand seamlessly, and reliability guarantees consistent performance under heavy load.
Additionally, emerging technologies such as SDN, NFV (Network Functions Virtualization), and cloud computing are reshaping network design by providing flexible and adaptive solutions that meet modern demands. These innovations enable organizations to build resilient networks that are capable of supporting complex digital ecosystems and ensuring uninterrupted service in a rapidly evolving technological landscape.
6. How might the convergence of telecommunications and networking technologies drive the evolution of smart cities?
Answer: The convergence of telecommunications and networking technologies is a critical driver for the evolution of smart cities by enabling seamless connectivity, data sharing, and real-time communication between various urban systems. This integration supports the deployment of IoT devices, smart sensors, and automated infrastructure that together enhance public safety, transportation, and energy management. As cities become more connected, data-driven insights allow for optimized resource allocation and improved quality of life for residents.
Smart city initiatives rely on robust and secure networks to manage the flow of information and support services ranging from traffic control to emergency response systems. The continuous exchange of data across municipal services fosters innovation and efficiency, ultimately transforming urban environments into more sustainable, resilient, and livable communities. This transformation is a key aspect of modern urban planning and digital transformation initiatives worldwide.
7. What impact does network latency have on communication systems, and how can improvements in technology mitigate these effects?
Answer: Network latency, the delay between data transmission and reception, significantly impacts the performance of communication systems by affecting the speed and responsiveness of data exchanges. High latency can lead to delays in real-time applications such as voice, video conferencing, and online gaming, reducing overall user satisfaction. Improvements in technology, such as faster fiber optics, optimized routing algorithms, and edge computing, can mitigate latency by reducing the physical and processing delays involved in data transmission.
By implementing these advanced solutions, networks can achieve lower latency, resulting in smoother and more reliable communication. This not only enhances user experience but also supports critical applications that depend on real-time data processing, thereby driving efficiency and productivity across various sectors.
8. How can emerging trends in network virtualization contribute to the flexibility and scalability of modern telecommunication networks?
Answer: Emerging trends in network virtualization, including software-defined networking (SDN) and network functions virtualization (NFV), contribute significantly to the flexibility and scalability of modern telecommunication networks. These technologies allow network administrators to manage, configure, and optimize network resources through software rather than relying solely on hardware. This abstraction enables rapid deployment of new services and dynamic resource allocation, making it easier to scale networks to meet increasing demand.
Virtualization also enhances network agility, as virtual networks can be reconfigured on the fly to adapt to changing traffic patterns or to respond to emerging threats. The resulting improvements in efficiency, cost savings, and operational flexibility are key to supporting the ever-evolving needs of global telecommunications.
9. What role do regulatory and compliance standards play in shaping modern networking and telecommunication infrastructures?
Answer: Regulatory and compliance standards play a critical role in shaping modern networking and telecommunication infrastructures by ensuring that systems are secure, reliable, and accessible to all users. These standards set benchmarks for data protection, privacy, and service quality, guiding the design and implementation of network systems. Compliance with regulations such as GDPR, FCC, and other international standards is essential for maintaining public trust and avoiding legal penalties.
By adhering to these standards, organizations are compelled to invest in advanced security measures and robust network management practices. This regulatory oversight drives continuous innovation and improvement within the industry, ensuring that telecommunication infrastructures are capable of meeting the challenges of a rapidly evolving digital landscape.
10. How can the integration of next-generation networking technologies improve disaster recovery and network resilience?
Answer: Next-generation networking technologies, such as SDN, cloud-based infrastructures, and advanced routing protocols, can significantly improve disaster recovery and network resilience by enabling rapid reconfiguration and automated failover processes. These technologies allow for real-time monitoring and dynamic response to network failures, ensuring that data traffic is quickly rerouted to avoid downtime. Enhanced redundancy, load balancing, and distributed architectures also contribute to a more robust network that can withstand unexpected disruptions.
By integrating these advanced solutions, organizations can minimize downtime and maintain critical communications during emergencies. This improved resilience not only safeguards business operations but also enhances overall network reliability, contributing to better service continuity and user satisfaction during adverse events.
11. How might the rise of the Internet of Things (IoT) affect the design and operation of telecommunication networks?
Answer: The rise of the Internet of Things (IoT) is dramatically affecting the design and operation of telecommunication networks by significantly increasing the number of connected devices and the volume of data transmitted. IoT requires networks to be highly scalable, low-latency, and capable of handling diverse data types and protocols. This evolution necessitates more robust network architectures, enhanced security measures, and efficient data management strategies to ensure reliable connectivity for millions of devices.
As IoT continues to expand, telecommunication networks must evolve to support real-time data processing and edge computing, ensuring that devices can communicate seamlessly and efficiently. This transformation not only drives innovation in smart cities and industrial automation but also poses new challenges in terms of network congestion, data privacy, and energy consumption, which must be addressed to maintain optimal performance.
12. How can network analytics and monitoring tools improve the management of telecommunication systems in large-scale networks?
Answer: Network analytics and monitoring tools improve the management of telecommunication systems by providing real-time visibility into network performance, traffic patterns, and potential bottlenecks. These tools enable administrators to detect anomalies, predict failures, and optimize resource allocation before issues escalate into major disruptions. By continuously monitoring key performance metrics, organizations can make informed decisions that enhance network efficiency and reliability.
Additionally, advanced analytics tools facilitate proactive maintenance and rapid troubleshooting, reducing downtime and ensuring high-quality service delivery. The integration of these tools into network management processes drives operational excellence, allowing large-scale networks to adapt dynamically to changing conditions and maintain robust performance.
Networking and Telecommunications: Numerical Problems and Solutions:
1. A network transmits data at 100 Mbps. Calculate the total data transmitted in one hour in gigabytes, then in 24 hours, and finally the average data transmitted per minute.
Solution:
• Step 1: Data per second = 100 Mbps = 100 × 10^6 bits per second.
• Step 2: Data per hour = 100 × 10^6 × 3600 = 360 × 10^9 bits. Convert to GB: 360 × 10^9 ÷ (8 × 10^9) = 45 GB.
• Step 3: Per 24 hours = 45 GB × 24 = 1,080 GB; average per minute = 1,080 GB ÷ (24×60) = 1,080 ÷ 1,440 = 0.75 GB per minute.
2. A router processes 1,200 packets per second. Calculate the number of packets processed per minute, then per hour, and finally per day (24 hours).
Solution:
• Step 1: Packets per minute = 1,200 × 60 = 72,000 packets.
• Step 2: Packets per hour = 72,000 × 60 = 4,320,000 packets.
• Step 3: Packets per day = 4,320,000 × 24 = 103,680,000 packets.
3. A telecommunication link has a bandwidth of 50 Mbps. If the link operates for 8 hours, calculate the total data transmitted in gigabytes, then determine the average data rate in MB per minute.
Solution:
• Step 1: Data per second = 50 Mbps = 50 × 10^6 bits.
• Step 2: Data in 8 hours = 50 × 10^6 × 8 × 3600 = 1.44 × 10^12 bits. Convert to GB: 1.44 × 10^12 ÷ (8 × 10^9) = 180 GB.
• Step 3: Average data per minute = 180 GB ÷ (8×60) = 180 ÷ 480 = 0.375 GB/min, which equals 375 MB/min.
4. A fiber optic cable has a latency of 5 ms per 100 km. Calculate the latency for 450 km, then for 1,000 km, and determine the difference in latency between the two distances.
Solution:
• Step 1: Latency per km = 5 ms ÷ 100 = 0.05 ms/km.
• Step 2: For 450 km = 450 × 0.05 = 22.5 ms; for 1,000 km = 1,000 × 0.05 = 50 ms.
• Step 3: Difference = 50 – 22.5 = 27.5 ms.
5. A network experiences a packet loss rate of 0.1%. If 1,000,000 packets are transmitted, calculate the number of lost packets and the success rate percentage.
Solution:
• Step 1: Lost packets = 1,000,000 × 0.001 = 1,000 packets.
• Step 2: Success rate = 1,000,000 – 1,000 = 999,000 packets transmitted successfully.
• Step 3: Success percentage = (999,000 ÷ 1,000,000) × 100 = 99.9%.
6. A wireless access point transmits at 300 Mbps. Calculate the total data transmitted in 10 minutes in megabytes.
Solution:
• Step 1: Data per second = 300 Mbps = 300 × 10^6 bits.
• Step 2: Data in 10 minutes = 300 × 10^6 × 600 = 180 × 10^9 bits.
• Step 3: Convert to MB: 180 × 10^9 ÷ (8 × 10^6) = 22,500 MB.
7. A telecommunications company allocates $2,000,000 for network infrastructure upgrades. If the upgrade reduces operational downtime costs by 40% and originally downtime costs were $500,000 annually, calculate the new downtime cost and the annual savings.
Solution:
• Step 1: New downtime cost = $500,000 × (1 – 0.40) = $500,000 × 0.60 = $300,000.
• Step 2: Annual savings = $500,000 – $300,000 = $200,000.
• Step 3: This represents a 40% reduction in downtime costs.
8. A router logs 250,000 events per hour. Calculate the total number of events logged in a day, then in a week, and finally the average events per minute over the week.
Solution:
• Step 1: Daily events = 250,000 × 24 = 6,000,000 events.
• Step 2: Weekly events = 6,000,000 × 7 = 42,000,000 events.
• Step 3: Average per minute = 42,000,000 ÷ (7×24×60) = 42,000,000 ÷ 10,080 ≈ 4,166.67 events per minute.
9. A network upgrade increases bandwidth from 100 Mbps to 150 Mbps. Calculate the percentage increase in bandwidth, then determine the additional data transmitted per second, and finally compute the additional data transmitted in one hour (in GB).
Solution:
• Step 1: Percentage increase = ((150 – 100) ÷ 100) × 100 = 50%.
• Step 2: Additional data per second = (150 – 100) Mbps = 50 Mbps = 50 × 10^6 bits.
• Step 3: In one hour = 50 × 10^6 × 3600 = 180 × 10^9 bits; convert to GB: 180 × 10^9 ÷ (8 × 10^9) = 22.5 GB.
10. A network’s latency is measured at 15 ms on average. If an optimization reduces latency by 20%, calculate the new latency, the absolute reduction in latency, and the percentage reduction.
Solution:
• Step 1: New latency = 15 × (1 – 0.20) = 15 × 0.80 = 12 ms.
• Step 2: Absolute reduction = 15 – 12 = 3 ms.
• Step 3: Percentage reduction = (3 ÷ 15) × 100 = 20%.
11. A telecommunication provider serves 10,000 subscribers, each using 2 GB of data per month. Calculate the total monthly data usage, then for a year, and finally the average data usage per subscriber per year.
Solution:
• Step 1: Monthly usage = 10,000 × 2 GB = 20,000 GB.
• Step 2: Annual usage = 20,000 × 12 = 240,000 GB.
• Step 3: Average per subscriber per year = 240,000 ÷ 10,000 = 24 GB.
12. A network monitoring system processes 500,000 logs per day. If 0.2% of these logs indicate critical issues, calculate the number of critical logs per day, then per month (30 days), and finally the percentage of critical logs relative to total logs.
Solution:
• Step 1: Critical logs per day = 500,000 × 0.002 = 1,000 logs.
• Step 2: Critical logs per month = 1,000 × 30 = 30,000 logs.
• Step 3: Percentage of critical logs = (1,000 ÷ 500,000) × 100 = 0.2%.
Last updated:
