Cybersecurity Awareness and Training Education is the art of shaping tiny decisions—because tiny decisions scale. The diagram shows how awareness becomes habit. Learners bring in inputs such as basic digital familiarity and structured materials, but their learning is steered by controls: organizational rules, policy requirements, and clear expectations about what must never be done and what must always be checked. Mechanisms like guided instruction and training platforms provide repetition with realism—scenarios, examples, and practice that mirror everyday moments: an unexpected message, a suspicious link, a request for credentials, a “quick” workaround that feels convenient. The output is not technical wizardry; it is steady judgment. Learners begin to recognize social engineering cues, handle information more carefully, and respond consistently under pressure—so security becomes part of routine conduct rather than a poster on the wall.
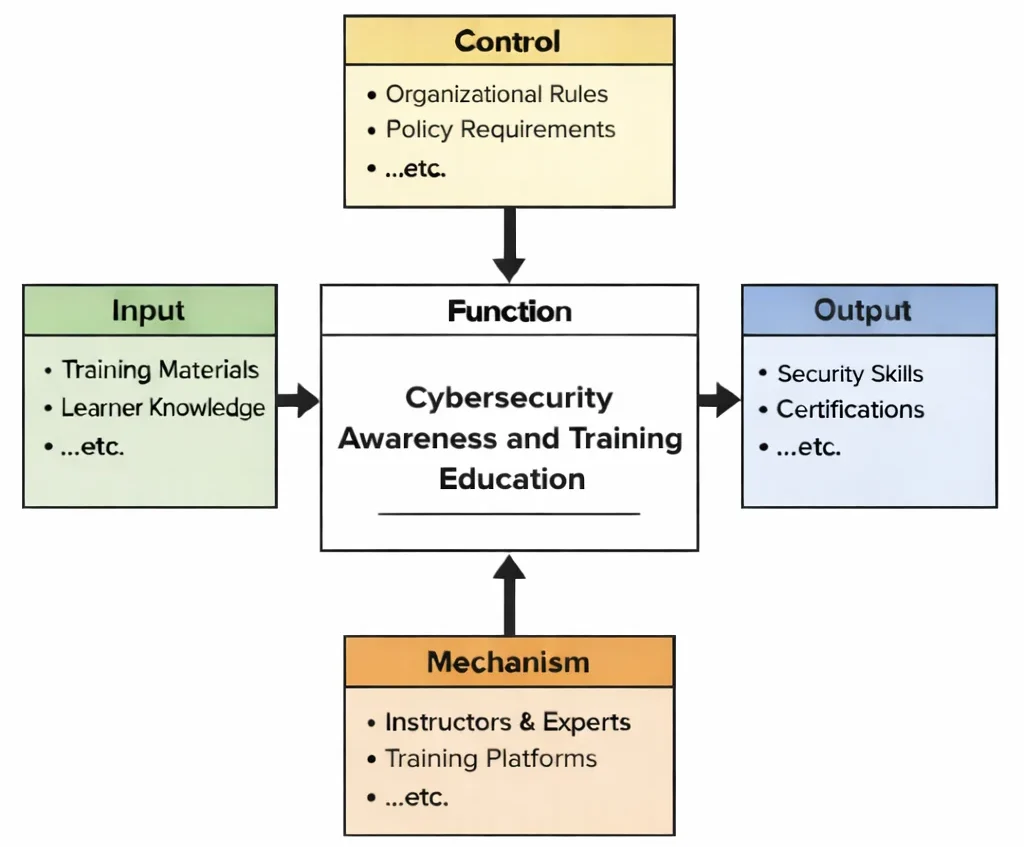
This IDEF0 (Input–Control–Output–Mechanism) diagram summarizes Cybersecurity Awareness and Training Education as a structured transformation. Inputs include training materials and learner baseline knowledge of common digital habits. Controls include organizational rules, policy requirements, and required behaviors that define what “secure conduct” looks like in daily work and study. Mechanisms include instructors, experts, training platforms, and practice activities (such as scenarios and simulations) that reinforce correct responses. Outputs include improved security skills, safer day-to-day behavior, and readiness for assessments or role-based certifications.
Cybersecurity awareness and training focus on equipping individuals and organizations with the knowledge and skills needed to identify, prevent, and respond to cyber threats. Since human error is one of the leading causes of cybersecurity incidents, creating a culture of security through education and awareness is crucial for minimizing risks.

This image visualizes cybersecurity awareness as a shared, human-centered responsibility. Learners sit at computer desks in a training-room setting while a luminous globe with a central padlock hovers above a digital platform, suggesting that modern security protects systems worldwide—and depends on informed users everywhere. The surrounding symbols (shields, alerts, network icons, and authentication imagery) represent common topics covered in training: safe passwords, phishing recognition, secure Wi-Fi use, data protection, and incident reporting. The composition emphasizes that good security is not only about tools and software, but also about habits, judgment, and teamwork—building a security-minded culture through education and practice.
What is cybersecurity awareness, and why does it matter for everyday users?
Cybersecurity awareness is the understanding of common digital risks and the everyday behaviours that help protect devices, data, and online identities. It matters because most cyber incidents start with human error, such as clicking a malicious link, reusing weak passwords, or oversharing information on social media. By recognising warning signs, applying basic security practices, and staying informed about new threats, everyday users can greatly reduce the chance of falling victim to phishing, fraud, and account compromise in both personal and professional settings.
What are the most common online threats that students and professionals should know about?
Common online threats include phishing emails and messages that trick users into revealing passwords or financial information, malware that can steal or destroy data, and ransomware that encrypts files and demands payment. Other frequent risks are identity theft, social engineering via phone or messaging apps, unsafe public Wi-Fi usage, and data leaks from weak passwords or misconfigured cloud accounts. Students and professionals who recognise these patterns and verify unexpected requests before acting are far better prepared to protect themselves and their organisations from avoidable incidents.
How can strong passwords and multi-factor authentication improve my security?
Strong passwords that are long, unique, and hard to guess make it significantly more difficult for attackers to break into accounts using guessing, credential stuffing, or brute-force attacks. Using a password manager helps you generate and store different complex passwords for every site so that one breach does not endanger all your logins. Enabling multi-factor authentication (MFA) adds an additional layer, such as a one-time code or an authentication app, so that even if your password is stolen, attackers cannot easily access your account without the second factor.
How can I recognise a phishing email or suspicious message?
Phishing emails and messages often create urgency or fear, asking you to click a link, open an attachment, or share sensitive details to avoid a problem or claim a reward. Warning signs include unfamiliar senders, spelling or grammar errors, mismatched web addresses, unusual payment requests, and links that do not match the organisation’s official domain when you hover over them. A good habit is to verify unexpected requests through a trusted channel, such as logging in directly via a known website or contacting the organisation using a phone number or email address you find independently, rather than replying or clicking immediately.
What safe habits should I practise when using public Wi-Fi and shared devices?
When using public Wi-Fi, you should avoid accessing sensitive accounts such as banking or work systems unless you use a virtual private network (VPN) to encrypt your traffic. Always check that websites use HTTPS, log out of accounts after use, and disable automatic Wi-Fi connection to unknown networks. On shared computers or devices, never save passwords in the browser, clear browsing data when finished, and avoid downloading personal files or work documents that might be left behind for the next user to see or copy.
Why are software updates and backups important for cybersecurity awareness?
Software updates often include security patches that fix vulnerabilities which attackers actively exploit, so delaying updates leaves devices open to known attacks. Keeping operating systems, browsers, apps, and security tools up to date is one of the simplest and most effective protective measures. Regular backups, stored offline or in a secure cloud service, ensure that you can recover important data after ransomware, hardware failure, or accidental deletion, turning a potential crisis into a manageable inconvenience rather than a disaster.
How does social media behaviour affect my personal and professional cybersecurity?
Social media posts can reveal personal information such as birthdays, locations, travel plans, and workplace details that attackers use to guess passwords, answer security questions, or tailor convincing phishing messages. Oversharing about projects, colleagues, or internal systems can unintentionally expose an organisation’s structure and technologies, making targeted attacks easier. Practising cybersecurity awareness means reviewing privacy settings, limiting public information, and thinking carefully before posting details that could be combined to impersonate you or gain access to your accounts or employer’s systems.
How does learning cybersecurity awareness prepare me for future study and careers?
Learning cybersecurity awareness builds habits and vocabulary that are valuable across computing, engineering, business, and any role that handles data or digital systems. It helps you understand how technical controls, policies, and human behaviour interact, which is a core theme in university courses on information security, risk management, and digital ethics. Employers increasingly expect graduates to recognise basic security issues, follow good practices, and contribute to a security-conscious culture, so early awareness can differentiate you in internships, projects, and long-term career pathways in both technical and non-technical fields.
Table of Contents
Key Topics in Cybersecurity Awareness and Training
Recognizing Phishing and Social Engineering Attacks:
- Phishing:
- Educating users about identifying deceptive emails or messages designed to steal sensitive information.
- Recognizing common signs such as:
- Misspelled email addresses or domains.
- Urgent requests for personal information.
- Suspicious attachments or links.
- Social Engineering:
- Training individuals to recognize psychological manipulation tactics used by attackers to gain unauthorized access.
- Examples include pretexting, baiting, and tailgating.
- Phishing:
Secure Password Practices:
- Educating users on the importance of strong, unique passwords to protect their accounts.
- Best practices include:
- Using long passwords with a mix of letters, numbers, and symbols.
- Avoiding predictable patterns like “123456” or “password.”
- Regularly updating passwords and avoiding reuse across platforms.
- Encouraging the use of password managers to generate and store complex passwords securely.
Regular Security Awareness Campaigns:
- Conducting periodic campaigns to reinforce good cybersecurity habits.
- Methods include:
- Simulated phishing tests to evaluate user awareness.
- Interactive quizzes and games to make learning engaging.
- Publishing security newsletters with tips and updates on recent threats.
Understanding Security Policies:
- Training employees to adhere to organizational security policies.
- Topics may include acceptable use policies, data handling procedures, and incident reporting protocols.
Safe Internet Practices:
- Avoiding public Wi-Fi for sensitive tasks unless using a VPN.
- Being cautious when downloading files or accessing websites.
Device Security:
- Securing personal and organizational devices through:
- Enabling automatic updates.
- Installing antivirus and antimalware software.
- Locking devices when unattended.
- Securing personal and organizational devices through:
Applications of Cybersecurity Awareness and Training
Reducing Susceptibility to Phishing Attacks:
- Training users to identify phishing emails and avoid clicking malicious links reduces the likelihood of data breaches.
- Example: Organizations conducting phishing simulations to measure and improve employee readiness.
Building a Culture of Security Within Organizations:
- Promoting security as a shared responsibility fosters vigilance across all levels of an organization.
- Regular discussions, workshops, and leadership support help normalize secure behavior.
Improving Incident Response Readiness:
- Educating employees about recognizing and reporting suspicious activities ensures quicker detection and response.
- Example: Training helpdesk staff to identify social engineering attempts targeting organizational systems.
Enhancing Compliance:
- Ensuring employees are aware of regulatory requirements like GDPR, HIPAA, or PCI-DSS reduces the risk of non-compliance penalties.
Mitigating Insider Threats:
- Awareness programs can reduce unintentional insider threats by teaching employees about data handling and proper security protocols.
Protecting Remote Workers:
- Training remote employees on securing home networks, using VPNs, and avoiding risky behaviors like sharing devices.
Tools and Methods for Cybersecurity Awareness and Training
E-Learning Platforms:
- Platforms like KnowBe4, Cybrary, and Coursera offer cybersecurity awareness training modules tailored for various industries.
- Example Topics:
- Identifying phishing emails.
- Understanding ransomware.
Simulated Attack Scenarios:
- Tools like PhishMe and Barracuda PhishLine simulate phishing attacks to test and train employees in a controlled environment.
Interactive Workshops and Seminars:
- Conducting in-person or virtual sessions led by cybersecurity experts.
- Topics: Recent cyber threats, best practices, and organizational security policies.
Gamification:
- Using games and challenges to engage employees in learning cybersecurity concepts.
- Example: Cybersecurity escape rooms or quizzes on recognizing phishing attempts.
Policy Awareness Programs:
- Distributing accessible guides and reminders on key security policies.
- Example: Posters near workstations encouraging password hygiene and reporting suspicious activities.
Benefits of Cybersecurity Awareness and Training
Minimizing Human-Related Vulnerabilities:
- Reduces the likelihood of employees falling victim to phishing or social engineering.
- Promotes proactive behavior like reporting potential threats.
Cost Savings:
- Prevents costly breaches and downtime by mitigating risks through early detection.
Boosting Employee Confidence:
- Empowering employees with knowledge fosters confidence in managing potential threats.
Enhancing Organizational Reputation:
- Demonstrating a commitment to security builds trust with customers, clients, and partners.
Supporting Digital Transformation:
- Ensures secure adoption and use of new technologies.
Challenges in Cybersecurity Awareness and Training
Maintaining Engagement:
Repetitive or overly technical training can lead to disengagement. Tailoring content to the audience is essential.
Keeping Up with Emerging Threats:
Regularly updating training materials to reflect the latest cyber threats and trends.
Measuring Effectiveness:
Tracking metrics like phishing simulation success rates or incident reporting frequency to gauge training impact.
Why Study Cybersecurity Awareness
Recognizing That Everyone Plays a Role in Security
Understanding Common Threats and How to Prevent Them
Building Strong Digital Hygiene Habits Early
Preparing for University Life and a Digital Academic Environment
Supporting Career Readiness and Workplace Security Culture
Cybersecurity Awareness – Frequently Asked Questions
These FAQs highlight everyday digital risks, practical protection habits, and how cybersecurity awareness supports your studies and future career.
What is cybersecurity awareness, and why does it matter for everyday users?
Cybersecurity awareness is the understanding of common digital risks and the everyday behaviours that help protect devices, data, and online identities. It matters because most cyber incidents start with human error, such as clicking a malicious link, reusing weak passwords, or oversharing information on social media. By recognising warning signs, applying basic security practices, and staying informed about new threats, everyday users can greatly reduce the chance of falling victim to phishing, fraud, and account compromise in both personal and professional settings.
What are the most common online threats that students and professionals should know about?
Common online threats include phishing emails and messages that trick users into revealing passwords or financial information, malware that can steal or destroy data, and ransomware that encrypts files and demands payment. Other frequent risks are identity theft, social engineering via phone or messaging apps, unsafe public Wi-Fi usage, and data leaks from weak passwords or misconfigured cloud accounts. Students and professionals who recognise these patterns and verify unexpected requests before acting are far better prepared to protect themselves and their organisations from avoidable incidents.
How can strong passwords and multi-factor authentication improve my security?
Strong passwords that are long, unique, and hard to guess make it significantly more difficult for attackers to break into accounts using guessing, credential stuffing, or brute-force attacks. Using a password manager helps you generate and store different complex passwords for every site so that one breach does not endanger all your logins. Enabling multi-factor authentication (MFA) adds an additional layer, such as a one-time code or an authentication app, so that even if your password is stolen, attackers cannot easily access your account without the second factor.
How can I recognise a phishing email or suspicious message?
Phishing emails and messages often create urgency or fear, asking you to click a link, open an attachment, or share sensitive details to avoid a problem or claim a reward. Warning signs include unfamiliar senders, spelling or grammar errors, mismatched web addresses, unusual payment requests, and links that do not match the organisation’s official domain when you hover over them. A good habit is to verify unexpected requests through a trusted channel, such as logging in directly via a known website or contacting the organisation using a phone number or email address you find independently, rather than replying or clicking immediately.
What safe habits should I practise when using public Wi-Fi and shared devices?
When using public Wi-Fi, you should avoid accessing sensitive accounts such as banking or work systems unless you use a virtual private network (VPN) to encrypt your traffic. Always check that websites use HTTPS, log out of accounts after use, and disable automatic Wi-Fi connection to unknown networks. On shared computers or devices, never save passwords in the browser, clear browsing data when finished, and avoid downloading personal files or work documents that might be left behind for the next user to see or copy.
Why are software updates and backups important for cybersecurity awareness?
Software updates often include security patches that fix vulnerabilities which attackers actively exploit, so delaying updates leaves devices open to known attacks. Keeping operating systems, browsers, apps, and security tools up to date is one of the simplest and most effective protective measures. Regular backups, stored offline or in a secure cloud service, ensure that you can recover important data after ransomware, hardware failure, or accidental deletion, turning a potential crisis into a manageable inconvenience rather than a disaster.
How does social media behaviour affect my personal and professional cybersecurity?
Social media posts can reveal personal information such as birthdays, locations, travel plans, and workplace details that attackers use to guess passwords, answer security questions, or tailor convincing phishing messages. Oversharing about projects, colleagues, or internal systems can unintentionally expose an organisation’s structure and technologies, making targeted attacks easier. Practising cybersecurity awareness means reviewing privacy settings, limiting public information, and thinking carefully before posting details that could be combined to impersonate you or gain access to your accounts or employer’s systems.
How does learning cybersecurity awareness prepare me for future study and careers?
Learning cybersecurity awareness builds habits and vocabulary that are valuable across computing, engineering, business, and any role that handles data or digital systems. It helps you understand how technical controls, policies, and human behaviour interact, which is a core theme in university courses on information security, risk management, and digital ethics. Employers increasingly expect graduates to recognise basic security issues, follow good practices, and contribute to a security-conscious culture, so early awareness can differentiate you in internships, projects, and long-term career pathways in both technical and non-technical fields.
Cybersecurity Awareness and Training: Conclusion
Cybersecurity awareness and training are vital for reducing human-related vulnerabilities and strengthening an organization’s overall security posture. Regular, engaging, and up-to-date training ensures that employees and individuals remain vigilant and informed about evolving cyber threats.
Cybersecurity Awareness and Training: Review Questions and Answers:
1. What is cybersecurity awareness and why is it essential for organizations?
Answer: Cybersecurity awareness refers to the understanding and knowledge employees have about cyber threats and safe online practices. It is essential because it helps prevent security breaches by equipping staff with the skills to identify and respond to potential risks. When employees are aware of the latest phishing tactics, social engineering schemes, and malware threats, they become the first line of defense against cyber attacks. Moreover, a strong awareness culture reduces overall risk and supports the implementation of robust security policies throughout the organization.
2. How do phishing simulations contribute to effective cybersecurity awareness?
Answer: Phishing simulations are practical exercises designed to test and improve employees’ ability to recognize and respond to fraudulent emails. They provide real-world scenarios that help identify common vulnerabilities and areas where additional training is needed. By measuring response rates and tracking improvements over time, organizations can gauge the effectiveness of their awareness programs. These simulations not only educate staff on what to look for in suspicious communications but also reinforce best practices for email security and reporting potential threats.
3. What are some common social engineering tactics highlighted in cybersecurity awareness programs?
Answer: Cybersecurity awareness programs often emphasize social engineering tactics such as phishing, pretexting, baiting, and tailgating. These tactics exploit human psychology rather than technical vulnerabilities to gain unauthorized access to sensitive information. Employees are taught to verify requests for confidential data, be cautious of unsolicited communications, and follow established protocols for reporting suspicious behavior. By understanding these tactics, individuals can better protect themselves and the organization from manipulation and data breaches.
4. How does regular cybersecurity awareness training impact an organization’s overall security posture?
Answer: Regular cybersecurity awareness training significantly strengthens an organization’s security posture by continually updating employees on emerging threats and best practices. It fosters a culture of vigilance where every employee plays an active role in safeguarding digital assets. This training helps reduce the likelihood of human error, which is a common cause of security incidents. Furthermore, ongoing education ensures that staff remain informed about new attack vectors and mitigation techniques, leading to a proactive and resilient defense strategy.
5. Why is employee behavior considered a critical factor in cybersecurity defense?
Answer: Employee behavior is considered a critical factor because humans are often the weakest link in an organization’s cybersecurity chain. Even the most advanced technical defenses can be undermined by careless actions, such as clicking on suspicious links or sharing sensitive information inadvertently. Cybersecurity awareness programs aim to transform employee behavior by promoting secure practices and a culture of responsibility. When employees are well-informed and cautious, they can detect and prevent potential threats before they escalate into significant security breaches.
6. How can organizations measure the effectiveness of their cybersecurity awareness training programs?
Answer: Organizations can measure the effectiveness of their training programs by tracking metrics such as phishing simulation click rates, incident reports, and employee feedback before and after training sessions. These metrics provide quantitative data on improvements in security behavior and awareness levels. Regular assessments, surveys, and simulated attacks help identify areas of strength and weaknesses, enabling continuous improvement. In addition, benchmarking against industry standards can offer insights into how well the training program is performing relative to similar organizations.
7. What role do digital communications and social media play in cybersecurity awareness?
Answer: Digital communications and social media are critical channels for disseminating cybersecurity awareness information and updates. They allow organizations to reach a broad audience quickly with the latest threat intelligence, best practices, and training materials. Social media platforms can also be used to simulate phishing attacks and monitor public awareness trends. By leveraging these tools, companies can engage employees in ongoing discussions about cybersecurity, reinforce training concepts, and create a community dedicated to digital safety.
8. How does cybersecurity awareness training help in mitigating the risks of data breaches?
Answer: Cybersecurity awareness training mitigates the risks of data breaches by educating employees on how to recognize and avoid common cyber threats. This training emphasizes the importance of secure passwords, cautious email handling, and proper data storage practices, all of which are crucial in preventing unauthorized access. When employees understand the potential consequences of a data breach, they are more likely to adhere to security protocols and report suspicious activity promptly. Overall, informed employees serve as an effective barrier against cybercriminals attempting to exploit human error.
9. What are the long-term benefits of establishing a strong cybersecurity awareness culture within an organization?
Answer: Establishing a strong cybersecurity awareness culture yields long-term benefits such as reduced incident rates, lower financial losses, and improved compliance with regulatory standards. A culture of awareness leads to continuous vigilance, proactive threat identification, and quicker responses to potential security issues. This not only safeguards the organization’s assets but also enhances its reputation among clients and partners. Over time, the cumulative effect of informed and responsible behavior significantly strengthens the overall resilience of the organization against cyber threats.
10. How do cybersecurity awareness initiatives integrate with broader IT security strategies?
Answer: Cybersecurity awareness initiatives are an integral component of broader IT security strategies because they address the human element of cybersecurity. These initiatives complement technical defenses by ensuring that employees are informed about risks and the importance of following security protocols. When awareness training is aligned with IT policies and incident response plans, it creates a cohesive defense mechanism that covers both technological and human vulnerabilities. As a result, organizations can achieve a more comprehensive and effective security posture that adapts to evolving cyber threats.
Cybersecurity Awareness and Training: Thought-Provoking Questions and Answers
1. How might evolving cyber threats reshape the future of cybersecurity awareness training?
Answer: The continuous evolution of cyber threats, including increasingly sophisticated phishing scams, ransomware attacks, and social engineering tactics, necessitates an adaptive approach to cybersecurity awareness training. As attackers develop more advanced methods to exploit human vulnerabilities, training programs must evolve to cover emerging threat vectors and provide practical, up-to-date strategies for prevention. This evolution may involve integrating real-time threat intelligence, interactive simulations, and continuous learning modules that keep pace with the changing landscape.
The future of cybersecurity awareness training will likely see greater personalization, with programs tailored to different roles within an organization. This specialization ensures that employees receive training relevant to their specific risk profiles and job functions. Additionally, advancements in technology such as virtual reality and gamification could make training more engaging and effective, ultimately reducing the likelihood of successful cyber attacks.
2. What impact does the rise of remote work have on cybersecurity awareness and employee behavior?
Answer: The shift to remote work has fundamentally altered the cybersecurity landscape by expanding the attack surface beyond the traditional office environment. Employees working remotely often use personal devices and unsecured networks, increasing the potential for cyber threats. This new reality requires enhanced cybersecurity awareness training that focuses on secure home network practices, safe remote access protocols, and the importance of using VPNs and multi-factor authentication.
Furthermore, remote work necessitates a cultural shift in how employees perceive cybersecurity risks, as the boundaries between personal and professional environments blur. Organizations must invest in continuous education and provide clear guidelines to ensure that remote workers maintain the same level of security vigilance as those in the office. By fostering a robust cybersecurity culture among remote employees, companies can significantly reduce the risk of breaches that exploit the vulnerabilities inherent in dispersed workforces.
3. How can organizations balance the need for robust cybersecurity awareness with the risk of overwhelming employees with information?
Answer: Striking a balance between comprehensive cybersecurity training and avoiding information overload is a critical challenge for organizations. One effective strategy is to break down training content into manageable, focused modules that address specific topics, allowing employees to absorb and retain key concepts gradually. Regular, short training sessions and interactive exercises can be more engaging than lengthy, one-time seminars, ensuring that critical information is reinforced over time without overwhelming the audience.
Moreover, organizations can tailor the training to the needs of different departments and roles, ensuring that each employee receives relevant and actionable information. Feedback mechanisms, such as quizzes and surveys, can help assess comprehension and adjust the training material accordingly. By adopting a modular, targeted approach, companies can build a robust cybersecurity awareness program that educates without overburdening employees.
4. In what ways can gamification enhance the effectiveness of cybersecurity awareness training?
Answer: Gamification incorporates game-design elements into cybersecurity training to create an interactive and engaging learning experience. By introducing elements such as points, leaderboards, and rewards, gamification motivates employees to participate actively in training activities and reinforces positive security behaviors. This approach not only makes learning more enjoyable but also enhances retention of critical information by encouraging friendly competition and regular participation.
Furthermore, gamified training can simulate real-world cyber threats in a controlled environment, allowing employees to practice their responses in a risk-free setting. This hands-on experience builds confidence and competence, making it more likely that employees will apply what they have learned in actual scenarios. As a result, gamification can lead to a more resilient and proactive cybersecurity culture within the organization.
5. How can emerging technologies like artificial intelligence be integrated into cybersecurity awareness programs?
Answer: Emerging technologies such as artificial intelligence (AI) can play a transformative role in enhancing cybersecurity awareness programs by providing personalized learning experiences and real-time threat simulations. AI-powered platforms can analyze employee performance data to identify knowledge gaps and customize training content to address individual needs. This targeted approach ensures that each employee receives relevant instruction based on their risk profile and learning pace, thereby increasing the overall effectiveness of the training.
In addition, AI can facilitate the creation of realistic threat simulations that adapt to current cyber trends. These simulations can mimic sophisticated cyber attacks, providing employees with hands-on experience in recognizing and responding to real-world threats. By leveraging AI, organizations can create dynamic training environments that continuously evolve to meet the challenges of modern cybersecurity, ultimately fostering a more proactive and informed workforce.
6. What are the long-term benefits of cultivating a strong cybersecurity culture within an organization?
Answer: Cultivating a strong cybersecurity culture yields long-term benefits that extend far beyond immediate risk reduction. A robust culture of cybersecurity awareness instills best practices and fosters a proactive mindset among employees, reducing the likelihood of breaches and enhancing overall resilience. Over time, this culture can lead to improved incident response times, better compliance with regulatory standards, and reduced financial losses due to cyber attacks. The ongoing commitment to security becomes embedded in the organization’s operations, driving continuous improvement and innovation.
Moreover, a strong cybersecurity culture enhances trust among customers, partners, and stakeholders by demonstrating a commitment to protecting sensitive information. This reputation can provide a competitive advantage in the market, as clients increasingly prioritize security when choosing vendors and service providers. Ultimately, investing in cybersecurity awareness leads to a more secure, agile, and successful organization over the long term.
7. How does the human factor contribute to cybersecurity vulnerabilities, and what measures can be taken to address this risk?
Answer: The human factor is a major contributor to cybersecurity vulnerabilities because employees can unintentionally make mistakes that expose systems to threats. Actions such as using weak passwords, clicking on suspicious links, or neglecting software updates can create opportunities for attackers to infiltrate an organization’s defenses. Addressing this risk requires comprehensive cybersecurity awareness training that emphasizes the importance of secure practices and the potential consequences of human error. By educating employees on common threats and best practices, organizations can significantly reduce the likelihood of breaches caused by human factors.
Additionally, implementing policies such as multi-factor authentication, regular security audits, and strict access controls further mitigates the risk posed by human error. Creating an environment where employees feel comfortable reporting potential security issues without fear of retribution also encourages proactive behavior. By focusing on both education and robust security policies, organizations can effectively address the human element of cybersecurity.
8. In what ways can international collaboration enhance global cybersecurity awareness and resilience?
Answer: International collaboration can significantly enhance global cybersecurity awareness by facilitating the sharing of threat intelligence, best practices, and emerging trends across borders. When organizations and governments work together, they can pool resources and expertise to develop more effective training programs and security protocols. This collaboration fosters a unified approach to combating cyber threats, ensuring that all stakeholders are better prepared to address sophisticated attacks. By exchanging information and experiences, countries can learn from one another and implement more resilient cybersecurity measures.
Moreover, international partnerships can lead to the development of standardized frameworks and guidelines that improve the consistency of cybersecurity practices worldwide. This harmonization of standards not only makes it easier for multinational organizations to manage security risks but also strengthens the global defense against cyber criminals. As cyber threats continue to evolve, collaboration on an international scale will be crucial for maintaining a secure and stable digital environment.
9. How do digital communication channels influence the perception of cybersecurity threats among employees?
Answer: Digital communication channels, such as email, social media, and instant messaging, play a significant role in shaping employees’ perceptions of cybersecurity threats. These channels are often the primary means by which threat alerts, training updates, and security best practices are communicated within an organization. When used effectively, they can raise awareness, foster a sense of urgency, and encourage proactive behavior among employees. However, if communication is inconsistent or overly technical, it can lead to confusion, complacency, or even fear, undermining the overall effectiveness of the cybersecurity awareness program.
Clear and engaging communication is therefore essential to ensure that employees understand the relevance and importance of cybersecurity measures. Organizations can use a mix of visual aids, real-life examples, and interactive content to convey messages effectively. By tailoring communication to different audiences and keeping the information accessible, companies can enhance employee understanding and create a more security-conscious work environment.
10. What ethical considerations arise when enforcing cybersecurity awareness in the workplace?
Answer: Enforcing cybersecurity awareness in the workplace raises several ethical considerations, including privacy concerns and the balance between monitoring and trust. On one hand, organizations need to monitor employee behavior to ensure compliance with security policies and to detect potential breaches. On the other hand, excessive surveillance or intrusive measures can infringe on employees’ privacy and create a culture of mistrust. It is essential to establish clear policies that outline the scope and purpose of monitoring while ensuring that employees are aware of and consent to these practices.
Ethical enforcement of cybersecurity awareness involves transparency, accountability, and respect for individual rights. Organizations must ensure that monitoring practices are proportionate, justified, and aligned with legal standards. By fostering open dialogue and involving employees in the development of security policies, companies can strike a balance between safeguarding assets and maintaining a respectful, trust-based workplace culture.
11. How can crisis simulation exercises enhance cybersecurity awareness and preparedness?
Answer: Crisis simulation exercises are a powerful tool for enhancing cybersecurity awareness by providing employees with realistic scenarios that test their ability to respond to cyber incidents. These exercises simulate various types of attacks, such as phishing campaigns or ransomware incidents, allowing employees to practice their responses in a controlled environment. By engaging in these simulations, staff learn to identify early warning signs, follow incident response protocols, and collaborate effectively under pressure. The hands-on experience gained through simulations not only reinforces theoretical training but also builds confidence in handling real-world cyber threats.
Additionally, crisis simulations help organizations identify weaknesses in their existing policies and procedures, enabling them to make necessary adjustments before an actual incident occurs. The insights gained from these exercises inform future training and drive continuous improvement in the organization’s security posture. As a result, employees become more adept at managing crises, reducing the overall risk and impact of cyber incidents.
12. What strategies can be implemented to ensure cybersecurity awareness training remains current with evolving threats?
Answer: To keep cybersecurity awareness training current, organizations must adopt a dynamic approach that involves continuous updates and regular review of training materials. This can include integrating real-time threat intelligence feeds, updating case studies with recent incidents, and incorporating feedback from previous training sessions. By staying abreast of the latest cyber threats and attack vectors, training programs can be adjusted to address new challenges as they arise. Such proactive measures ensure that employees are always equipped with the most relevant and effective security practices.
Moreover, organizations can partner with industry experts and leverage advanced technologies like AI to analyze emerging trends and tailor training content accordingly. Regular audits and assessments of training efficacy also help identify areas for improvement. Through these strategies, companies can maintain a robust and responsive cybersecurity awareness program that evolves in step with the rapidly changing threat landscape.
Cybersecurity Awareness and Training: Numerical Problems and Solutions:
1. If an organization with 500 employees conducts a phishing simulation where 20% of employees click on the malicious link, calculate the number of employees affected. Then, if a follow-up training reduces this click rate by 50%, determine how many employees will still click on a phishing email. Finally, compute the overall percentage reduction.
Solution:
• First, calculate the initial number of employees affected: 500 × 20% = 100 employees.
• Next, after training, the click rate is reduced by 50%, so the new number of affected employees = 100 × 50% = 50 employees.
• Finally, the overall percentage reduction = ((100 – 50) ÷ 100) × 100 = 50% reduction.
2. A cybersecurity awareness program costs $25 per employee. For an organization of 600 employees, determine the total training cost. If the program reduces phishing-related breaches (costing $5,000 each) by 80% on an expected rate of 10 breaches per year, calculate the annual savings and the ROI for the training cost.
Solution:
• Total training cost = 600 × $25 = $15,000.
• Expected annual breach cost without training = 10 × $5,000 = $50,000.
• Savings after an 80% reduction = $50,000 × 80% = $40,000; ROI = (($40,000 – $15,000) ÷ $15,000) × 100 = 166.67%.
3. In a cybersecurity survey, 50% of 500 employees initially feel confident in identifying phishing emails. After training, 70% feel confident. Calculate the number of employees before and after training, then determine the percentage increase in confident employees.
Solution:
• Initially, 500 × 50% = 250 employees feel confident.
• After training, 500 × 70% = 350 employees feel confident.
• Increase = 350 – 250 = 100 employees; percentage increase = (100 ÷ 250) × 100 = 40%.
4. A phishing simulation campaign is conducted weekly, starting with a 20% click rate. If the rate decreases by 2 percentage points each week, determine the number of weeks required for the click rate to fall below 5%.
Solution:
• Weekly rate after n weeks = 20% – 2% × (n – 1).
• Set 20 – 2(n – 1) < 5 → 20 – 2n + 2 < 5 → 22 – 2n < 5 → 2n > 17 → n > 8.5.
• Thus, it will take 9 weeks for the click rate to fall below 5%.
5. If the average incident response time decreases from 60 minutes to 30 minutes after training, and the cost of downtime is $100 per minute, calculate the cost saving per incident. Then, determine the total annual savings if 50 incidents occur per year.
Solution:
• Time saved per incident = 60 – 30 = 30 minutes; cost saving per incident = 30 × $100 = $3,000.
• Annual savings = 50 × $3,000 = $150,000.
6. Before training, employees have a 30% probability of falling for phishing scams. After training, the probability drops to 10%. For a group of 100 employees, calculate the expected number of incidents before and after training, and the percentage reduction.
Solution:
• Before training: 100 × 30% = 30 incidents; after training: 100 × 10% = 10 incidents.
• Reduction = 30 – 10 = 20 incidents; percentage reduction = (20 ÷ 30) × 100 ≈ 66.67%.
7. A security awareness session lasts 2 hours with an employee cost of $40 per hour. Calculate the training cost per employee. If training increases productivity by 1% on an annual salary of $50,000, compute the monetary value of the productivity gain per employee and the net benefit.
Solution:
• Training cost per employee = 2 × $40 = $80.
• Productivity gain = 1% of $50,000 = $500; net benefit = $500 – $80 = $420 per employee.
8. A company sends 1,000 cybersecurity newsletters monthly. With an open rate of 35% and a click-through rate of 10% of the open emails, calculate the number of clicks. If each click prevents a breach worth $2,000, determine the total preventive value.
Solution:
• Opens = 1,000 × 35% = 350; clicks = 350 × 10% = 35.
• Preventive value = 35 × $2,000 = $70,000.
9. During a cybersecurity awareness month, reported phishing attempts increase by 150% from the previous month’s 40 reports. Calculate the new total number of reported attempts and the absolute increase.
Solution:
• Increase = 40 × 150% = 60; new total = 40 + 60 = 100 reported attempts.
• Absolute increase = 60 attempts.
10. An untrained employee has a 25% chance of clicking a phishing email, while training reduces this risk to 5%. Calculate the relative risk reduction.
Solution:
• Relative risk reduction = ((25% – 5%) ÷ 25%) × 100 = (20% ÷ 25%) × 100 = 80% reduction.
11. In a simulation, 1 out of every 20 emails is a phishing email. If an employee receives 200 emails per day, calculate the number of phishing emails received. Then, if the click rate drops from 15% to 3% after training, determine the expected number of clicks before and after training.
Solution:
• Phishing emails per day = 200 ÷ 20 = 10.
• Before training: 10 × 15% = 1.5 clicks; after training: 10 × 3% = 0.3 clicks.
12. If a cybersecurity program increases the reporting rate of suspicious emails from 5% to 20% among 800 employees, calculate the number of reports before and after training, and the absolute increase.
Solution:
• Before training: 800 × 5% = 40 reports; after training: 800 × 20% = 160 reports.
• Absolute increase = 160 – 40 = 120 reports.
